How to Align Password Policies across Directory Services
Environment
There are several environments where you want to align the password settings so the replication won’t have any issue with differing configurations.
- The most common environment is an UCS with Samba/AD (Samba4).
- An UCS joint into a Microsoft/AD
- AN UCS joint into a Microsoft/AD and also providing a Samba/AD
Note: All these scenarios need to have the same password settings to avoid problems in password sync.
Where to find the password settings
Each Directory Service has it’s own settings and methods to change them.
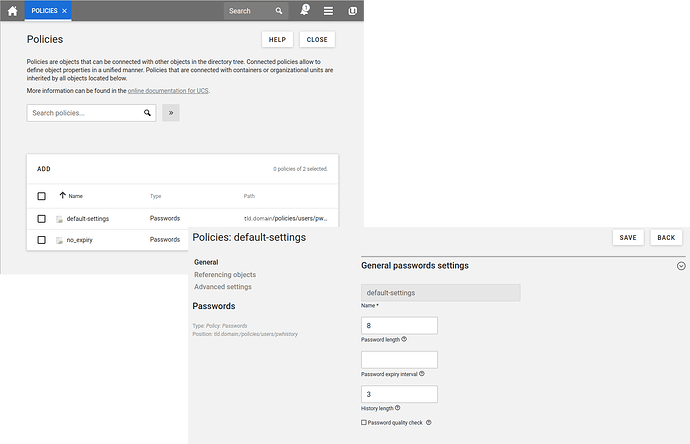
1. Univention Corporate Server
UCS stores it’s password settings within the OpenLDAP. The easiest way is to access them via udm or UMC (webfrontend).
You can have several Policies and link them to several containers or objects.
via udm in Terminal
root@ucs:~ # udm policies/pwhistory list
DN: cn=default-settings,cn=pwhistory,cn=users,cn=policies,dc=domain,dc=tld
expiryInterval: 30
ldapFilter: None
length: 3
name: default-settings
pwLength: 8
pwQualityCheck: None
DN: cn=no_expiry,cn=pwhistory,cn=users,cn=policies,dc=domain,dc=tld
expiryInterval: None
ldapFilter: None
length: 3
name: no_expiry
pwLength: 8
pwQualityCheck: FALSE
via UMC in Browser
2. Samba/AD
To access the Samba/AD password settings you need to use a Terminal.
root@ucs:~# samba-tool domain passwordsettings
Usage: samba-tool domain passwordsettings <subcommand>
Manage password policy settings.
Options:
-h, --help show this help message and exit
Available subcommands:
pso - Manage fine-grained Password Settings Objects (PSOs).
set - Set password settings.
show - Display current password settings for the domain.
For more help on a specific subcommand, please type: samba-tool domain passwordsettings <subcommand> (-h|--help)
root@ucs:~# samba-tool domain passwordsettings show
Password informations for domain 'DC=domain,DC=tld'
Password complexity: off
Store plaintext passwords: off
Password history length: 3
Minimum password length: 8
Minimum password age (days): 0
Maximum password age (days): 30
Account lockout duration (mins): 3
Account lockout threshold (attempts): 3
Reset account lockout after (mins): 30
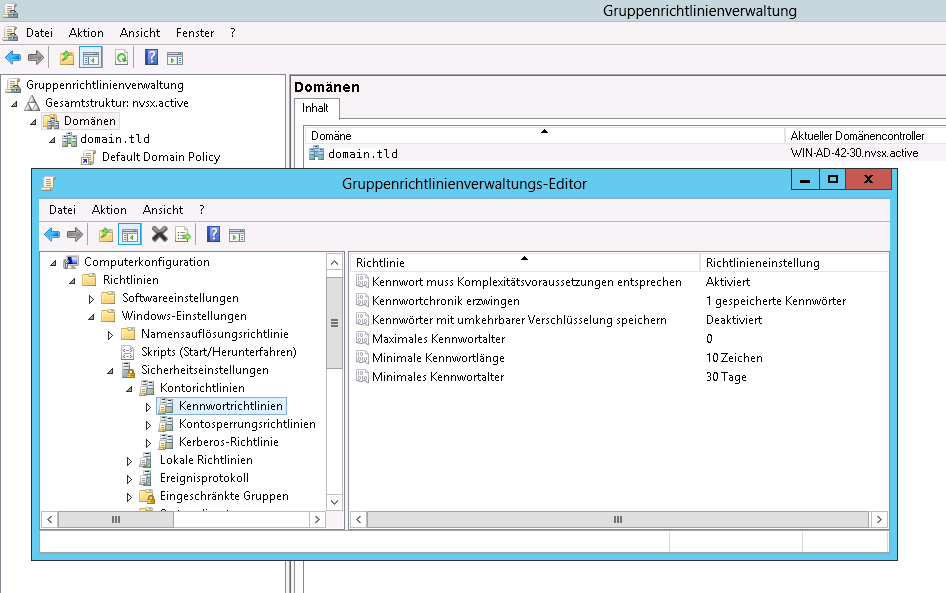
3. Microsoft/AD
In Microsoft/AD you have to log in as Domain Administrator and open the GPO-Editor to access the respective Group Policy