Sorry, but this is going to be long, but I am hoping to streamline my process here so I included lots of pictures with hopefully few words 
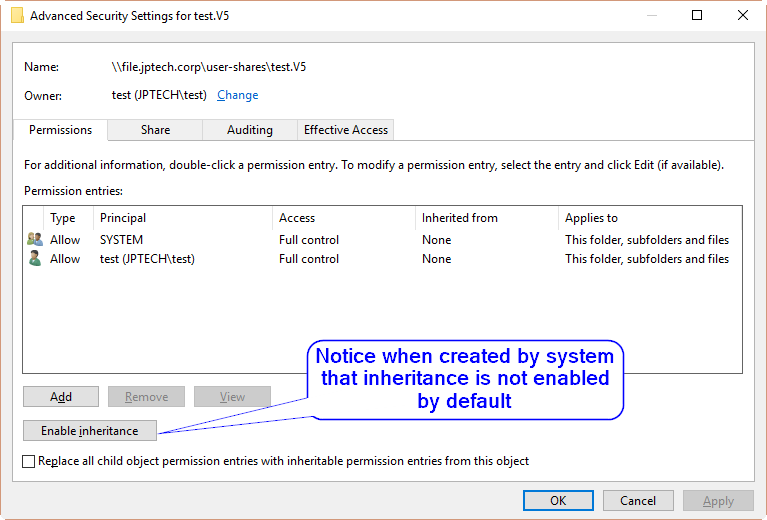
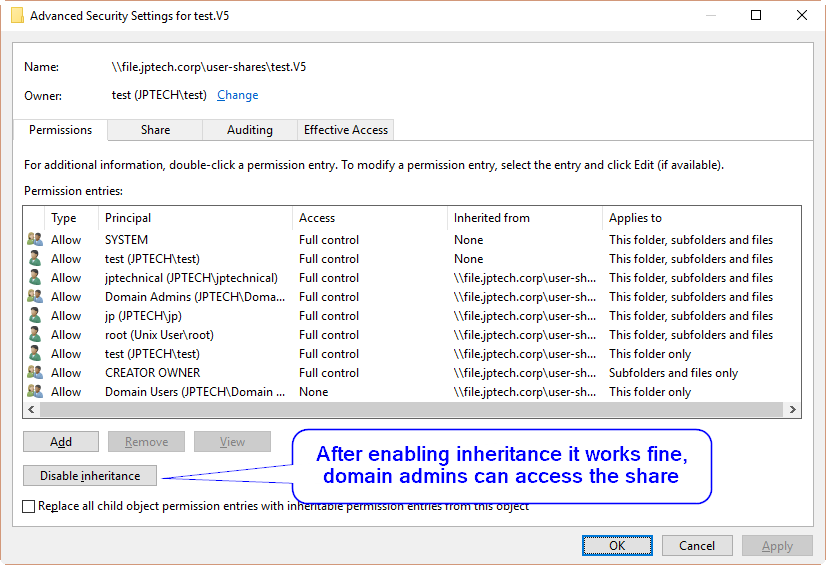
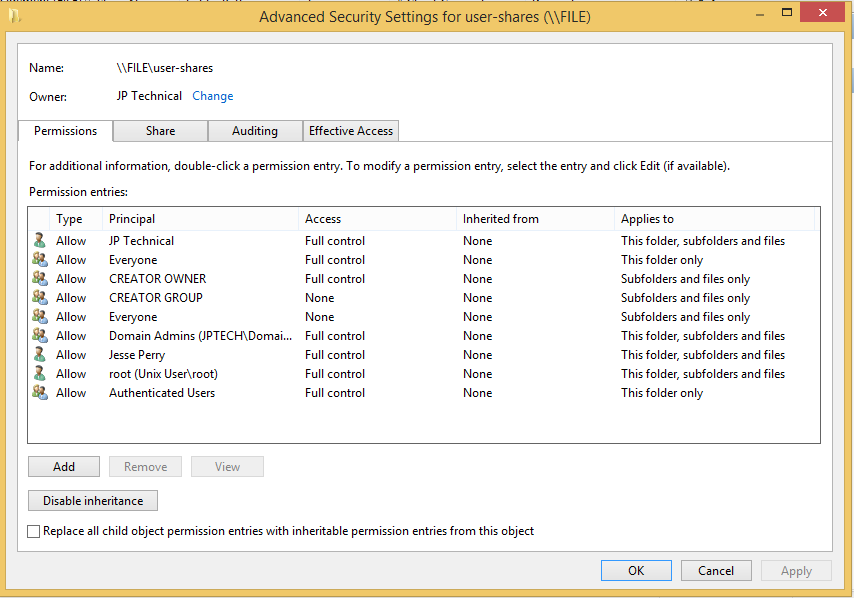
So, I have folder redirection and roaming profiles in my test env, either works as the user folders are created as needed, the user owns them and can edit the contents and the administrator@domain account can access them for backup purposes. However, they do not inherit the permissions on the share that should specify the domain admins group (for testing, will leter be a backup group used specifically for backup purposes) to be able to access them. The result is everything works until I try to access them with a domain admins account I can’t access the folders, if I login as administrator@domain I can view them just fine. If as the administrator@domain account I enable inheritance then permissions are inherited and the domain admin accounts can access them fine. This is requiring manual adjustment to each folder as it is created, in the case of roaming profiles this will be really tedious with varieties of desktop OS and v1-5 folders being created, and really it shouldn’t be necessary at all since it has never been so on M$ domains. The domain admins that might show in the pics below are ‘jp’ and ‘jptechnical’ and the domain users are ‘test’, ‘test1’, etc.
I was hoping to nail down this to a repeatable process and then make an FAQ to contribute back since I have a LOT of experience with this on the Windows side. This will be a rinse and repeat kind of thing for my business, my hope is about 4 UCS Domain deployments this summer so far.
Here are my configs in hopefully pretty graphics.
UCS shares page, I might not need to check the ‘other’ row. I did not adjust anything beyond the general page other than the options specified in the UCS manual I think.
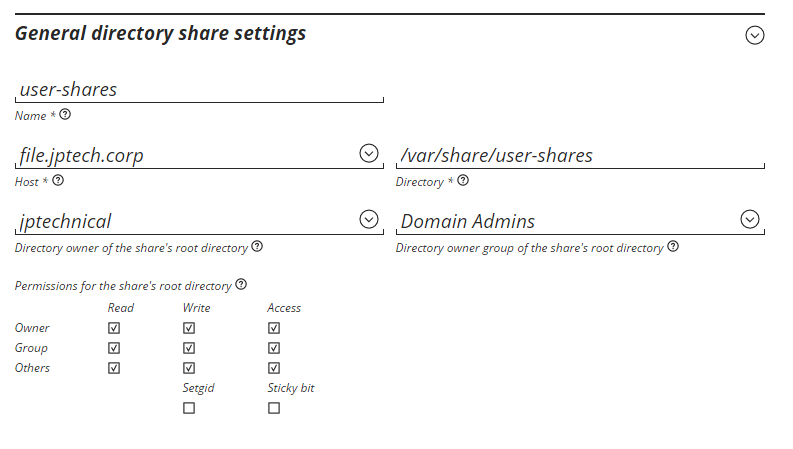
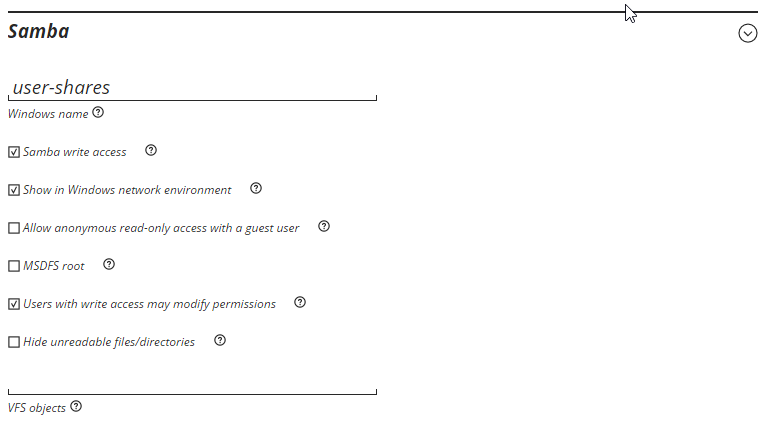
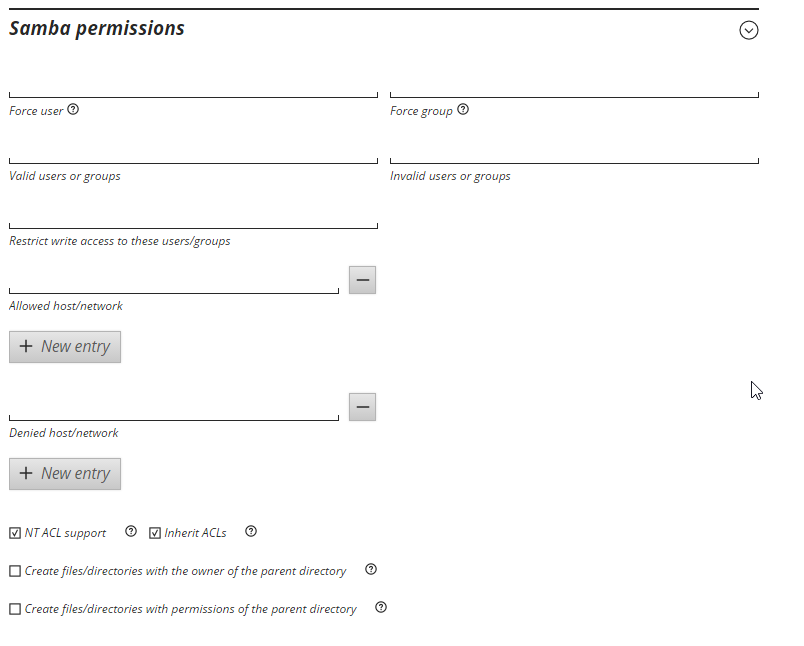
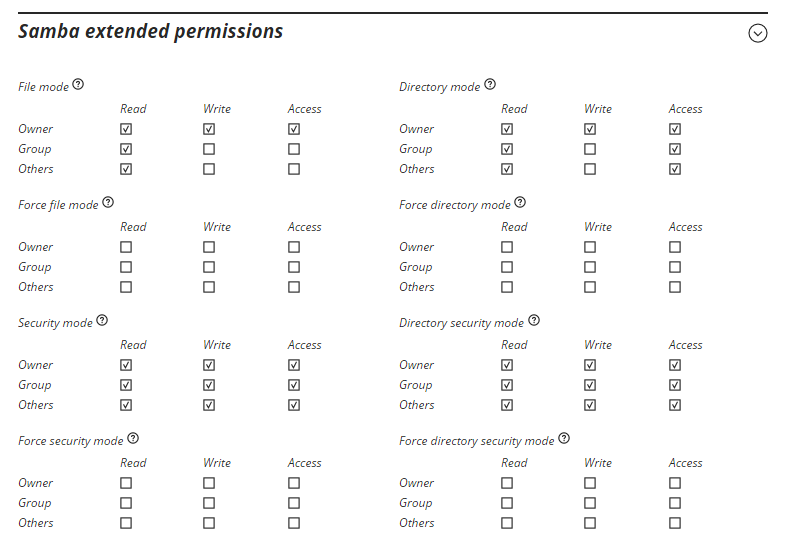
Windows shares settings, when to compmgmt.msc > connecto to computer > and edited the share from there. These are the same security settings as I would use for a windows server for the intended affect.
