We will now connect Moodle with our UCS Identity Provider using Single-Sign-On (SSO) and the SAML (Security Assertion Markup Language) Protocol. Moodle will be able to create and map all it’s users based on all the enabled ones inside our LDAP context(s).
This article is based on a successful installation of Moodle accomplished by following our Cool Solution “Install Moodle”.
Prerequisites
We will first have to download and extract the SAML2 Single-Sign-On plugin. You can use the following script to download the last tested version 2019022100. You might find and use newer plugin versions on the linked Moodle website.
tmpdir=$(mktemp -d) # A temporary working directory
# Download the Plugin and extract it
wget --show-progress -O $tmpdir/moodle-auth_saml2-2019022100.tgz https://github.com/catalyst/moodle-auth_saml2/archive/2019022100.tar.gz
tar -xvzf $tmpdir/moodle-auth_saml2-2019022100.tgz -C /var/www/moodle/auth/
# Set the correct folder and file permissions (This might take a few seconds)
mv /var/www/moodle/auth/moodle-auth_saml2-2019022100 /var/www/moodle/auth/saml2
chown -R www-data:www-data /var/www/moodle/auth/saml2
find /var/www/moodle/auth/saml2/ -type f -exec chmod 640 {} \;
find /var/www/moodle/auth/saml2/ -type d -exec chmod 750 {} \;
# Remove the temporary working directory again
rm -R $tmpdir
Moodle will now require an upgrade of its database. This can quickly be done by opening the service in a webbrowser (might take a while):
https://<server>/moodle
As last prerequisite, the SAML2 Plugin should be activated inside the web configuration site Site Administration → Plugins → Authentication → Manage authentication. Please confirm that the LDAP server Plugin is disabled. We don’t recommend having both authentication services enabled.
Now the SAML connection can be configured. You can either use the webbrowser or use the command line as described below.
SAML identity provider configuration from the Command Line
Use the following script to automatically configure the SAML2 service provider through the command line. You can optionally use your web browser further down:
(Note: Don’t forget to set the variables on the script top first)
This part has to be executed on your UCS SAML IdP server (usually your Master) to create a SAML service provider and additionally enable a few attributes, which can then be accessed by Moodle.
moodle_server_fqdn="slave1.cool-solutions.intranet" # The fully qualified domain name (FQDN) of your Moodle server
moodle_web_address="https://slave1.cool-solutions.intranet/moodle" # Please set the direct web address to moodle here. It should be the same address you used during the Moodle installation and should also start with the https protocol
# Enable a few attributes, that can later be accessed by Moodle
shopt -s nocasematch
eval "$(ucr --shell search saml/idp/ldap/get_attributes)"
temp_saml_idp_ldap_get_attributes="$saml_idp_ldap_get_attributes"
for attribute in 'uid' 'mailprimaryAddress' 'enabledServiceProviderIdentifier' 'c' 'departmentNumber' 'description' 'givenName' 'l' 'mobile' 'o' 'sn' 'street' 'telephoneNumber' 'uidNumber'; do
if [[ ! $saml_idp_ldap_get_attributes =~ [\'\"]$attribute[\'\"] ]]; then
temp_saml_idp_ldap_get_attributes+=" ,'$attribute'"
fi
done
ucr set saml/idp/ldap/get_attributes="$temp_saml_idp_ldap_get_attributes"
# Create a SAML identity provider for Moodle. This will allow Moodle to send login requests and receive the set attributes to map them to the automatically created users
udm saml/serviceprovider create --position cn=saml-serviceprovider,cn=univention,$(ucr get ldap/base) \
--set Identifier="$moodle_web_address/auth/saml2/sp/metadata.php" \
--set AssertionConsumerService="$moodle_web_address/auth/saml2/sp/saml2-acs.php/$moodle_server_fqdn" \
--set singleLogoutService="$moodle_web_address/auth/saml2/sp/saml2-logout.php/$moodle_server_fqdn" \
--set isActivated=TRUE \
--set simplesamlAttributes=TRUE \
--set simplesamlNameIDAttribute=uid \
--append LDAPattributes=c \
--append LDAPattributes=departmentNumber \
--append LDAPattributes=description \
--append LDAPattributes=givenName \
--append LDAPattributes=l \
--append LDAPattributes=mailPrimaryAddress \
--append LDAPattributes=mobile \
--append LDAPattributes=o \
--append LDAPattributes=sn \
--append LDAPattributes=street \
--append LDAPattributes=telephoneNumber \
--append LDAPattributes=uid \
--append LDAPattributes=uidNumber
Alternative: SAML identity provider configuration using the web browser
As first part, we will have to create a new external service provider. We can follow the official UCS Documentation for this.
