Hello,
I’have setup a lab and install OpenVPN on my UCS 192.168.10.2 server.
I’m connected to the VPN but i can’t ping other servers of the LAN
there is my home network 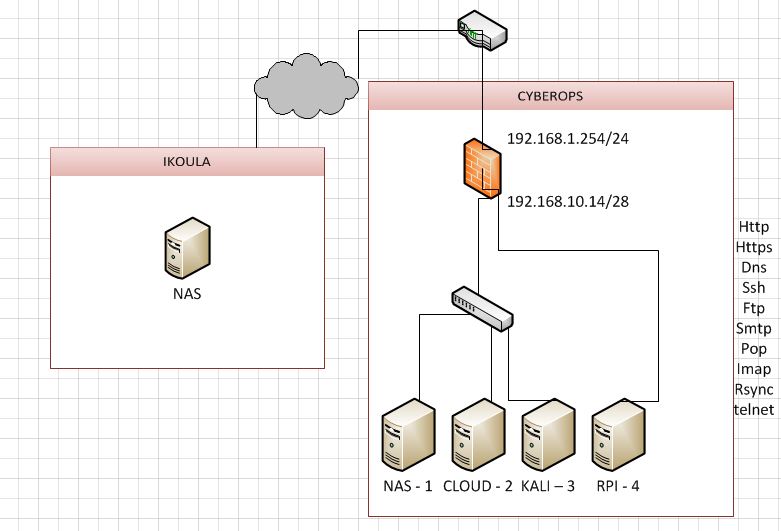
the tunnel is : 192.168.8.0/28 and the lan is 192.168.10.0/28
when im connected i can ping the UCS server but i can’t ping my kali or my nas ?!
do i need to create iptables rules like this guy : Openvpn4ucs cannot access LAN resource ?
linuxly
If you don’t do NAT on your VPN endpoint, the following happens:
- Your client, which has a private IP address on the VPN adapter, sends a ping to e.g.
kali-3 with the source address of that private network used solely between the VPN client and the VPN server.
- The server forwards that packet as-is to the local LAN.
- The packet arrives at
kali-3 which sends a reply to the packet’s source address, which is that private IP from that private VPN.
-
kali-3 doesn’t have any special knowledge/no route for that VPN network and sends the request to its default gateway, which is your router.
- Your router doesn’t have a special route for that VPN network either and discards the packet.
There are several possible solutions to this problem:
- On your VPN server: use a NAT firewall rule to rewrite the source address of all packets coming from the VPN to the source address of your VPN server’s local LAN interface. That way
kali-3 will think the request came from your VPN server and send its reply back to the VPN server. The VPN server will recognize that this is a reply to a packet with a rewritten source address, reverse the process and pass the reply on to your VPN client.
- On
kali-3: add a network route to the VPN network with gateway being your VPN server. This will fix kali-3, but none of the other servers.
- On your router: add a network route to the VPN network with gateway being your VPN server. This will fix it for all machines on your LAN.
Another possibility why it doesn’t work is that your VPN server might have IP routing/IP forwarding deactivated.
1 Like
ok i will try to do a route on the router/firewall
the router do nat 192.168.1.254 (outsite)
on my router i will add
src | mask | interface destination
192.168.8.0 | /28 | 192.168.10.14
10.14 is the lan interface
