For security reasons we recommend to create a simple authentication account , which can read LDAP entries but is not able to login to any service provided.
Creating a LDAP search user via the LDAP directory module
Open the Univention Management Console via a webbrowser of your choice with the FQDN or the ip address of your server, like ucs.example.com. After the login please click on the module Domain , to get an overview of all modules in this category. Your site should look like the following picture.
Click on the module LDAP directory to see all the container of your directory.
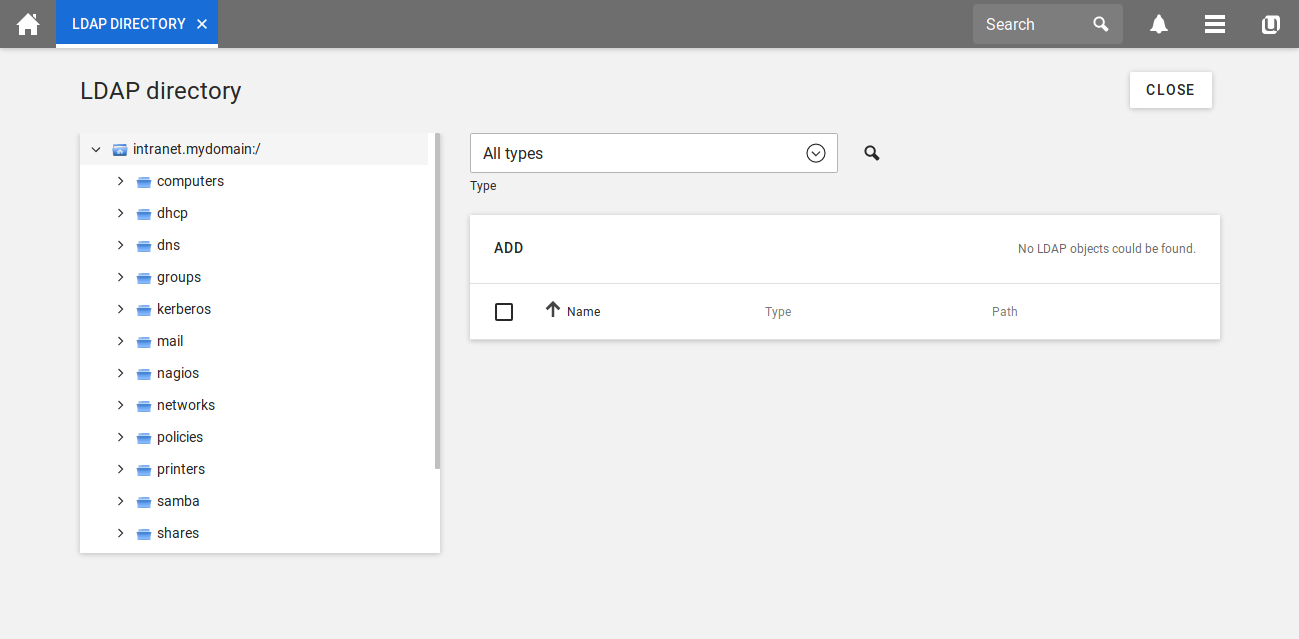
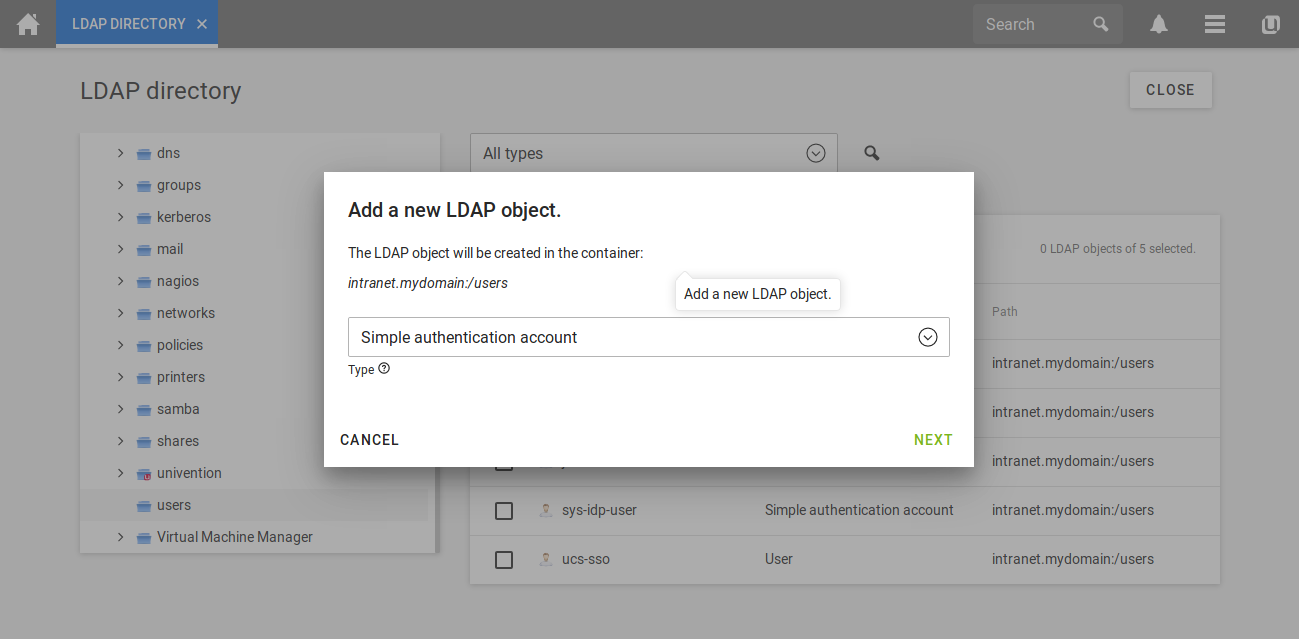
In the menu on the left, you can click on users to open the corresponding container. By clicking on add on the left side of the page you can add a new LDAP object. Please select simple authentication account (german: Einfaches Authentisierungskonto) in the drop down menu as the object you want to create.
