Problem
If you get an failure message “invalid request” while login to SSO/Keycloak you could check the App Logs for:
univention-app logs keycloak
2024-08-01 12:57:03,011 DEBUG [org.keycloak.protocol.saml.SamlService] (executor-thread-102) ** login request
2024-08-01 12:57:03,011 DEBUG [org.hibernate.resource.jdbc.internal.LogicalConnectionManagedImpl] (executor-thread-102) `hibernate.connection.provider_disables_autocommit` was enabled. This setting should only be enabled when you are certain that the Connections given to Hibernate by the ConnectionProvider have auto-commit disabled. Enabling this setting when the Connections do not have auto-commit disabled will lead to Hibernate executing SQL operations outside of any JDBC/SQL transaction.
2024-08-01 12:57:03,011 DEBUG [org.hibernate.resource.transaction.backend.jta.internal.JtaTransactionCoordinatorImpl] (executor-thread-102) Hibernate RegisteredSynchronization successfully registered with JTA platform
2024-08-01 12:57:03,012 DEBUG [org.hibernate.orm.sql.exec] (executor-thread-102) Skipping reading Query result cache data: cache-enabled = false, cache-mode = NORMAL
2024-08-01 12:57:03,012 DEBUG [org.hibernate.orm.results] (executor-thread-102) Initializer list is empty
2024-08-01 12:57:03,012 DEBUG [org.hibernate.SQL] (executor-thread-102) select ce1_0.ID from CLIENT ce1_0 where ce1_0.CLIENT_ID=? and ce1_0.REALM_ID=?
2024-08-01 12:57:03,012 FINE [org.postgresql.jdbc.PgConnection] (executor-thread-102) setAutoCommit = false
2024-08-01 12:57:03,012 DEBUG [org.keycloak.transaction.JtaTransactionWrapper] (executor-thread-102) new JtaTransactionWrapper
2024-08-01 12:57:03,012 DEBUG [org.keycloak.transaction.JtaTransactionWrapper] (executor-thread-102) was existing? true
2024-08-01 12:57:03,012 DEBUG [org.keycloak.transaction.JtaTransactionWrapper] (executor-thread-102) JtaTransactionWrapper commit
2024-08-01 12:57:03,012 DEBUG [org.keycloak.transaction.JtaTransactionWrapper] (executor-thread-102) JtaTransactionWrapper end
2024-08-01 12:57:03,012 DEBUG [org.keycloak.transaction.JtaTransactionWrapper] (executor-thread-102) JtaTransactionWrapper resuming suspended
2024-08-01 12:57:03,012 WARN [org.keycloak.events] (executor-thread-102) type="LOGIN_ERROR", realmId="ucs", clientId="null", userId="null", ipAddress="10.254.10.254", error="client_not_found", reason="Cannot_match_source_hash"
Solution
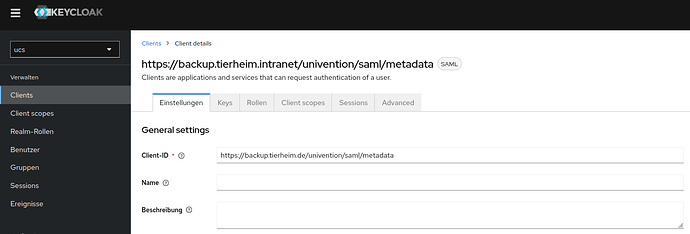
During the installation of Keycloak, the FQDN which Keycloak should be accessible can be defined via the settings by the Client-ID.
However, the Keycloak script sets the FQDNs it receives from the systems/nodes and configures the SP/clients in Keycloak accordingly by using this script /usr/lib/univention-install/50keycloak.inst.
The setting that the script sets for the Client in Keycloak is:
https://backup.tierheim.intranet/univention/saml/metadata
But in the App-Settings the following FQDN are used to reach Keycloak.
https://backup.tierheim.de/univention/saml/metadata
Change the Client-ID URI to make Keycloak reachable
Defines the ID that is referenced in the URI and token. For example ‘my-client’. With SAML, this is also the expected issuer value of authn requests.
Change the realm to “ucs”, go to the tab “Clients” and choose the Client, you want to modify the URI.
Now the Keycloak login will be reachable
See also: