Installation
The software is designed to operate on the UCS DC Master. To install the packages you first need to enable the Cool Solution repository.
Next, you must install the package univention-ldap-usercert on the DC Master server and should install the package on every DC Backup server. This can be achieved by using either the UMC module Package management or by manually invoking the following command on each system:
univention-install univention-ldap-usercert
Additionally, you must install the packages univention-usercert on the DC Master. Optionally, you can also install univention-windowscert for the creation of certificates for windows clients. Again, you can either use the UMC module Package management or the command line:
univention-install univention-usercert univention-windowscert
During the installation, new UCR variables will be created (see below) and the Univention directory listener daemon will be restarted.
If not run automatically, check if joinscripts must be executed by executing the follow command:
univention-run-join-scripts
Managing user certificates
To create a user certificate, open the [Options] tab in the user’s LDAP object and select “Public key infrastructure account” . This step isn’t needed for Simple authentication accounts.
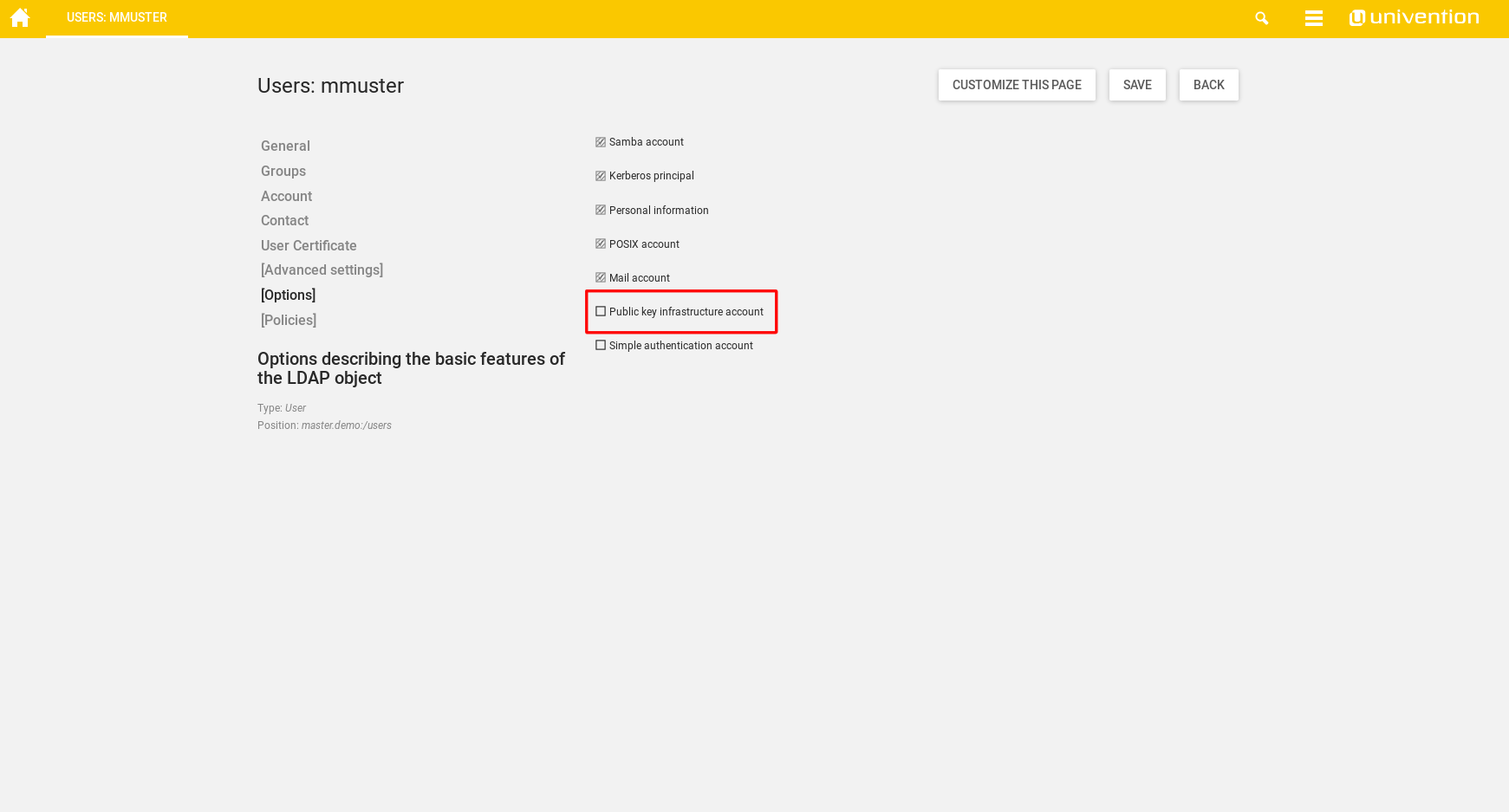
Now switch to the User Certificate tab and select “Create/Revoke User Certificate” .
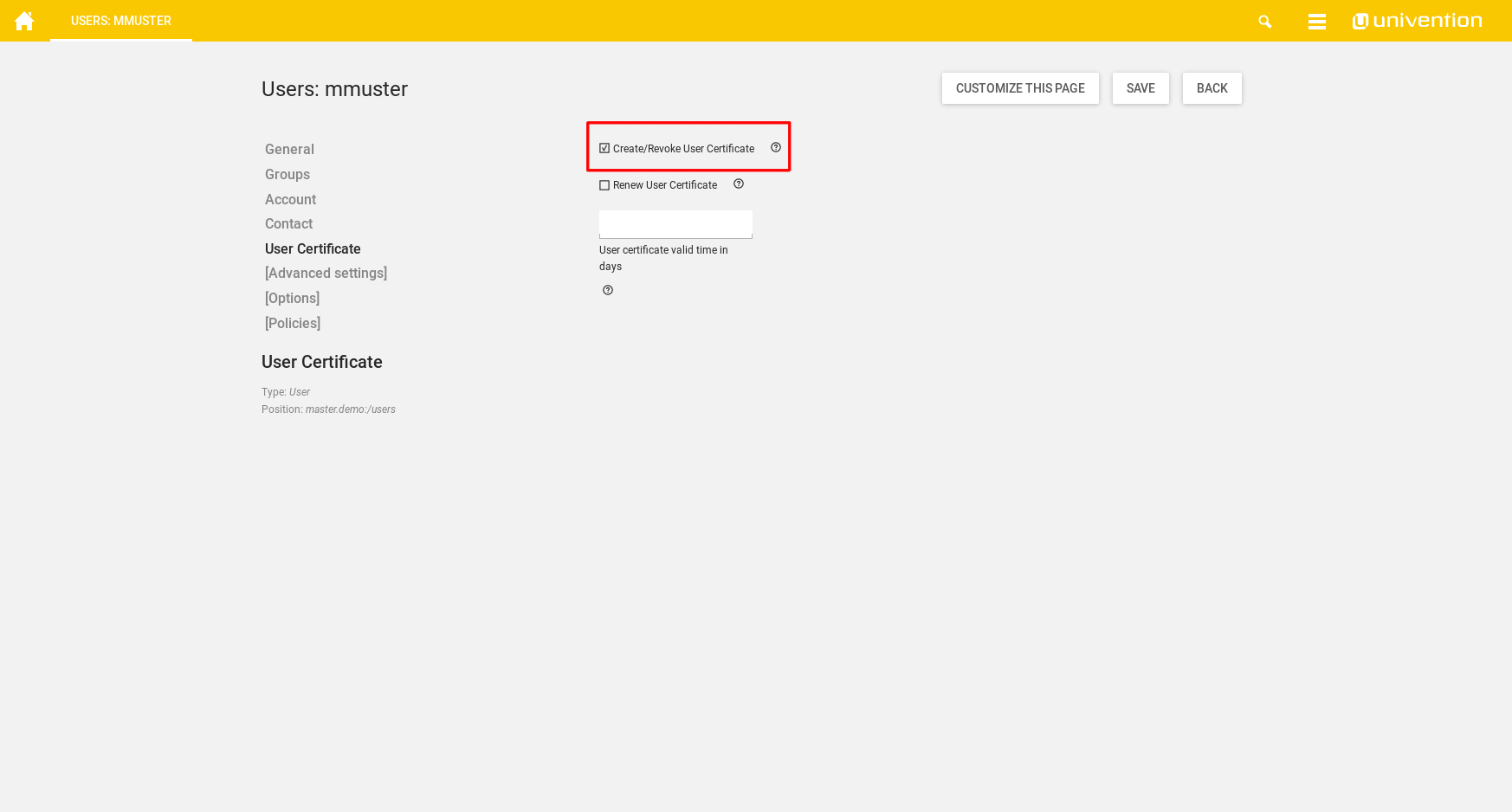
When saving, the certificate is created and saved in the directory provided in ssl/usercert/certpath in a subdirectory with the user’s UID. By default, only the user itself and the group entered in ssl/usercert/admingroup have read permission on the files. It is recommended to create a file share of the folder containing the certificates, so users can access them remotely. This can be easily achieved by following the UCS documentation Management of shares in UMC.
Note: Optionally, the standard valid time of the certificate can be overwritten here. If the field is left blank, the standard valid time from the UCR variable ssl/usercert/days will be used.
When a certificate is to be revoked, it is sufficient to untick “Create/Revoke User Certificate”. The certificate files are removed from the LDAP, but not deleted from the filesystem. If the UCS root CA was used to sign the user’s certificate, an entry is made into the Certificate Revocation List specified by /etc/univention/ssl/ucsCA/crl/ .
When a certificate needs to be renewed, it is sufficient to tick “Renew User Certificate” and save the changes made. The old certificate will then be revoked and a new one will be created with the settings from the former certificate.
Managing windows computer certificates
To create a computer certificate, open the Certificate tab on the computer’s LDAP option and select “Create/Revoke Certificate” .
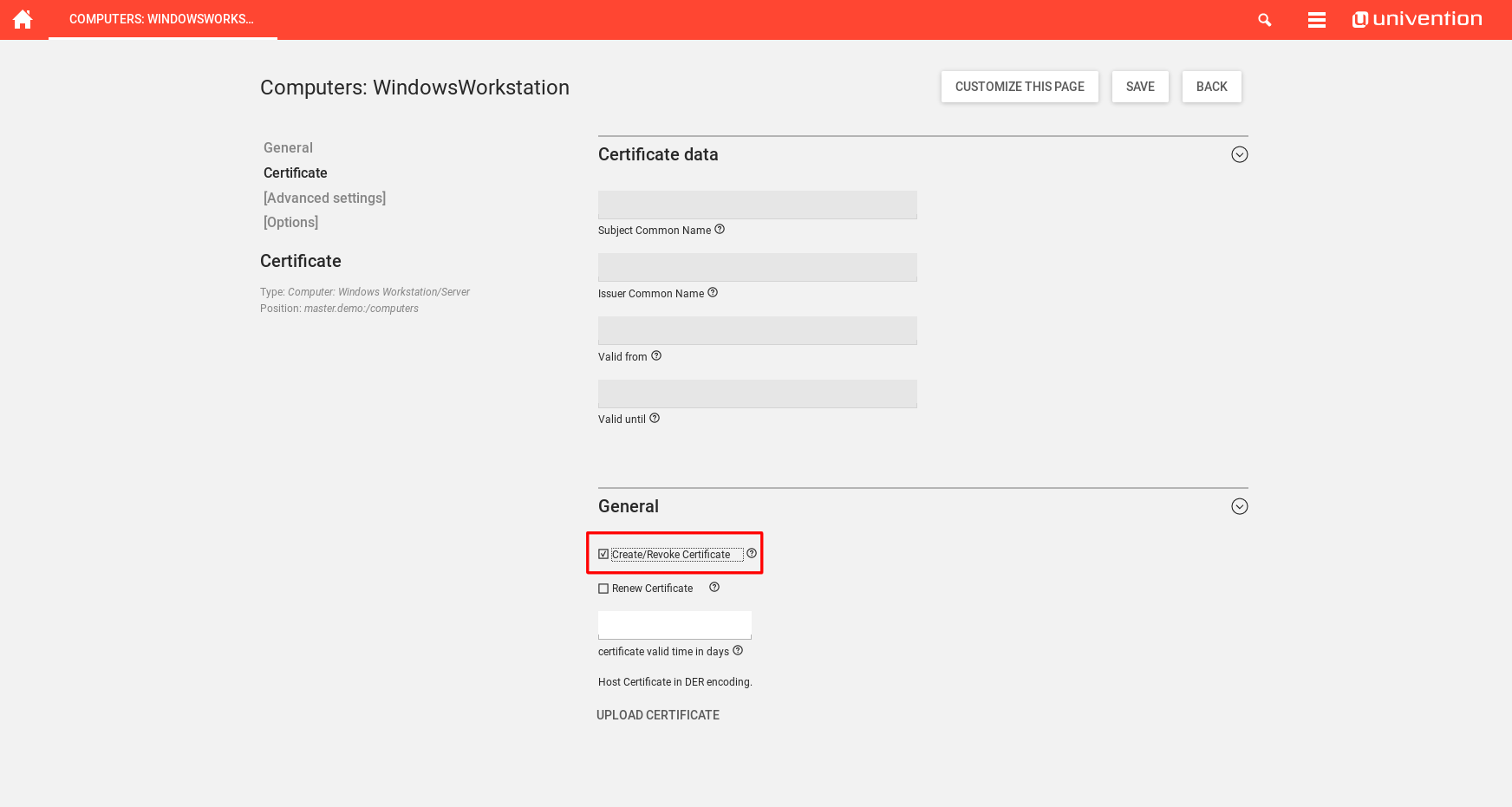
When a certificate is to be revoked, it is sufficient to untick “Create/Revoke Certificate”. The certificate files are removed from the LDAP, but not deleted from the filesystem. If the UCS root CA was used to sign the computer’s certificate, an entry is made into the Certificate Revocation List specified by /etc/univention/ssl/ucsCA/crl/ .
When a certificate needs to be renewed, it is sufficient to tick “Renew Certificate” and save the changes made. The old certificate will then be revoked and a new one will be created with the settings from the former certificate.
Windows certificates will be saved below the path specified in the UCR variable ssl/windowscert/certpath and readable for the group specified in the UCR variable ssl/windowscert/admingroup ( DC Backup Hosts by default).
Upload certificates
It is also possible to upload certificates for users and windows computers in the UMC. In this case, the certificates have to be DER encoded before the upload. If you have a PEM encoded certificate, you can convert your certificate to DER with openssl on the commadline:
openssl x509 -in /path/to/certificate.PEM -out /path/to/certificate.DER -outform DER
UCR variables and their functionality
During the installation, several new UCR variables will be created. They are as follows:
| UCR variable | Default value | Description |
|---|---|---|
| User certificate | ||
| ssl/usercert/UID/extensionsfile | <empty> | Apply the custom settings only to users named here. |
| ssl/usercert/admingroup | DC Backup Hosts | Besides the owner of the certificate, this group has read permissions on the certificate files. |
| ssl/usercert/ca | ucsCA | Folder where the Root CA files are stored (located in ssl/usercert/sslbase). |
| ssl/usercert/certldapmapping/cn | uid | Maps, which identifier from the user’s CN is mapped with the user certificate. |
| ssl/usercert/certldapmapping/email | mailPrimaryAddress | Maps, which e-mail address is mapped with the user certificate. |
| ssl/usercert/certldapmapping/locality | l | Maps, which location is mapped with the user certificate. |
| ssl/usercert/certldapmapping/organization | o | Maps, which organization is mapped with the user certificate. |
| ssl/usercert/certldapmapping/organizationalunit | <empty> | Maps, which business unit is mapped with the user certificate. |
| ssl/usercert/certldapmapping/state | <empty> | Maps, which state is mapped with the user certificate. |
| ssl/usercert/certpath | /etc/univention/ssl/user | Default path where the user certificates are saved in a UID labeled subdirectory. |
| ssl/usercert/days | 1825 | Default time that a certificate is valid. Can be overwritten in the user’s UMC object. |
| ssl/usercert/default/country | Defaults to Root CA’s country | By default, no LDAP mapping exists for this variable, the value from ssl/country will be used. |
| ssl/usercert/default/email | Defaults to Root CA’s e-mail | By default, no LDAP mapping exists for this variable, the value from ssl/email will be used. |
| ssl/usercert/default/locality | Defaults to Root CA’s location | By default, no LDAP mapping exists for this variable, the value from ssl/locality will be used. |
| ssl/usercert/default/organization | Defaults to Root CA’s organization | By default, no LDAP mapping exists for this variable, the value from ssl/organization will be used. |
| ssl/usercert/default/organizationalunit | Defaults to Root CA’s business unit | By default, no LDAP mapping exists for this variable, the value from ssl/organizationalunit will be used. |
| ssl/usercert/default/state | Defaults to Root CA’s state | By default, no LDAP mapping exists for this variable, the value from ssl/state will be used. |
| ssl/usercert/extensionsfile | <empty> | Overwrite the default openSSL settings with custom settings. |
| ssl/usercert/ldapimport | yes | If set to yes/true, the public certificate is imported into the LDAP. |
| ssl/usercert/passwordchars | <empty> | Any number can be entered here to specify the password length. |
| ssl/usercert/pkcs12/chain | yes | Whether the PKCS12 chain is saved in the certificate. |
| ssl/usercert/sslbase | /etc/univention/ssl/ | SSL root directory. |
| Windows certificate | ||
| ssl/windowscert/UID/extensionsfile | <empty> | Apply the custom settings only to computers named here. |
| ssl/windowscert/admingroup | DC Backup Hosts | Besides the owner of the certificate, this group has read permissions on the certificate files. |
| ssl/windowscert/ca | ucsCA | Certificate to sign the computer certificate with. |
| ssl/windowscert/certldapmapping/cn | cn | Maps, which identifier from the computer’s CN is mapped with the computer certificate. |
| ssl/windowscert/certldapmapping/email | <empty> | Maps, which e-mail address is mapped with the computer certificate. |
