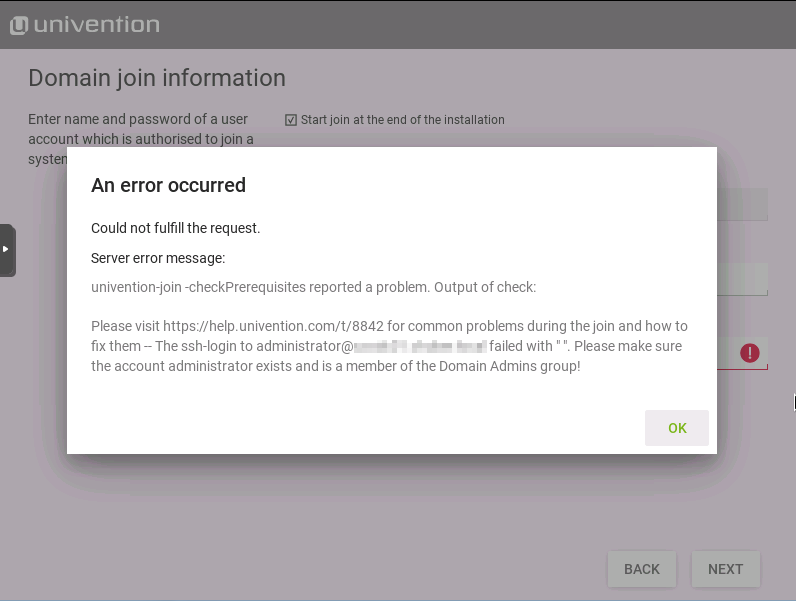
Hi,
I have increased the ssh timeout in the univention-join script. Now univention-ssh finished with success. Good, but later on the script stops at the univention-ldap search complaining about a bad bind…
Here is the log of the join. Very weird.
Thank you for your help!
G
Chris
Thu Jan 31 23:42:01 CET 2019: starting /usr/sbin/univention-join -verbose -dcaccount administrator -dcpwd /tmp/pwdtxt
+ '[' -n 2 ']'
+ old_listener_debug_level=2
+ ucr set listener/debug/level=4
Setting listener/debug/level
+ listener_debug_level=4
+ display_header
+ echo 'univention-join: joins a computer to an ucs domain'
+ echo 'copyright (c) 2001-2018 Univention GmbH, Germany'
+ echo ''
+ '[' domaincontroller_slave = domaincontroller_master ']'
+ '[' -z administrator ']'
+ '[' '!' -f /tmp/tmp.2oSvCjkRZ6/dcpwd ']'
+ chmod 600 /tmp/tmp.2oSvCjkRZ6/dcpwd
+ '[' -n '' ']'
+ '[' domaincontroller_slave = fatclient ']'
+ '[' -z domaincontroller_slave ']'
+ '[' -z '' ']'
+ echo -n 'Search DC Master: '
++ sed -ne '$s/.* \([^ ]\+\)\.$/\1/p'
++ host -t SRV _domaincontroller_master._tcp.domain
+ DCNAME=mydc.domain
+ '[' -n mydc.domain ']'
+ echo -e '\033[60Gdone'
+ DCNAME=mydc.domain
+ '[' -z mydc.domain ']'
+ echo -n 'Check DC Master: '
++ nslookup mydc.domain
+ nslookup_out='Server: 10.10.1.253
Address: 10.10.1.253#53
Name: mydc.domain
Address: 10.10.1.253'
+ '[' 0 -ne 0 ']'
++ ping -q -c 3 mydc.domain
+ ping_out='PING mydc.domain (10.10.1.253) 56(84) bytes of data.
--- mydc.domain ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 0.783/2.574/4.885/1.714 ms'
+ '[' 0 -ne 0 ']'
++ univention-ssh -timeout 55555 /tmp/tmp.2oSvCjkRZ6/dcpwd administrator@mydc.domain ls
+ ssh_out='Downloads
windows-profiles'
+ '[' 0 -ne 0 ']'
++ univention-ssh /tmp/tmp.2oSvCjkRZ6/dcpwd administrator@mydc.domain /usr/sbin/ucr search --brief '^version/'
+ versions='version/erratalevel: 410
version/patchlevel: 3
version/releasename: Neustadt
version/version: 4.3'
+ OLDIFS='
'
+ IFS='
'
+ for i in $versions
+ key=version/erratalevel
+ value=410
+ case "$key" in
+ for i in $versions
+ key=version/patchlevel
+ value=3
+ case "$key" in
+ master_patchlevel=3
+ for i in $versions
+ key=version/releasename
+ value=Neustadt
+ case "$key" in
+ master_releasename=Neustadt
+ for i in $versions
+ key=version/version
+ value=4.3
+ case "$key" in
+ master_version=4.3
+ IFS='
'
+ echo 'running version check'
running version check
+ mystatus=no
+ '[' -n 4.3 -a -n 3 ']'
+ vmaster=4.33
+ vmyself=4.33
++ echo 4.33 4.33
++ awk '{if ($1 >= $2) print "yes"; else print "no"}'
+ mystatus=yes
+ '[' no = yes ']'
+ echo 'OK: UCS version on mydc.domain is higher or equal (4.33) to the local version (4.33).'
OK: UCS version on mydc.domain is higher or equal (4.33) to the local version (4.33).
+ echo -e '\033[60Gdone'
+ '[' false = false ']'
+ '[' domaincontroller_slave = domaincontroller_backup -o domaincontroller_slave = domaincontroller_slave ']'
++ univention-ssh /tmp/tmp.2oSvCjkRZ6/dcpwd administrator@mydc.domain /usr/sbin/ucr get ldap/overlay/memberof
+ master_member_of=true
+ ucr set tmp/join/test/master/memberof=true
+ is_ucr_true tmp/join/test/master/memberof
+ local value
++ /usr/sbin/univention-config-registry get tmp/join/test/master/memberof
+ value=true
+ case "$(echo -n "$value" | tr '[:upper:]' '[:lower:]')" in
++ echo -n true
++ tr '[:upper:]' '[:lower:]'
+ return 0
+ ucr unset tmp/join/test/master/memberof
+ msg='The OpenLDAP extension memberOf is activated on the UCS master (UCR variable ldap/overlay/memberof is true). In order to join this system successfully'
+ grep -q 'install ok installed'
+ dpkg-query -W -f '${status}' univention-ldap-overlay-memberof
+ is_ucr_true ldap/overlay/memberof
+ local value
++ /usr/sbin/univention-config-registry get ldap/overlay/memberof
+ value=true
+ case "$(echo -n "$value" | tr '[:upper:]' '[:lower:]')" in
++ echo -n true
++ tr '[:upper:]' '[:lower:]'
+ return 0
+ '[' false = false -a -x /etc/init.d/univention-s4-connector ']'
+ '[' false = false -a -x /etc/init.d/slapd ']'
+ echo -n 'Stop LDAP Server: '
+ /etc/init.d/slapd stop
Stopping slapd (via systemctl): slapd.serviceWarning: slapd.service changed on disk. Run 'systemctl daemon-reload' to reload units.
.
+ echo -e '\033[60Gdone'
+ '[' false = false -a -x /etc/init.d/samba ']'
+ '[' -z '' ']'
+ echo -n 'Search ldap/base'
++ sed -ne 's|^ldap/base: ||p'
++ univention-ssh /tmp/tmp.2oSvCjkRZ6/dcpwd administrator@mydc.domain /usr/sbin/ucr search --brief '^ldap/base$'
+ ldap_base=dc=domain
+ '[' -n dc=domain ']'
+ false
+ univention-config-registry set ldap/base=dc=domain
+ echo -e '\033[60Gdone'
+ '[' false = false -a -x /etc/init.d/slapd ']'
+ echo -n 'Start LDAP Server: '
+ /etc/init.d/slapd start
Starting slapd (via systemctl): slapd.serviceWarning: slapd.service changed on disk. Run 'systemctl daemon-reload' to reload units.
.
