The OX Connector was broken after update.
The joinscript 50ox-connector.inst was failing, also 65univention-ox.inst as follow-up problem.
I got following error message in join.log:
ERROR: Timeout waiting for /usr/lib/python3/dist-packages/univention/admin/handlers/oxmail/oxcontext.py.
ucs_registerLDAPExtension: registraton of /var/lib/univention-appcenter/apps/ox-connector/data/resources//udm/handlers/oxmail/oxcontext.py failed.
unknown module oxmail/oxcontext.
…50ox-connector.inst: Failed to register LDAP module.
The problem was the missing handlers which I manually downloaded from github:
git clone GitHub - univention/ox-connector
cd ox-connector/udm/handlers/
cp -a oxmail oxresources /usr/lib/python3/dist-packages/univention/admin/handlers/
After that I could add new users with OX access and found following in /var/log/univention/listener.log:
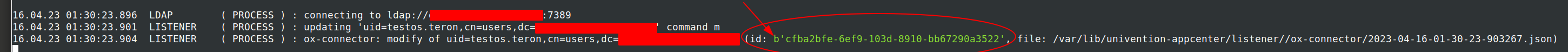
Off-Topic: The marked “b” in the screenshot looks identically to this issue, which could be a hint for the developers: UCS 5/ox-connector issue: OX global addressbook: all telephone numbers with leading "b'[number]'"
Back to topic: The test user cannot login to OX, because the user is not found in context:
/var/log/open-xchange/open-xchange.log.11: com.openexchange.login.login=testos.teron
/var/log/open-xchange/open-xchange.log.11:com.openexchange.exception.OXException: USR-0015 Categories=ERROR Message=‘Cannot find user with identifier testos.teron in context 10.’ exceptionID=-299353422-237959
After that I checked the folder /var/lib/univention-appcenter/listener/ox-connector/ which is empty.
I checked the container and found persistent folder e.g. /var/lib/univention-appcenter/listener/ox-connector/ with 651 JSON files in it.
This means the SOAP requests are not working.
But log file looks ok:
The OX SOAP service is up and running:
/var/log/open-xchange/open-xchange.log.0:CXF SOAP service is up and running
I could not find anything interesting in the open-xchange logs related to the SOAP API which means the ox-connector does not connect to it.
Then I started a shell in the ox-connector container and executed /usr/bin/python3 /tmp/univention-ox-connector.listener_trigger
This resulted in following error message:
Error while processing /var/lib/univention-appcenter/apps/ox-connector/data/listener/2023-04-16-00-22-58-029382.json
Traceback (most recent call last):
- File “/usr/lib/python3.9/site-packages/urllib3/connectionpool.py”, line 699, in urlopen*
- httplib_response = self._make_request(*
- File “/usr/lib/python3.9/site-packages/urllib3/connectionpool.py”, line 382, in _make_request*
- self._validate_conn(conn)*
- File “/usr/lib/python3.9/site-packages/urllib3/connectionpool.py”, line 1010, in _validate_conn*
- conn.connect()*
- File “/usr/lib/python3.9/site-packages/urllib3/connection.py”, line 411, in connect*
- self.sock = ssl_wrap_socket(*
- File “/usr/lib/python3.9/site-packages/urllib3/util/ssl_.py”, line 449, in ssl_wrap_socket*
- ssl_sock = _ssl_wrap_socket_impl(*
- File “/usr/lib/python3.9/site-packages/urllib3/util/ssl_.py”, line 493, in _ssl_wrap_socket_impl*
- return ssl_context.wrap_socket(sock, server_hostname=server_hostname)*
- File “/usr/lib/python3.9/ssl.py”, line 501, in wrap_socket*
- return self.sslsocket_class._create(*
- File “/usr/lib/python3.9/ssl.py”, line 1041, in _create*
- self.do_handshake()*
- File “/usr/lib/python3.9/ssl.py”, line 1310, in do_handshake*
- self._sslobj.do_handshake()*
ssl.SSLCertVerificationError: [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: unable to get local issuer certificate (_ssl.c:1129)
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
- File “/usr/lib/python3.9/site-packages/requests/adapters.py”, line 489, in send*
- resp = conn.urlopen(*
- File “/usr/lib/python3.9/site-packages/urllib3/connectionpool.py”, line 755, in urlopen*
- retries = retries.increment(*
- File “/usr/lib/python3.9/site-packages/urllib3/util/retry.py”, line 574, in increment*
- raise MaxRetryError(_pool, url, error or ResponseError(cause))*
urllib3.exceptions.MaxRetryError: HTTPSConnectionPool(host=’********’, port=443): Max retries exceeded with url: /webservices/OXContextService?wsdl (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: unable to get local issuer certificate (_ssl.c:1129)’)))
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
- File “/tmp/univention-ox-connector.listener_trigger”, line 324, in run_on_files*
- f(obj)*
- File “/usr/lib/python3.9/site-packages/univention/ox/provisioning/init.py”, line 69, in run*
- create_context(obj)*