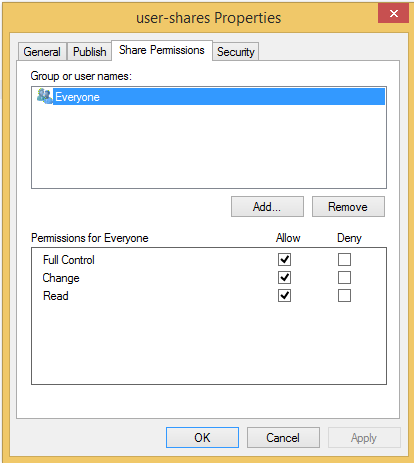
This is the result of browsing the folders created when a user logs in for the first time as a domain admin and the administrator@domain account.
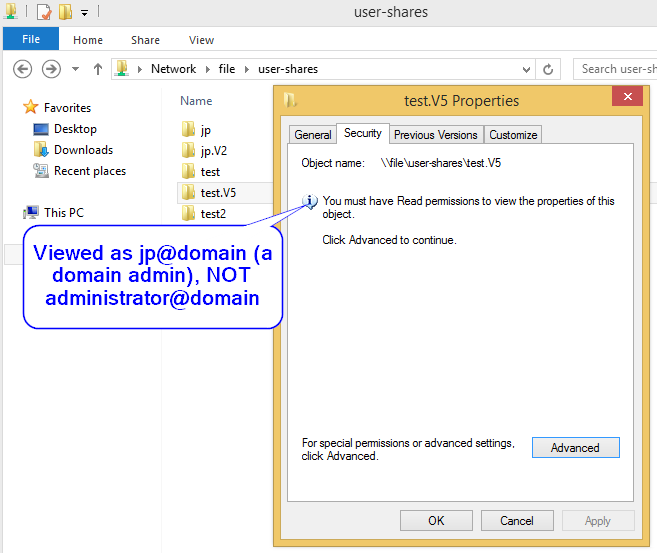
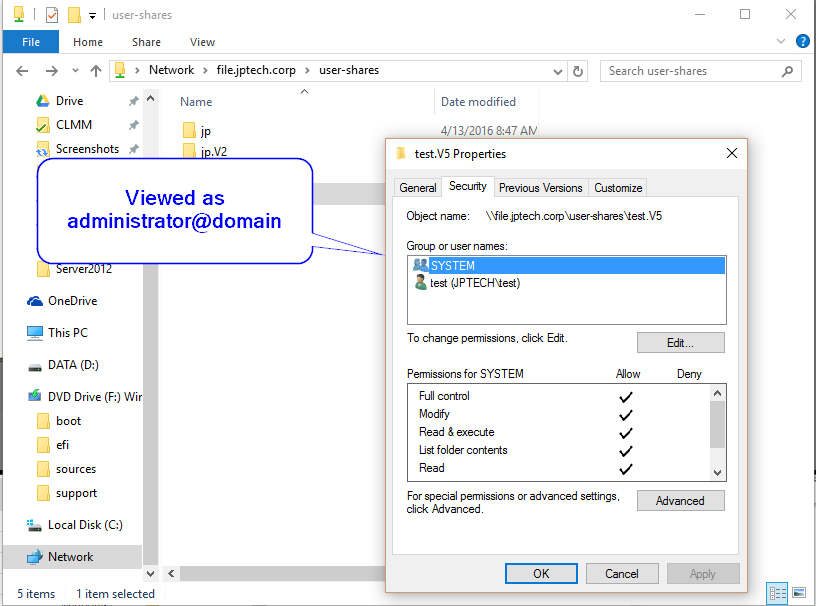
This is the result of viewing advanced security settings of the folders created when a user logs in for the first time as a domain admin and the administrator@domain account.