+ echo -e '\033[60Gdone'
+ echo -n 'Search LDAP binddn '
++ univention-ssh /tmp/tmp.2oSvCjkRZ6/dcpwd administrator@mydc.domain /usr/sbin/udm users/user list --filter uid=administrator --logfile /dev/null
++ sed -ne 's|^DN: ||p'
+++ tee -a /var/log/univention/join.log
+ binddn=uid=Administrator,cn=users,dc=domain
+ '[' -z uid=Administrator,cn=users,dc=domain ']'
+ '[' -z uid=Administrator,cn=users,dc=domain ']'
+ '[' -z uid=Administrator,cn=users,dc=domain ']'
+ '[' -z uid=Administrator,cn=users,dc=domain ']'
+ echo -e '\033[60Gdone'
+ false
+ '[' -x /usr/bin/rdate ']'
+ echo -n 'Sync time: '
+ timeout -k 20 15 /usr/bin/rdate -n mydc.domain
Thu Jan 31 23:42:31 CET 2019
+ echo -e '\033[60Gdone'
+ args=()
+ '[' -n '' ']'
+ '[' 4 -lt 3 ']'
+ args+=(-binddn "$binddn")
+ false
++ get_default_ip_address
++ PYTHONPATH=/usr/lib/pymodules/python2.7/univention/config_registry
++ python2.7 -c 'from interfaces import Interfaces;print Interfaces().get_default_ip_address().ip'
+ IP=10.10.1.251
+ '[' -n 10.10.1.251 ']'
+ args+=(-ip "$IP")
+ '[' 4 -ge 3 ']'
++ get_default_netmask
++ PYTHONPATH=/usr/lib/pymodules/python2.7/univention/config_registry
++ python2.7 -c 'from interfaces import Interfaces;import ipaddr;a=Interfaces().get_default_ip_address();print a.netmask if isinstance(a,ipaddr.IPv4Network) else a.prefixlen'
+ NETMASK=255.255.255.0
+ args+=(-netmask "$NETMASK")
++ LC_ALL=C
++ ip link show
++ head -n -1
++ sed -rne 's|.*link/ether ([0-9a-fA-F:]+) brd .*|\1|p'
+ mac_addr=b6:2b:0e:a7:a4:06
+ '[' -n b6:2b:0e:a7:a4:06 ']'
+ read line
+ '[' -n b6:2b:0e:a7:a4:06 ']'
+ args+=(-mac "$line")
+ read line
+ test -x /usr/sbin/nscd
+ nscd -i hosts
+ echo -n 'Join Computer Account: '
+ args+=(-role "$server_role" -hostname "$hostname" -domainname "$domainname")
+ tee /tmp/tmp.2oSvCjkRZ6/secret
++ bashquote -binddn uid=Administrator,cn=users,dc=domain -ip 10.10.1.251 -netmask 255.255.255.0 -mac b6:2b:0e:a7:a4:06 -role domaincontroller_slave -hostname ucsdc02 -domainname domain
++ declare -a escaped
++ declare -r 'quote=\'\'''
++ local arg
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
+ grep -v '^KerberosPasswd="'
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
+ tee /tmp/tmp.2oSvCjkRZ6/scrubbed
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ for arg in "$@"
++ escaped+=("'${arg//\'/'$quote'}'")
++ echo -n ''\''-binddn'\''' ''\''uid=Administrator,cn=users,dc=domain'\''' ''\''-ip'\''' ''\''10.10.1.251'\''' ''\''-netmask'\''' ''\''255.255.255.0'\''' ''\''-mac'\''' ''\''b6:2b:0e:a7:a4:06'\''' ''\''-role'\''' ''\''domaincontroller_slave'\''' ''\''-hostname'\''' ''\''ucsdc02'\''' ''\''-domainname'\''' ''\''domain'\'''
+ univention-ssh --no-split /tmp/tmp.2oSvCjkRZ6/dcpwd administrator@mydc.domain 'DCPWD=$(mktemp) && trap "rm -f \"$DCPWD\"" EXIT && cat >"$DCPWD" && /usr/share/univention-join/univention-server-join -bindpwfile "$DCPWD"' ''\''-binddn'\'' '\''uid=Administrator,cn=users,dc=domain'\'' '\''-ip'\'' '\''10.10.1.251'\'' '\''-netmask'\'' '\''255.255.255.0'\'' '\''-mac'\'' '\''b6:2b:0e:a7:a4:06'\'' '\''-role'\'' '\''domaincontroller_slave'\'' '\''-hostname'\'' '\''ucsdc02'\'' '\''-domainname'\'' '\''domain'\'''
univention-server-join: joins a server to an univention domain
copyright (c) 2001-2018 Univention GmbH, Germany
ldap_dn="cn=ucsdc02,cn=dc,cn=computers,dc=domain"
++ sed -ne 's/^E:\s*//p' /tmp/tmp.2oSvCjkRZ6/scrubbed
+ res_message=
+ '[' -z '' ']'
+ echo -e '\033[60Gdone'
+ '[' -s /tmp/tmp.2oSvCjkRZ6/secret ']'
++ grep -e '^ldap_dn=' -e '^KerberosPasswd=' /tmp/tmp.2oSvCjkRZ6/secret
+ eval 'ldap_dn="cn=ucsdc02,cn=dc,cn=computers,dc=domain"
KerberosPasswd="pJ7DcAosYMPThJsaVC1X" '