- File “/usr/lib/python3.9/site-packages/univention/ox/provisioning/contexts.py”, line 64, in create_context*
- if context_exists(obj):*
- File “/usr/lib/python3.9/site-packages/univention/ox/provisioning/contexts.py”, line 59, in context_exists*
- return bool(get_obj_by_name_from_ox(Context, context_id, None))*
- File “/usr/lib/python3.9/site-packages/univention/ox/provisioning/helpers.py”, line 41, in get_obj_by_name_from_ox*
- return klass.from_ox(context_id, name=name)*
- File “/usr/lib/python3.9/site-packages/univention/ox/soap/backend.py”, line 280, in from_ox*
- context_service = cls.service(DEFAULT_CONTEXT)*
- File “/usr/lib/python3.9/site-packages/univention/ox/soap/backend.py”, line 105, in service*
- cls._service_objs[cls._object_type][context_id] = OxSoapServiceClass(cls.get_client_credentials(context_id))*
- File “/usr/lib/python3.9/site-packages/univention/ox/soap/services.py”, line 129, in init*
- self.Type = getattr(client_credentials.types, self._type_name)*
- File “/usr/lib/python3.9/site-packages/univention/ox/soap/credentials.py”, line 84, in types*
- self.class._types = Types(self.server)*
- File “/usr/lib/python3.9/site-packages/univention/ox/soap/types.py”, line 71, in init*
- self.class.wsdl_context = get_wsdl(server, ‘Context’)*
- File “/usr/lib/python3.9/site-packages/univention/ox/soap/services.py”, line 94, in get_wsdl*
- return ZeepClient(WS_URLS[object_type].format(server=server)).wsdl*
- File “/usr/lib/python3.9/site-packages/zeep/client.py”, line 76, in init*
- self.wsdl = Document(wsdl, self.transport, settings=self.settings)*
- File “/usr/lib/python3.9/site-packages/zeep/wsdl/wsdl.py”, line 92, in init*
- self.load(location)*
- File “/usr/lib/python3.9/site-packages/zeep/wsdl/wsdl.py”, line 95, in load*
- document = self._get_xml_document(location)*
- File “/usr/lib/python3.9/site-packages/zeep/wsdl/wsdl.py”, line 155, in _get_xml_document*
- return load_external(*
- File “/usr/lib/python3.9/site-packages/zeep/loader.py”, line 89, in load_external*
- content = transport.load(url)*
- File “/usr/lib/python3.9/site-packages/zeep/transports.py”, line 123, in load*
- content = self._load_remote_data(url)*
- File “/usr/lib/python3.9/site-packages/zeep/transports.py”, line 135, in _load_remote_data*
- response = self.session.get(url, timeout=self.load_timeout)*
- File “/usr/lib/python3.9/site-packages/requests/sessions.py”, line 600, in get*
- return self.request(“GET”, url, *kwargs)
- File “/usr/lib/python3.9/site-packages/requests/sessions.py”, line 587, in request*
- resp = self.send(prep, *send_kwargs)
- File “/usr/lib/python3.9/site-packages/requests/sessions.py”, line 701, in send*
- r = adapter.send(request, *kwargs)
- File “/usr/lib/python3.9/site-packages/requests/adapters.py”, line 563, in send*
- raise SSLError(e, request=request)*
requests.exceptions.SSLError: HTTPSConnectionPool(host=’**********’, port=443): Max retries exceeded with url: /webservices/OXContextService?wsdl (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: unable to get local issuer certificate (_ssl.c:1129)’)))
This is consecutive error #810
Sleeping for 0 sec
Successfully processed 0 files during this run
This means the ox-connector & with OX installed on UCS internally (error message sounds like self-signed certificate?) is not working at the moment for the UCS server itself?
The configuration of the ox-connector, for the UCS server where OX is installed was: “https://hostname.subdomain.domain.tld”. But the webserver of the UCS server is using a Letsencrypt certificate. We have no problems connecting to it, but the ox-connector has…
Next test:
Then I setup OX to listen also on ethernet:
ucr set ox/cfg/server.properties/com.openexchange.connector.networkListenerHost=*
Setup another apache webserver on a different (Non-UCS) Linux VM, added a proxy setup and a vhost ox.domain.tld, added a DNS A record, added a similar Letsencrypt certificate, copied the OX frontend files into document root, reloaded apache and modified then the server URL in the configuration of the ox-connector.
Smoke test: OX login possible with my previously existing user…OX is accessible.
Some seconds later:…Bamm, working now…all JSON files were processed and moved to a subdirectory “old”. Why the same OX server with similar Letsencrypt certificate on the UCS webserver is not working but a different apache which is proxying to it is?
This is now something for Univention developers to clarify this topic. For me the workaround is Ok. for now.

 hope it will be fixed soon.
hope it will be fixed soon.