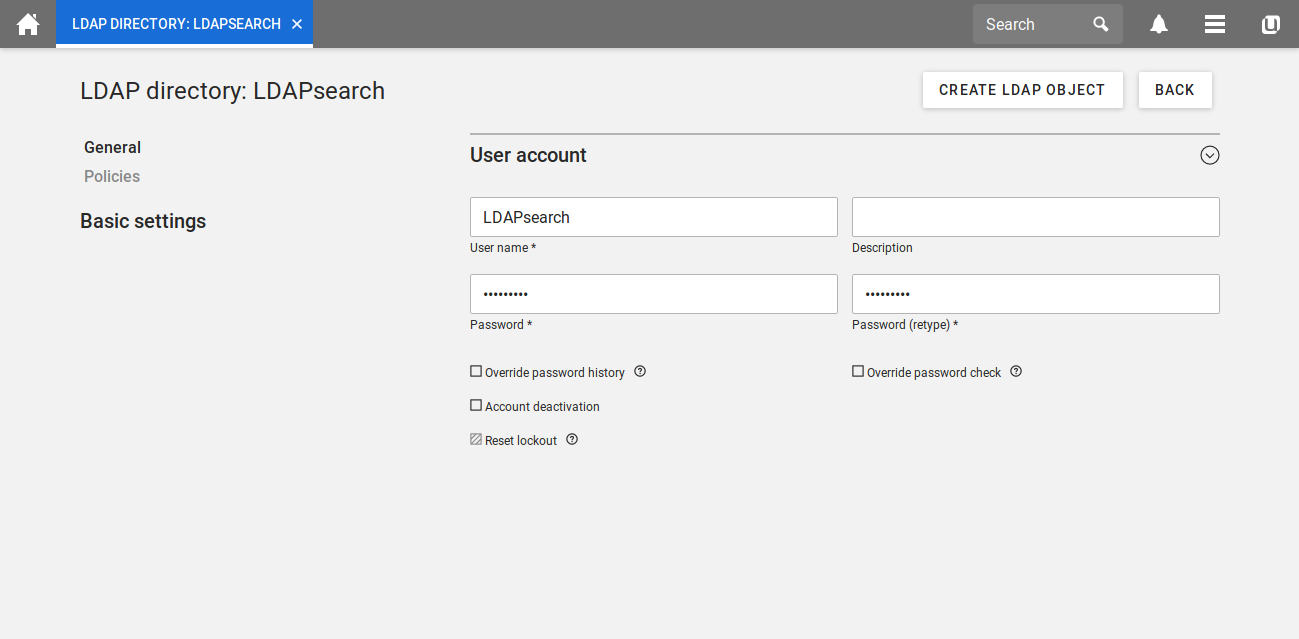
In a last step you can name the account and assign a password to it. Once you clicked on create LDAP object your LDAP search user is ready to be used.
Test commands
With the following shell command you can check if the created user is able to read the LDAP entries:
ldapsearch -x -D uid=<LDAP user>,cn=users,$(/usr/sbin/ucr get ldap/base) -W uid=Administrator
and enter the password of the LDAP search user. If you can see the Administrator’s user object the search user is configured correctly and can be used in services to query the LDAP.