A few attributes have to be appended to an UCR variable on your UCS SAML server. This later allows Moodle to access the data when it automatically creates a new user. The Univention Management Console system module Univention Configuration Registry can be used for this.
Assure that the UCR variable “saml/idp/ldap/get_attributes” contains the following attributes:
‘uid’, ‘mailPrimaryAddress’, ‘enabledServiceProviderIdentifier’, ‘c’, ‘departmentNumber’, ‘description’, ‘givenName’, ‘l’, ‘mobile’, ‘o’, ‘sn’, ‘street’, ‘telephoneNumber’, ‘uidNumber’
After setting the UCR variable, use the following settings while using the Univention Management Console domain module SAML identity provider to create a new service provider:
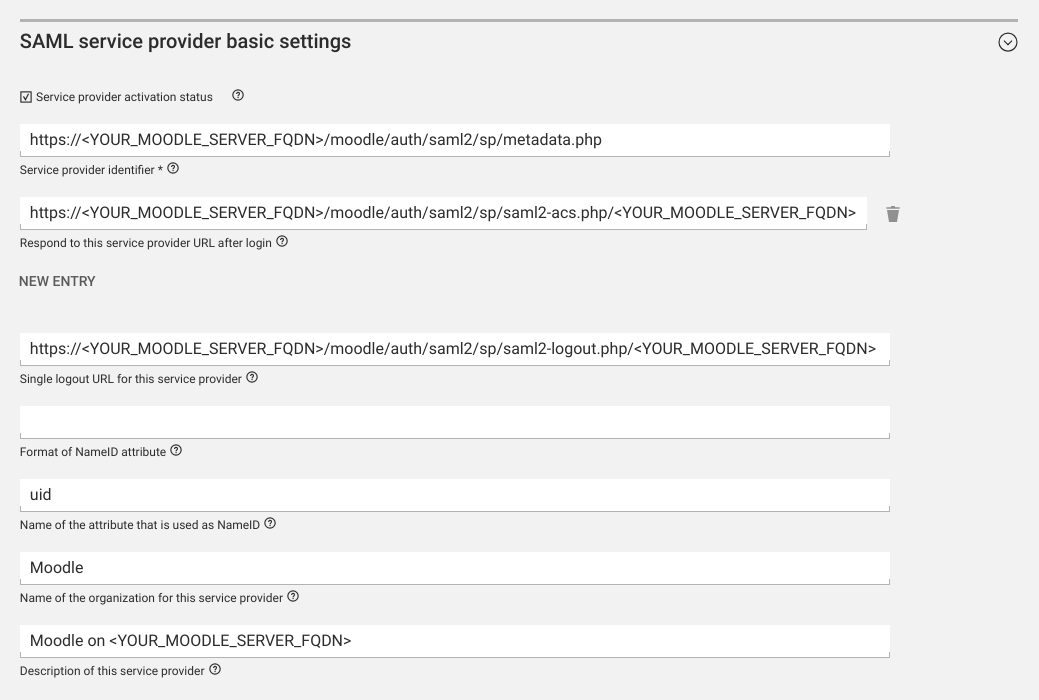
SAML service provider basic settings:
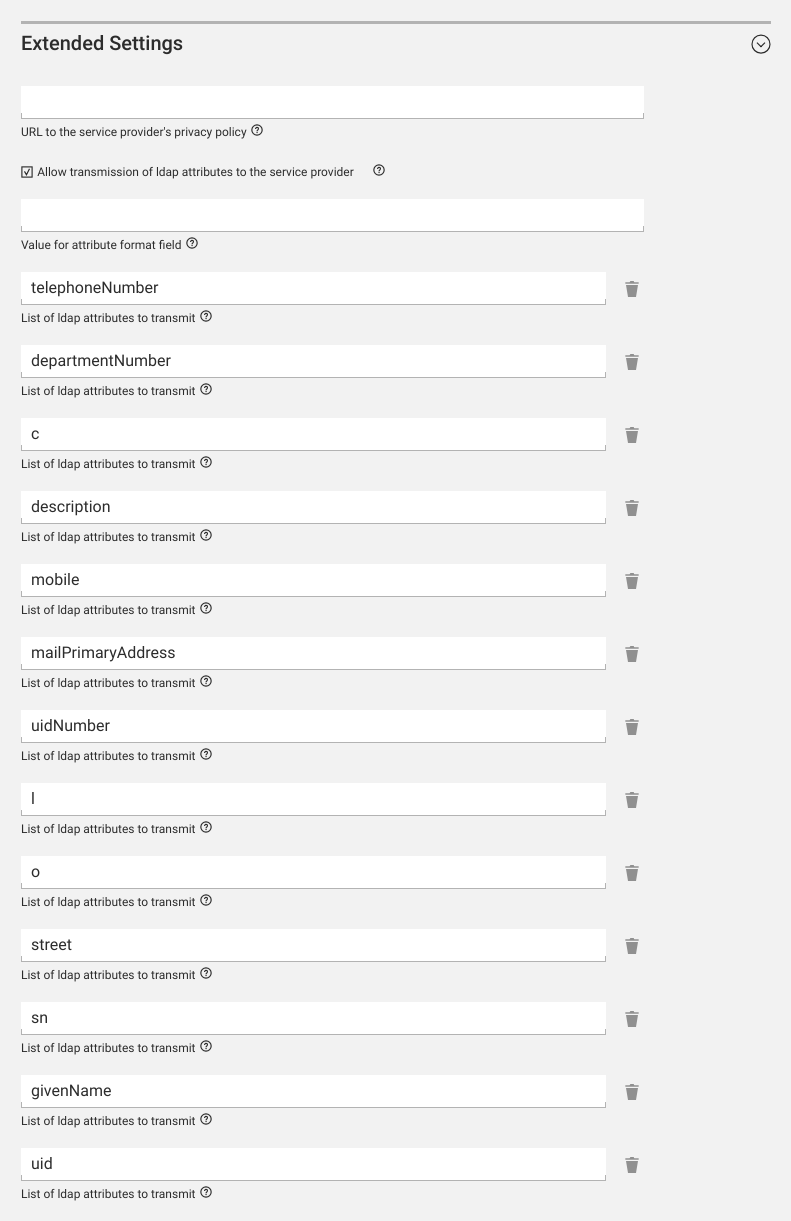
SAML service provider extended settings:
SAML Single-Sign-On configuration using the web browser
Moodle is now allowed to send authentication requests to our UCS server. Next, we will have to configure the Moodle SAML plugin.
Change the values under the Moodle web page Site Administration → Plugins → Authentication → Manage authentication → SAML2 → Settings to successfully configure the SAML plugin:
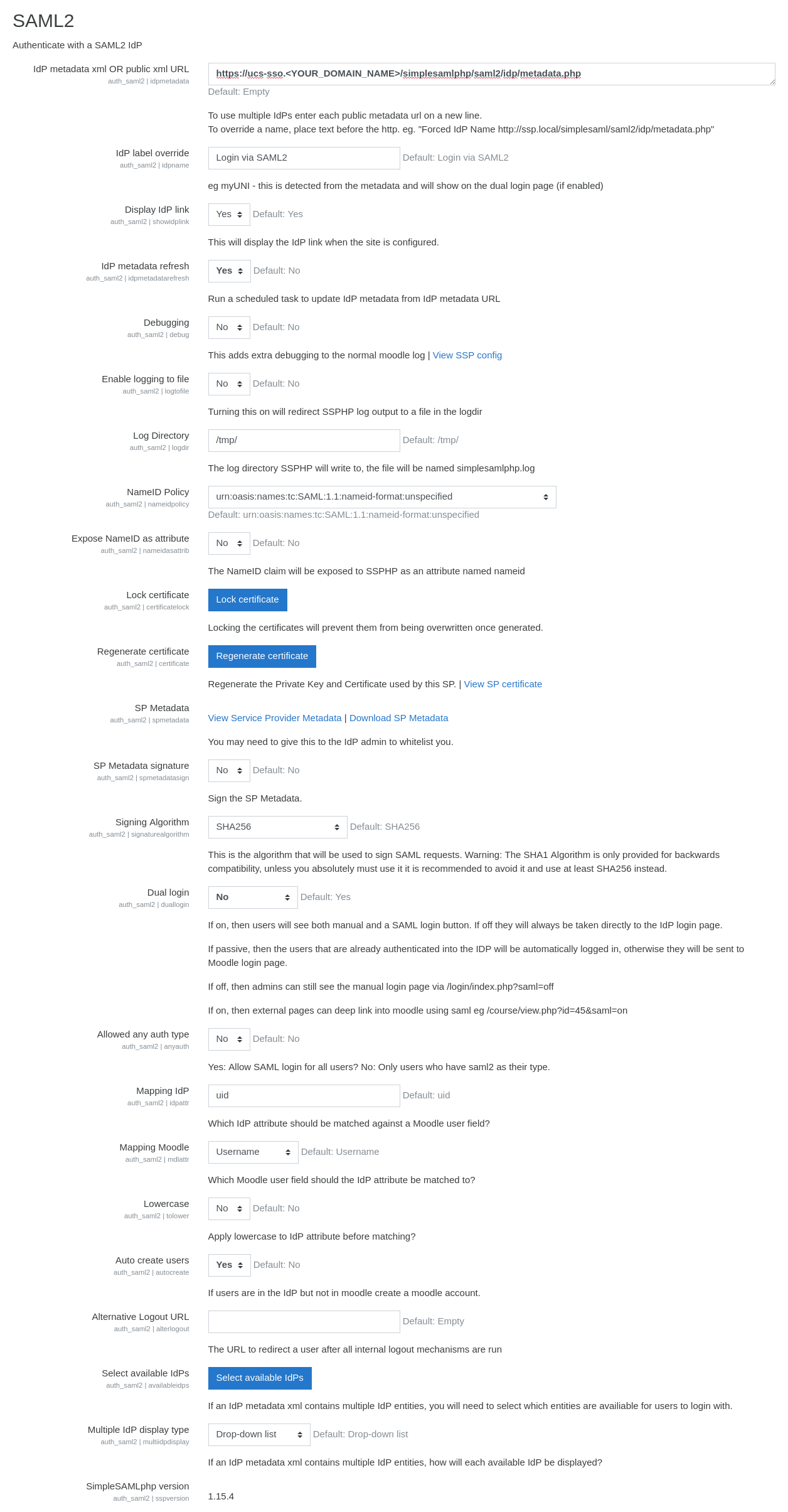
SAML server settings:
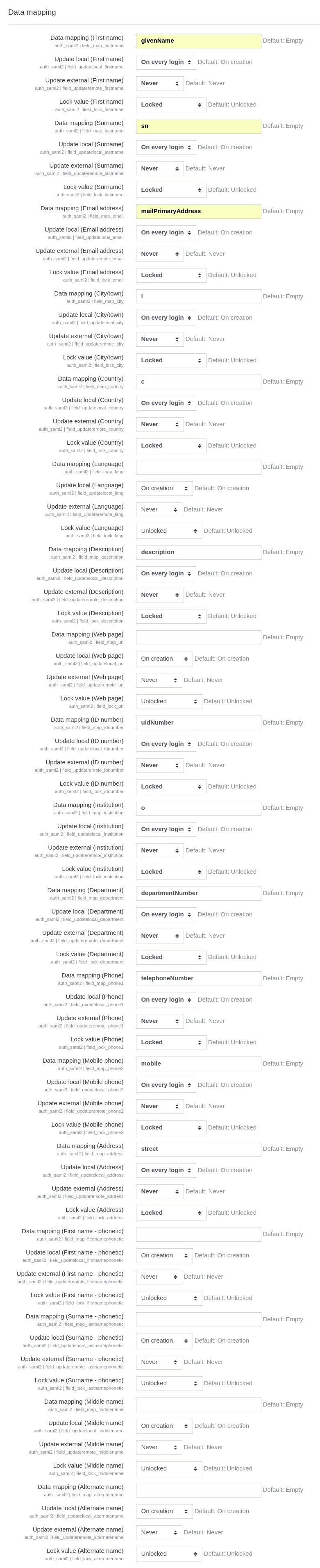
Data mapping:
We are almost finished. As last we will have to activate our registered SAML service provider for all wanted users. Please follow the Postrequisites to achieve this.
Postrequisites
We can now activate Moodle for all wanted users. For this, we need to enable users for the created Moodle service providers on the user’s Account tab.
- Open the Univention Management Console module Users
- Select all users you want to enable for Moodle
- Open the Account tab
- Add your created service provider inside the SAML settings section (It’s entry schould look like: “https://<YOUR_MOODLE_SERVER_FQDN>/moodle/auth/saml2/sp/metadata.php”)
- Save the changes
You should now be able to login as any user that is enabled for the registered SAML service provider. Note that some attributes like Email address are mandatory for moodle. Users without valid email addresses inside UCS won’t be able to leave their profile settings page, so you should make sure that all moodle users own a valid email.
Note: You can always login locally on Moodle by using the following Link: https://<YOUR_MOODLE_SERVER_FQDN>/moodle/login/index.php?saml=off
References
- Moodle SAML Plugin - Moodle plugins directory: SAML2 Single sign on | Moodle.org
- UCS SAML identity provider - Univention Corporate Server