++ ldap_dn=cn=ucsdc02,cn=dc,cn=computers,dc=domain
++ KerberosPasswd=pJ7DcAosYMPThJsaVC1X
+ '[' -n cn=ucsdc02,cn=dc,cn=computers,dc=domain ']'
+ rdn=cn=ucsdc02
+ hostname=ucsdc02
+ '[' -n ucsdc02 ']'
+ '[' -n pJ7DcAosYMPThJsaVC1X ']'
+ '[' -e /etc/machine.secret ']'
+ cat /etc/machine.secret
+ echo -n pJ7DcAosYMPThJsaVC1X
+ fromdos /etc/machine.secret
+ chmod 600 /etc/machine.secret
+ '[' -e /etc/machine.secret.SAVE ']'
+ chmod 600 /etc/machine.secret.SAVE
+ hostname ucsdc02
+ univention-config-registry set hostname=ucsdc02 ldap/hostdn=cn=ucsdc02,cn=dc,cn=computers,dc=domain
Setting hostname
Setting ldap/hostdn
File: /etc/pam.d/smtp
Multifile: /etc/ldap/slapd.conf
File: /etc/welcome.msg
Multifile: /etc/postfix/ldap.virtualwithcanonical
File: /etc/pam_ldap.conf
File: /etc/issue
Multifile: /etc/postfix/ldap.virtual_mailbox
Multifile: /etc/hosts
Multifile: /etc/postfix/ldap.groups
File: /etc/dhcp/dhclient.conf
Multifile: /etc/postfix/ldap.virtual
Multifile: /etc/postfix/ldap.canonicalrecipient
Multifile: /etc/postfix/ldap.transport
File: /etc/libnss-ldap.conf
Multifile: /etc/postfix/ldap.canonicalsender
File: /etc/apache2/sites-available/univention-proxy.conf
Multifile: /etc/postfix/ldap.virtualdomains
Multifile: /etc/postfix/ldap.distlist
Multifile: /etc/postfix/ldap.sharedfolderlocal_aliases
File: /etc/apache2/conf-available/ucs.conf
Multifile: /etc/postfix/ldap.sharedfolderlocal
File: /etc/mailname
File: /etc/cron.d/univention-directory-policy
Multifile: /etc/postfix/main.cf
Multifile: /etc/postfix/ldap.sharedfolderremote
File: /etc/hostname
Multifile: /etc/postfix/ldap.saslusermapping
Multifile: /etc/postfix/ldap.external_aliases
Multifile: /etc/apache2/sites-available/default-ssl.conf
Multifile: /etc/pam.d/univention-management-console
+ '[' -e /usr/lib/univention-install/.index.txt ']'
+ mkdir -p /var/univention-join/
+ rm -rf /var/univention-join/status
+ rm /usr/lib/univention-install/.index.txt
+ touch /var/univention-join/status
+ '[' '!' -e /usr/lib/univention-install/.index.txt ']'
+ mkdir -p /var/univention-join/
+ touch /var/univention-join/status
+ ln -sf /var/univention-join/status /usr/lib/univention-install/.index.txt
+ '[' -e /etc/univention/ssl ']'
++ date +%y%m%d%H%M
+ mv /etc/univention/ssl /etc/univention/ssl_1901312342
+ install -m 755 -d /etc/univention/ssl
+ for service in univention-directory-notifier univention-directory-listener
+ '[' -e /etc/runit/univention/univention-directory-notifier ']'
+ for service in univention-directory-notifier univention-directory-listener
+ '[' -e /etc/runit/univention/univention-directory-listener ']'
+ rm -Rf '/var/lib/univention-directory-listener/*'
+ '[' domaincontroller_slave = domaincontroller_backup ']'
+ '[' domaincontroller_slave = domaincontroller_slave ']'
+ echo -n 'Sync ldap-backup.secret: '
+ '[' -e /etc/ldap-backup.secret ']'
+ cat /etc/ldap-backup.secret
+ univention-scp /tmp/tmp.2oSvCjkRZ6/dcpwd 'administrator@mydc.domain:/etc/ldap-backup.secret /etc/ldap-backup.secret'
+ echo -e '\033[60Gdone'
+ univention-config-registry set ldap/server/name=ucsdc02.domain ldap/server/ip=10.10.1.251 'ldap/server/port?7389' ldap/master=mydc.domain 'ldap/master/port?7389' ldap/server/type=slave
Setting ldap/server/name
Setting ldap/server/ip
Not updating ldap/server/port
Setting ldap/master
Not updating ldap/master/port
Setting ldap/server/type
Multifile: /etc/ldap/slapd.conf
Multifile: /etc/postfix/ldap.virtualwithcanonical
File: /etc/pam_ldap.conf
File: /etc/krb5.conf
Multifile: /etc/postfix/ldap.virtual_mailbox
Multifile: /etc/postfix/ldap.sharedfolderlocal_aliases
Multifile: /etc/postfix/ldap.virtual
Multifile: /etc/postfix/ldap.canonicalrecipient
Multifile: /etc/postfix/ldap.transport
File: /etc/libnss-ldap.conf
Multifile: /etc/postfix/ldap.canonicalsender
Multifile: /etc/postfix/ldap.saslusermapping
Multifile: /etc/postfix/ldap.virtualdomains
Multifile: /etc/postfix/ldap.distlist
Multifile: /etc/postfix/ldap.groups
File: /etc/pam.d/smtp
Multifile: /etc/postfix/ldap.sharedfolderlocal
File: /etc/init.d/slapd
File: /etc/default/ntpdate
File: /etc/nagios/nrpe.cfg
Multifile: /etc/postfix/ldap.sharedfolderremote
File: /etc/ntp.conf
Multifile: /etc/postfix/ldap.external_aliases
File: /etc/ldap/ldap.conf
+ setup_ssl force
+ local ca dst=/etc/univention/ssl/ucsCA
+ '[' force = force ']'
+ rm -rf /etc/univention/ssl/ucsCA
+ install -m 0755 -d /etc/univention/ssl/ucsCA
+ for ca in ucsCA udsCA
+ '[' -e /etc/univention/ssl/ucsCA/CAcert.pem ']'
+ univention-scp /tmp/tmp.2oSvCjkRZ6/dcpwd -q administrator@mydc.domain:/etc/univention/ssl/ucsCA/CAcert.pem /etc/univention/ssl/ucsCA/CAcert.pem
+ for ca in ucsCA udsCA
+ '[' -e /etc/univention/ssl/ucsCA/CAcert.pem ']'
+ break
+ chmod 755 /etc/univention/ssl
+ chmod 755 /etc/univention/ssl/ucsCA
+ chmod 644 /etc/univention/ssl/ucsCA/CAcert.pem
+ ln -snf /etc/univention/ssl/ucsCA/CAcert.pem /usr/local/share/ca-certificates/ucsCA.crt
+ update-ca-certificates --fresh
Clearing symlinks in /etc/ssl/certs...
done.
Updating certificates in /etc/ssl/certs...
152 added, 0 removed; done.
Running hooks in /etc/ca-certificates/update.d...
done.
+ check_ldap_tls_connection
+ echo -n 'Check TLS connection: '
++ ucr shell ldap/master/port
+ eval ldap_master_port=7389
++ ldap_master_port=7389
+ echo univention-ldapsearch -p 7389 -s base -h mydc.domain -D uid=Administrator,cn=users,dc=doamin --bindpwdfile /tmp/tmp.2oSvCjkRZ6/dcpwd dn
+ univention-ldapsearch -p 7389 -s base -h mydc.domain -D uid=Administrator,cn=users,dc=doamin --bindpwdfile /tmp/tmp.2oSvCjkRZ6/dcpwd dn
ldap_bind: Invalid credentials (49)
+ '[' 49 '!=' 0 ']'
+ failed_message 'Establishing a TLS connection with mydc.domain failed. Maybe you didn'\''t specify a FQDN.'
+ echo ''
+ echo ''
+ echo '**************************************************************************'
+ echo '* Join failed! *'
+ echo '* Contact your system administrator *'
+ echo '**************************************************************************'
+ tee -a /var/log/univention/join.log
+ echo '* Message: Please visit https://help.univention.com/t/8842 for common problems during the join and how to fix them -- Establishing a TLS connection with mydc.domain failed. Maybe you didn'\''t specify a FQDN.'
+ echo '**************************************************************************'
**************************************************************************
* Join failed! *
* Contact your system administrator *
**************************************************************************
* Message: Please visit https://help.univention.com/t/8842 for common problems during the join and how to fix them -- Establishing a TLS connection with mydc.domain failed. Maybe you didn't specify a FQDN.
**************************************************************************
+ exit 1
+ trapOnExit
+ rm -rf /tmp/tmp.2oSvCjkRZ6
+ joinscript_remove_credentialfiles
+ test -e /var/run/univention-join/bindpwd
+ test -e /var/run/univention-join/binddn
+ '[' -n true -a true = true ']'
+ '[' -n 2 ']'
+ ucr set listener/debug/level=2
Setting listener/debug/level
++ LC_ALL=C
++ date
+ echo 'Thu Jan 31 23:43:09 CET 2019: finish /usr/sbin/univention-join'
Thu Jan 31 23:43:09 CET 2019: finish /usr/sbin/univention-join
root@ucsdc02:~#