Kudos @Moritz_Bunkus
Problem
In system diagnostic you see an error about an invalid certificate.
It might occur after having renewed your certificates based on this article.
Or you have installed external certificates based on this article.
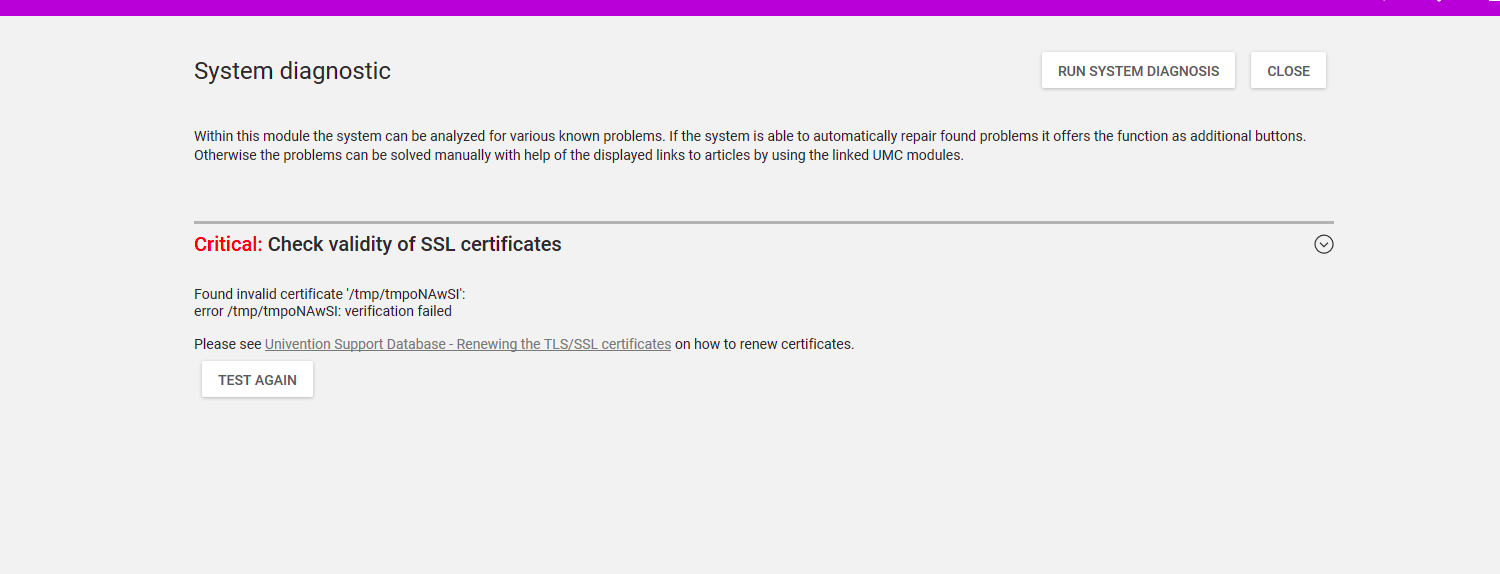
Solution
Step 1
root@ucs:~# univention-run-diagnostic-checks -t 02_certificate_check
Domain Admin Login:Administrator
Password:
You can find the logging messages of the diagnostic modules at /var/log/univention/management-console-module-diagnostic.log
############################
## Check failed: 02_certificate_check - Überprüfe Gültigkeit der SSL Zertifikate
Ungültiges Zertifikat '/etc/simplesaml.php/ucs-sso.multi.ucs.crt' gefunden:
error /etc/simplesaml.php/ucs-sso.multi.ucs.crt: verification failed
Siehe {sdb} für Informationen zum Erneuern von Zertifikaten.
########### End #############
Step 2
Verify the certificate in question:
root@ucs:~# openssl verify /etc/simplesaml.php/ucs-sso.multi.ucs.crt
If you see an error message like this proceed with the next step.
error 20 at 0 depth lookup: unable to get local issuer certificate
error /etc/simplesaml.php/ucs-sso.multi.ucs.crt: verification failed
Step 3
Check the issuer of the failing certificate:
root@ucs:~# openssl x509 -in /etc/simplesamlphp/ucs-sso.multi.local-idp-certificate.crt -noout -issuer
issuer=C = DE, ST = DE, L = DE, O = DE, OU = Univention Corporate Server, CN = Univention Corporate Server Root CA (ID=Aa7815D5), emailAddress = ssl@multi.lan
Note: In case you see “Univention Corporate Server Root CA” as issuer proceed to step 4B. If the certificate has been issued by an official (public) CA proceed with step 4A.
Step 4A
If the certificate has been issued by an official (public) CA, follow these steps:
Step 4A-1
Get the CA from the issuer:
root@ucs:~# wget http://repository.certum.pl/myIssuerCA.cer
root@ucs:~# file myIssuerCA.cer
myIssuerCA.cer: data
Step 4A-2
Convert the data to pem
root@ucs:~# openssl x509 -inform der -in myIssuerCA.cer -out myIssuerCA.pem
root@ucs:~# file myIssuerCA.pem
myIssuerCA.pem: PEM certificate
Step 4A-3
Rename it into the expected ending and copy it to the destination folder.
root@ucs:~# mv myIssuerCA.pem myIssuerCA.crt
root@ucs:~# cp myIssuerCA.crt /usr/local/share/ca-certificates
Step 4A-4
Update the ca store.
root@ucs:~# update-ca-certificates
Updating certificates in /etc/ssl/certs...
1 added, 0 removed; done.
This should fix the issue and the certificate check should succeed.
Step 4B
In case you see “Univention Corporate Server Root CA” as issuer, follow these steps:
Step 4B-1
Verify the certificate with the certificate of your UCS CA (expect an error message):
openssl verify -CAfile /usr/local/share/ca-certificates/ucsCA.crt /etc/simplesaml.php/ucs-sso.multi.ucs.crt
error 20 at 0 depth lookup: unable to get local issuer certificate
error /etc/simplesaml.php/ucs-sso.multi.ucs.crt: verification failed
Step 4B-2
The CA and the issuer of your certificate do not match. Verify the subject name of the CA:
root@ucsadsrv:~# openssl x509 -noout -subject -in /usr/local/share/ca-certificates/ucsCA.crt
subject=C = DE, ST = DE, L = DE, O = DE, OU = Univention Corporate Server, CN = Univention Corporate Server Root CA (ID=Aa7815D5), emailAddress = ssl@multi.local
The issuer of the host certificate above shows with ssl@multi.lan vs. ssl@multi.local from the CA.
Step 4B-3
Verify the host’s certificate matches the CA:
root@ucsadsrv:~# openssl verify -CAfile /usr/local/share/ca-certificates/ucsCA.crt /etc/univention/ssl/ucs/cert.pem
cert.pem: OK
If this prints “OK” copy the file to the needed location:
root@ucs:~# cp /etc/univention/ssl/ucs/cert.pem /etc/simplesaml.php/ucs-sso.multi.ucs.crt
root@ucs:~# cp /etc/univention/ssl/ucs/private.key /etc/simplesaml.php/ucs-sso.multi.ucs.key
service univention-saml restart
