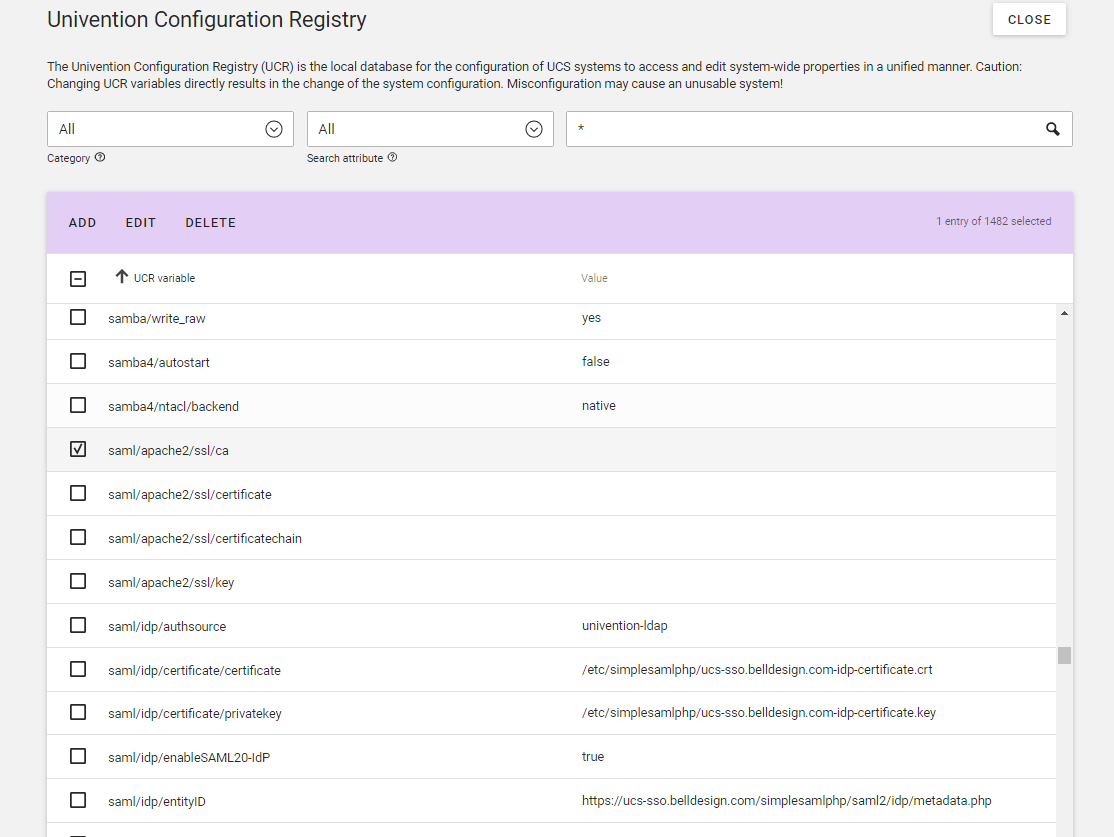
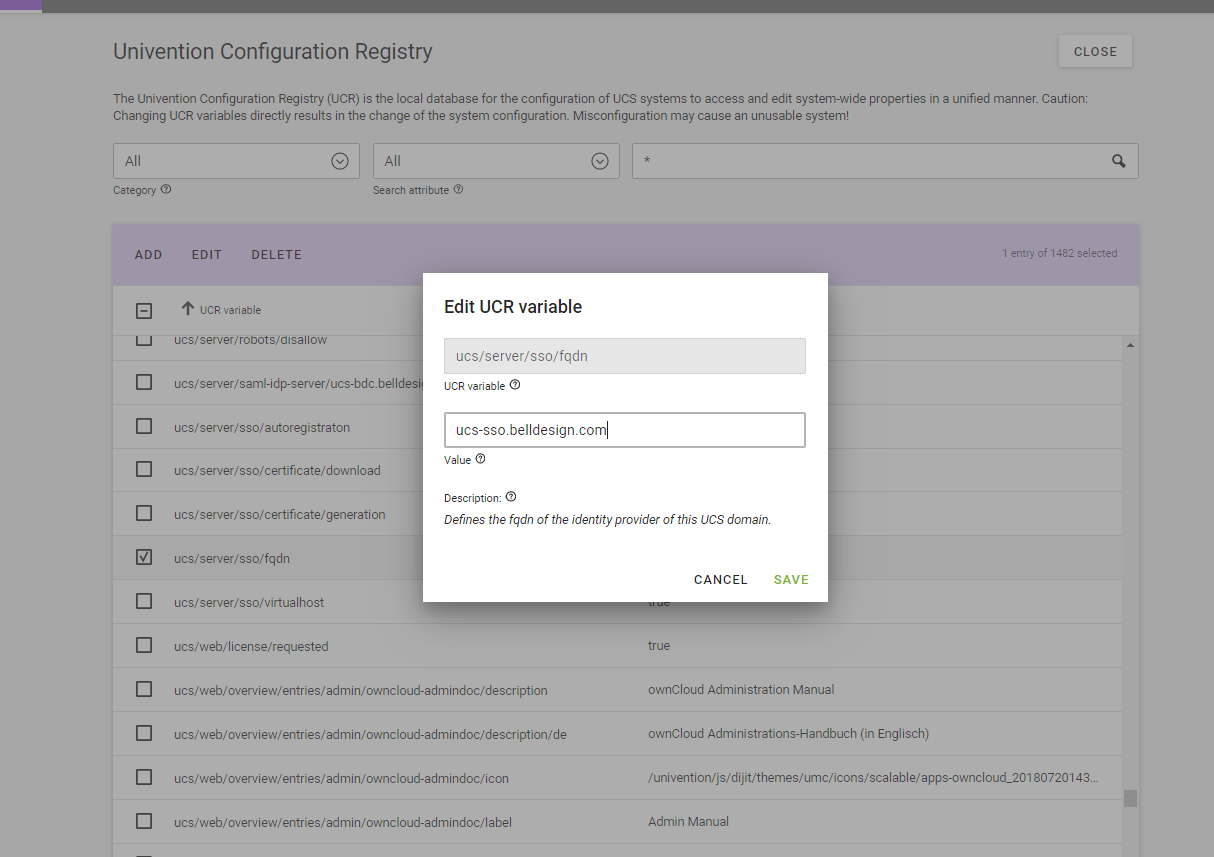
System Diagnostic Tool -
Problem:SAML certificate verification failed
UCS Version
4.4-1 errata290 (Blumenthal)
UMC Version
11.0.4-36A~4.4.0.201909050927
Date of expiry of the SSL root certificate
August 25, 2023 at
Date of expiry of the SSL certificate for this system
August 25, 2023 at
This occurred after a
Error:
Traceback (most recent call last):
File "/usr/lib/pymodules/python2.7/univention/management/console/modules/diagnostic/__init__.py", line 280, in execute
result = execute(umc_module, **kwargs)
File "/usr/lib/pymodules/python2.7/univention/management/console/modules/diagnostic/plugins/04_saml_certificate_check.py", line 76, in run
test_identity_provider_certificate()
File "/usr/lib/pymodules/python2.7/univention/management/console/modules/diagnostic/plugins/04_saml_certificate_check.py", line 89, in test_identity_provider_certificate
for host in socket.gethostbyname_ex(sso_fqdn)[2]:
gaierror: [Errno -2] Name or service not known
I looked at the conf. file in etc/apache2/univention-saml.conf and noticed it lists the ucs domain name and not the FQDN which I have been using … should this be changed to the FQDN?
# Warning: This file is auto-generated and might be overwritten by
# univention-config-registry.
# Please edit the following file(s) instead:
# Warnung: Diese Datei wurde automatisch generiert und kann durch
# univention-config-registry ueberschrieben werden.
# Bitte bearbeiten Sie an Stelle dessen die folgende(n) Datei(en):
#
# /etc/univention/templates/files/etc/apache2/sites-available/univention-saml.conf
#
Alias /simplesamlphp/saml2/idp/certificate /etc/simplesamlphp/ucs-sso.belldesign.com-idp-certificate.crt
<Directory "/etc/simplesamlphp">
<Files "ucs-sso.belldesign.com-idp-certificate.crt">
Require all granted
</Files>
</Directory>
Alias /simplesamlphp /usr/share/simplesamlphp/www
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteRule ^/?simplesamlphp/(.*) https://%{SERVER_NAME}/simplesamlphp/$1 [R,L]
<Directory /usr/share/simplesamlphp/www/>
<FilesMatch ".+\.ph(p[345]?|t|tml)$">
SetHandler php-cgi
</FilesMatch>
Action php-cgi /saml-bin/php-cgi
Order allow,deny
Allow from all
</Directory>
<Directory /var/www/saml/>
Options -Indexes
</Directory>
<IfModule mod_ssl.c>
<VirtualHost *:443>
IncludeOptional /etc/apache2/sso-vhost.conf.d/*.conf
SSLEngine on
SSLProxyEngine on
ServerName ucs-sso.belldesign.com
SSLCertificateFile /etc/univention/ssl/ucs-sso.belldesign.com/cert.pem
SSLCertificateKeyFile /etc/univention/ssl/ucs-sso.belldesign.com/private.key
SSLCACertificateFile /etc/univention/ssl/ucsCA/CAcert.pem
DocumentRoot /var/www/
RedirectMatch ^/$ /simplesamlphp/
ScriptAlias /saml-bin /var/www/saml
SuexecUserGroup samlcgi samlcgi
RewriteEngine on
RewriteCond %{HTTP:Authorization} !^$
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization},L]
Include /etc/apache2/sites-available/univention-proxy.conf
</VirtualHost>
<VirtualHost *:80>
IncludeOptional /etc/apache2/sso-vhost.conf.d/*.conf
ServerName ucs-sso.belldesign.com
DocumentRoot /var/www/
RedirectMatch ^/$ /simplesamlphp/
ScriptAlias /saml-bin /var/www/saml
SuexecUserGroup samlcgi samlcgi
RewriteEngine on
RewriteCond %{HTTP:Authorization} !^$
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization},L]
Include /etc/apache2/sites-available/univention-proxy.conf
</VirtualHost>
</IfModule>