LDAP attributes and values
| Attribute | Further Names | Values | Explanation |
|---|---|---|---|
| LDAP hostname | serveradress | <ip of the server> or <FQDN of the server> | To get the FQDN, run hostname -f on the UCS DC Master |
| LDAP port | 7389, or 7636 for SSL | If the app Active Directory-compatible Domain Controller is installed, the ports 389 and 636 are reserverd for Samba/AD | |
| LDAP method | plain | ||
| LDAP URL | ldaps://example.com:636 | The LDAP-URL containing the protocol (ldaps), server address (e.g. example.com) and port (636 or 7636) | |
| LDAP base | To get the LDAP base from your domain, run ucr get ldap/base on any UCS system. | ||
| LDAP search base | In normal cases it can just be the LDAP base (see Attribute LDAP base). For really huge LDAPs it make sense to narrow the search base down. | ||
| LDAP uid | adminDN | uid | The attribute “uid” contains the username for the LDAP search user. A user which has the authorization to access the LDAP. |
| LDAP password | adminPassword | <password of your LDAP search user> | |
| LDAP user filter | objectClass=organizationalPerson | Only users matching the filter are found using the LDAP filter. Can be expaneded. | |
| LDAP teacher filter (UCS@school) | objectClass=ucsschoolTeacher | Only teachers are found. Can be expanded. | |
| LDAP students filter (UCS@school) | objectClass=ucsschoolStudents | Only students are found. Can be expanded. | |
| LDAP search filter | uid={{username}} | Helpful for third party applications to authenticate to the LDAP. | |
| User DN (UCS) | cn=users,<LDAP base> | Default LDAP path to where the users are stored. | |
| User DN (UCS@school) | <LDAP base> | In normal cases it can just be the LDAP base (see Attribute LDAP base). For really huge LDAPs it make sense to narrow the search base down. | |
| User DN specific school (UCS@school) | cn=users,ou=schoolXY,<LDAP base> | Default LDAP path to where the users of one specific school are stored. | |
| Teacher DN specific school (UCS@school) | cn=lehrer,cn=users,ou=schoolXY,<LDAP base> | Default LDAP path to where the teachers of one specific school are stored. | |
| Students DN specific school (UCS@school) | cn=schueler,cn=users,ou=schoolXY,<LDAP base> | Default LDAP path to where the students of one specific school are stored. | |
| Group DN (UCS) | cn=groups,<LDAP base> | Default LDAP path to where the groups are stored. | |
| Group DN (UCS@school) | <LDAP base> | In normal cases it can just be the LDAP base (see Attribute LDAP base). For really huge LDAPs it make sense to narrow the search base down. | |
| Group DN specific school (UCS@school) | cn=groups,ou=schoolXY,<LDAP base> | Default LDAP path to where the groups of one specific school are stored. | |
| Class DN specific school (UCS@school) | cn=klassen,cn=schueler,cn=groups,ou=schoolXY,<LDAP base> | Default LDAP path to where the class of one specific school are stored. | |
| Workgroup DN specific school (UCS@school) | cn=schueler,cn=groups,ou=schoolXY,<LDAP base> | Default LDAP path to where the workgroups of one specific school are stored. Caution it is a superset of Class DN. So probably if you search recursively in the container you will get workgroups and classes. | |
| Group filter | objectClass=univentionGroup | Only groups matching the filter are found using the LDAP filter. Can be expaneded. | |
| Group attribute | cn | Attribute the group name is stored in the LDAP. |
UCS@school directory structure
The structure is a LDAP tree and the hierarchy looks like this for all UCS@school installations:
- LDAP-Basis (dc=demo,dc= intranet)
- demoschule1 (ou)
- users (cn)
- lehrer (cn)
- teacher1 (cn)
- objectClass: ucsschoolTeacher
- ucsschoolRole: teacher:school:demoschule1
- …
- teacher2
- objectClass: ucsschoolTeacher
- …
- …
- teacher1 (cn)
- schueler (cn)
- student1
- objectClass: ucsschoolStudent
- ucsschoolRole: student:school:demoschule1
- student2
- objectClass: ucsschoolStudent
- …
- …
- student1
- lehrer (cn)
- users (cn)
- demoschule2 (ou)
- demoschule3 (ou)
- …
The path to a teacher entry is called DN and would be for example:
uid=teacher1,cn=lehrer,cn=users,ou= demoschule1,dc= demo,dc= intranet
- demoschule1 (ou)
You can get group memberships with the following filters:
Search filter: “(uid={{username}})” memberOf
Then you get a list of the user’s group memberships.
This list always contains at least one “school group” (Domain Users demoschule1) and one role group (lehrer-demoschule1 or schueler-demoschule1).
Class and workgroup memberships are also obtained this way. Since the class names in LDAP must be unique across schools, the classes and workgroups contain a prefix of the school. For example “demoschule1-1A”.
Troubleshooting
Possible error messages may appear:
> (ldap) Authentication failure! invalid_credentials encountered.
Solution: Check, with the following command, if your bind user (LDAP search user) has the needed access rights to search through the LDAP entries.
univention-ldapsearch -D <DN of your user> -W
If you receive no error message, re-check the configuration of the LDAP plugin. Otherwise, try to work through these wiki article again.
Another error message could be:
> (ldap) Authentication failure! ldap_error: Net::LDAP::Error, Connection reset by peer - SSL_connect
Solution: This error message can have several causes. One of the common reason is that the port number has been set incorrectly.
- LDAP Port: 7389
- LDAP Port (SSL): 7636