How to access netlogon shares of other school or domain from Microsoft Windows
Environment
- UCS@school Environment
- Windows (10 or later) client system for administrative access to all school netlogon shares
Explanation
Starting with Windows 10, Microsoft Windows clients enforce some additional security requirements for the access of remote shares via UNC path. One of these security requirements is mutual authentication. In case a Windows client is not joined to domain controller of the target system, which hosts the netlogon share, the client cannot verify the identity of the target system and thus rejects to connect to that share. This also affects UCS@school, because the individual schools are configured as stand alone Samba/AD domain controllers that only have control over the subset of identities (user, group and computer accounts) that are in the OU of that school. Vice versa, all other schools, and the central school department (where the UCS primary node is running) don’t “see” or “know” the identity/account of the target school DC. That’s a unique architecture that is specific to UCS@school that allows isolation between different schools. The following steps explain how to adjust the security rules for Hardened UNC Paths on the Windows client in such a way, that it doesn’t reject to connect to an unknown windows file server (in this case it happens to be a UCS@school DC).
Configure local GPO for “Hardened UNC Paths”
Step 1: Open local Group Policy Editor
Log into a Windows machine with administrative privileges and open the Group Policy Editor by starting gpedit.msc, e.g. via <Windows-Key>+R.
Step 2: Configure local GPO
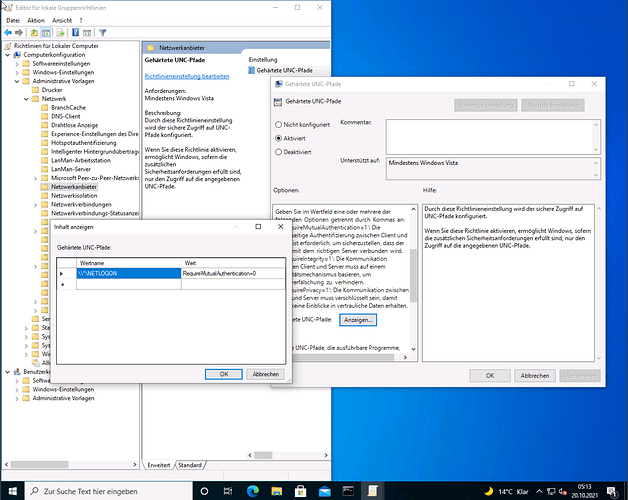
Edit the local GPO by right click and edit. Go to the policy section Computer Configuration → Administrative Templates → Network → Network Provider → Enable the Hardened UNC Paths policy → Click the Show button (Anzeigen in german localized Windows) in the middle of the left option text
Step 3: Disable mutual authentication for access to NETLOGON share
You can enter \\*\NETLOGON\ as valuename and RequireMutualAuthentication=0 as value. You also can be more specific about the UNC path, and e.g. just allow access to particular FQDNs or IPs. Close Window with Ok and save GPO bei clicking Ok on the GPO edit window too.
Step 3: Apply updated GPO
Open a command prompt by <Windows-Key>+R and gpupdate /force
Alternatively you can also configure this via local registry key: