hi,
thanks for your ideas, which i´ve tried today:
@damrose: i worked through the whole list and everythings seems to work fine:
- UCR variable is changed
- SAML identity provider shows up in Intranet Sites in the IE settings
root@dc:/var/log/apache2# univention-check-templates 2>&1 | egrep "(apache|saml)"
root@dc:/var/log/apache2#
root@dc:/var/log/apache2# ktutil --keytab=/etc/simplesamlphp.keytab list
/etc/simplesamlphp.keytab:
Vno Type Principal Aliases
2 des-cbc-crc HTTP/ucs-sso.domain.ltd@domain.ltd
2 des-cbc-crc ucs-sso@domain.ltd
2 des-cbc-md5 HTTP/ucs-sso.domain.ltd@domain.ltd
2 des-cbc-md5 ucs-sso@domain.ltd
2 arcfour-hmac-md5 HTTP/ucs-sso.domain.ltd@domain.ltd
2 arcfour-hmac-md5 ucs-sso@domain.ltd
2 aes128-cts-hmac-sha1-96 HTTP/ucs-sso.domain.ltd@domain.ltd
2 aes128-cts-hmac-sha1-96 ucs-sso@domain.ltd
2 aes256-cts-hmac-sha1-96 HTTP/ucs-sso.domain.ltd@domain.ltd
2 aes256-cts-hmac-sha1-96 ucs-sso@domain.ltd
1 des3-cbc-sha1 HTTP/ucs-sso.domain.ltd@domain.ltd
1 des-cbc-md4 HTTP/ucs-sso.domain.ltd@domain.ltd
1 arcfour-hmac-md5 HTTP/ucs-sso.domain.ltd@domain.ltd
1 aes128-cts-hmac-sha1-96 HTTP/ucs-sso.domain.ltd@domain.ltd
1 aes256-cts-hmac-sha1-96 HTTP/ucs-sso.domain.ltd@domain.ltd
1 des-cbc-md5 HTTP/ucs-sso.domain.ltd@domain.ltd
1 des-cbc-crc HTTP/ucs-sso.domain.ltd@domain.ltd
1 des3-cbc-sha1 HTTP/ucs-sso.domain.ltd@domain.ltd
1 des-cbc-md4 HTTP/ucs-sso.domain.ltd@domain.ltd
1 arcfour-hmac-md5 HTTP/ucs-sso.domain.ltd@domain.ltd
1 aes128-cts-hmac-sha1-96 HTTP/ucs-sso.domain.ltd@domain.ltd
1 aes256-cts-hmac-sha1-96 HTTP/ucs-sso.domain.ltd@domain.ltd
1 des-cbc-md5 HTTP/ucs-sso.domain.ltd@domain.ltd
1 des-cbc-crc HTTP/ucs-sso.domain.ltd@domain.ltd
root@dc:/var/log/apache2#
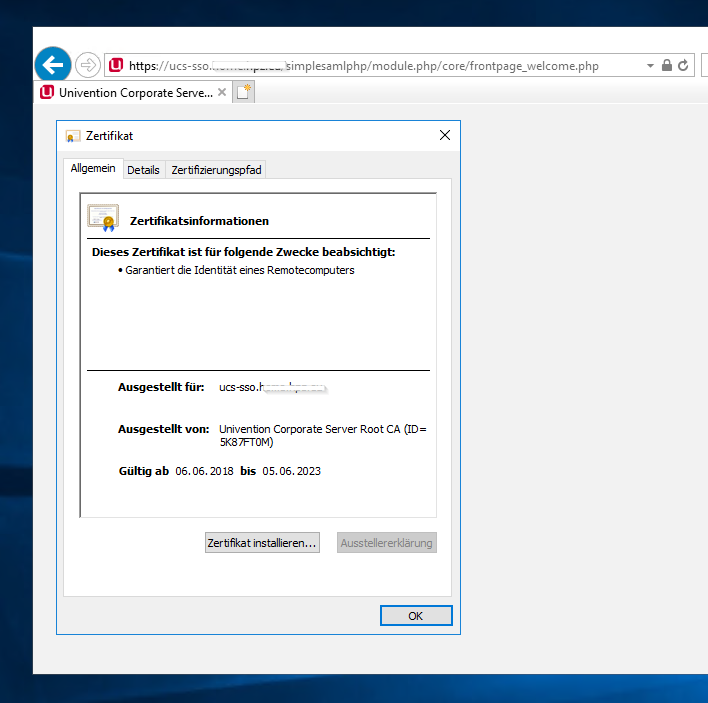
Then i make a test and call the website ucs-sso.domain.ltd on my domain-joined client.
I logged in with my user, the url is changing to https://domain.ltd/simplesamlphp/module.php/core/frontpage_welcome.php and i get an 404 error page!
Content of my access.log and error.log:
access,log:
192.168.24.80 - - [15/Oct/2018:10:23:12 +0200] "POST /univention/auth HTTP/1.1" 200 854 "https://domain.ltd/univention/login/?location=%2Fsimplesamlphp%2Fmodule.php%2Fcore%2Ffrontpage_welcome.php&lang=de-AT" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko"
192.168.24.80 - - [15/Oct/2018:10:23:12 +0200] "GET /univention/get/meta?1539591792481 HTTP/1.1" 200 1821 "https://domain.ltd/univention/login/?location=%2Fsimplesamlphp%2Fmodule.php%2Fcore%2Ffrontpage_welcome.php&lang=de-AT" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko"
192.168.24.80 - - [15/Oct/2018:10:23:12 +0200] "GET /simplesamlphp/module.php/core/frontpage_welcome.php HTTP/1.1" 404 642 "https://domain.ltd/univention/login/?location=%2Fsimplesamlphp%2Fmodule.php%2Fcore%2Ffrontpage_welcome.php&lang=de-AT" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko"
error.log:
[Mon Oct 15 10:21:58.779236 2018] [autoindex:error] [pid 7063] [client 192.168.24.80:64103] AH01276: Cannot serve directory /var/www/univention/js/umc/: No matching DirectoryIndex (index.html,index.cgi,index.pl,index.php,index.xhtml,index.htm) found, and server-generated directory index forbidden by Options directive, referer: https://domain.ltd/univention/login/?location=%2Funivention%2Fself-service%2F%23passwordreset&lang=de-AT
[Mon Oct 15 10:22:59.134915 2018] [autoindex:error] [pid 7066] [client 192.168.24.80:64138] AH01276: Cannot serve directory /var/www/univention/js/umc/: No matching DirectoryIndex (index.html,index.cgi,index.pl,index.php,index.xhtml,index.htm) found, and server-generated directory index forbidden by Options directive, referer: https://domain.ltd/univention/login/?location=%2Fsimplesamlphp%2Fmodule.php%2Fcore%2Ffrontpage_welcome.php&lang=de-AT