I only have one UCS server with master role. And not running any Let’s Ecrypt.
I have some more feedback… no solution however 
-
After restart, i’m able to sso using internet explorer in every servers (backup and slaves) the only server that sso isn’t working is the domainmaster
After sso with internet explorer i cannot sso using chrome. -
After restart, and try with chrome: i’m able to sso in every servers (backup and slaves) the only server that sso isn’t working is the domainmaster.
After sso with chrome i cannot sso using internet explorer
Again i don’t know if that is the expected behaviour or not… but is what happen on my side
@hpz do you have more ucs servers configured? (slave or backups) so you can try sso in that servers?
hi,
no, one single ucs master.
@hpz are you able to find the “blank.json”
still the same as written before…
@hpz yep… i also don’t have that file i none os my servers… cannot understand why the sso don’t work in domainmaster
Little thumb up this post…
Anyone can help/guide how to troubleshoot the sso and why it don’t work in the domaincontroller_master but works fine in all other servers roles (backup and slaves)
Could this be related ?
The sso address is avaible via two servers (master and backup) and the windows client trying the sso via the domaincontroller_master portal the first server that respond to the sso fqdn is the ip from the backup server?
Hi there,
I had the same problem. I did the following:
univention-run-join-scripts --force --run-scripts 98univention-samba4-saml-kerberos.inst
univention-run-join-scripts --force --run-scripts 91univention-saml.inst
# In this order, it might be a bug because the password get changed in the 98 script and I got
# an invalid password error with the next command
kinit -t /etc/simplesamlphp.keytab HTTP/ucs-sso.$(ucr get domainname)@$(ucr get kerberos/realm)
# And last but not least the following, because I got an invalid certificate error under
# https://afdc.af.intra/univention/saml/
univention-run-join-scripts --force --run-scripts 92univention-management-console-web-server.inst
After that, I was able to use my client’s kerberos ticket to login.
@damrose
There might be a Bug in the guide under: Debugging the SAML Kerbeors authentication
The 98 script changes the password of the ucs-sso user and I feel like this invalidates all tickets in the samlkeytab file. So maybe the order must be 98 and then 91, but I’am not a 100% sure.
@go2sh do you run the commands in master only or in all the servers?
Thanks
Master only as I have only one server, which is also the ucs-sso server.
@go2sh well my problem is really in the master, but all others servers work fine with sso
@codedmind Mine too. My master wasn’t able to use single-singon. Can you try to open the following page:
https://{master-dns}/univention/saml
@go2sh it will ask for login. if i went to the same url but slave-dns it works (sso)
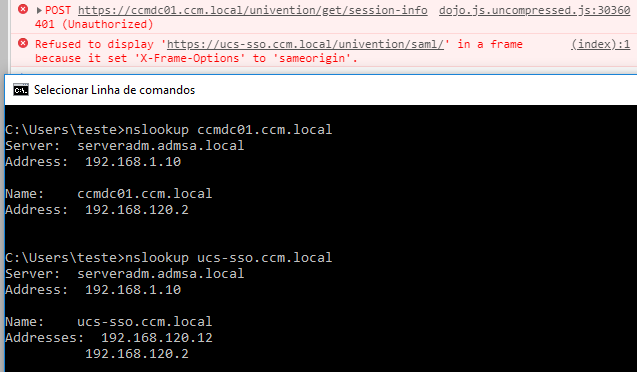
This doesn’t work
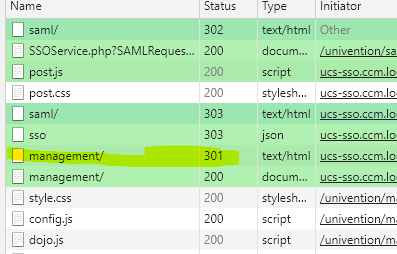
This works
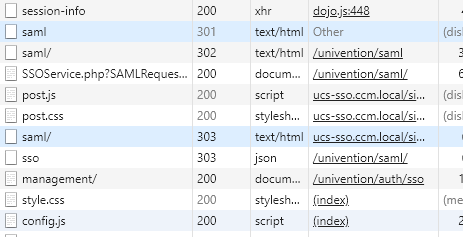
Don0t know if this matters but the first print i two management/ one 301 then other 200 in the second only get one management/ with the 200 code
Can you check your ucr variable saml/idp/authsource on the master if it is univention-negotiate. This would be the only thing I could imagine.
@go2sh yep is univention- negotiate
![]()