| ssl/windowscert/certldapmapping/locality | <empty> | Maps, which location is mapped with the user certificate. |
| ssl/windowscert/certldapmapping/organization | <empty> | Maps, which organization is mapped with the user certificate. |
| ssl/windowscert/certldapmapping/organizationalunit | <empty> | Maps, which business unit is mapped with the user certificate. |
| ssl/windowscert/certldapmapping/state | <empty> | Maps, which state is mapped with the user certificate. |
| ssl/windowscert/certpath | /etc/univention/ssl/windows-hosts | Path where the certificates are saved. Only the computer account and the group in ssl/windowscert/admingroup can access this directory. |
| ssl/windowscert/days | 1825 | Default time that a certificate is valid. Can be overwritten in the computers’s UMC object. |
| ssl/windowscert/extensionsfile | <empty> | Overwrite the default openSSL settings with custom settings. |
| ssl/windowscert/ldapimport | yes | Whether the public certificate should be imported automatically. |
| ssl/windowscert/passwordchars | <empty> | Any number can be entered here to specify the password length. |
| ssl/windowscert/pkcs12/chain | yes | Whether the PKCS12 chain is saved in the certificate. |
| ssl/windowscert/sslbase | /etc/univention/ssl/ | Base directory where all SSL certificates are saved. |
Apache and SSL certificates
It is possible to configure the Apache webserver, so that only users with a valid certificate imported in the user web browser can access a webpage or directory using HTTPS.
To configure this, either expand an existing site or create a new one in /etc/apache2/ucs-sites.conf.d/ .
Attention : When expanding an existing site, please make sure that the file is not managed by an UCR template, as it may be overwritten when corresponding UCR variables are changed! Either expand the template file (handle with care!) or create a new site!
Put the following code into the site file and replace all mentions of subfolder my_protected_directory with your own:
# CA Certificates for Client Auth
SSLCACertificateFile /etc/univention/ssl/ucsCA/CAcert.pem
SSLCACertificatePath /etc/univention/ssl/ucsCA/
SSLCARevocationCheck chain
# Revocation list
SSLCARevocationFile /etc/univention/ssl/ucsCA/crl/crl.pem
# A forced redirect to HTTPS, as HTTP won't work
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteRule ^/?my_protected_directory/(.*) https://%{SERVER_NAME}/my_protected_directory/$1 [R,L]
# Protected directory
<Directory /var/www/my_protected_directory>
Options Indexes FollowSymLinks MultiViews
Require all granted
SSLVerifyClient require
SSLVerifyDepth 5
SSLOptions +FakeBasicAuth
SSLRequireSSL
</Directory>
After creating a new site, or expanding an existing one, the Apache webserver must be reloaded:
systemctl reload apache2
Handling of revoked certificates
Apache only checks the certificate revocation list when the service is reloaded. It is adviced to create a cronjob using UCR that reloads the service on a daily basis:
ucr set \
cron/reload-apache2/command="systemctl reload apache2" \
cron/reload-apache2/time="0 0 * * *"
The above cronjob reloads Apache once a day at midnight.
Update to UCS 5
Note: In ordner to have a fully-functioning cool solution after an Update to UCS 5 the UCS systems have to be updated to a minimum UCS Version of UCS 5.0-2.
Shortly before upgrading to UCS 5 please update the cool solution packages on all servers that have the corresponding packages installed:
univention-install univention-ldap-usercert univention-usercert univention-windowscert
This should update all of the packages to a version 4.2.0-8. After that you can check the join status of your systems. Additionally you should force run the corresponding join script:
univention-check-join-status
univention-run-join-scripts --force --run-scripts 31univention-usercert.inst
And if everything is joined successfully start the upgrade to UCS 5 in your prefered way.
NOTE: You have to upgrade to a minimum version of UCS 5.0-2. The update from UCS 5.0-1 to 5.0-2 might be blocked because of the cool solution repository. As a work around you can unset the corresponding UCR variables
ucr unset repository/online/component/cool-solutions \
repository/online/component/cool-solutions/version \
repository/online/component/cool-solutions/unmaintained
Set them again after the succesful update to UCS 5.0-2:
ucr set repository/online/component/cool-solutions=yes \
repository/online/component/cool-solutions/version=current \
repository/online/component/cool-solutions/unmaintained=yes
