I have configured a UCS server as my Primary Domain Controller. I have configured a CentOS 7 server that I would like to make a File and Print Server for this Domain. When configuring I have selected the options for GUI, File server, and Print Server. I have successfully joined it to the UCS domain. I am trying to log into the server with other users that I have created in the users OU. I can log in with a user I created in AD on my windows laptop after joining it to the domain. When I try logging in on the server to test user authentication is working it doesn’t let me. Can someone help me get this to work?
Hi,
I can not see from your post which methods you used for logging in to the CentOS machine.
As far as I know joining Linux machines to an UCS domain only configures authentication for console and ssh login.
I havent used CentOS for file/print for a while as UCS already provides this service without additional configuration. But I would expect that one has to (and can) configure Kerberos or LDAP auth on CentOS too and it should be mentioned in the CentOS docs.
Best Regards,
Dirk Ahrnke
Sorry for the delayed response…
Let me start over…
I have configured a UCS “Univention Corporate Server” to run as an LDAP server as the Primary domain controller.
I have been able to connect a Windows 10 desktop client to the domain, after connecting my Windows PC to the domain I am able to successfully test with a user that I created on the UCS.
What I am trying to do is connect a CentOS 7 server to the domain and configure it’s LDAP client to use the Users and Groups from the UCS LDAP.
I am STUCK HERE: I have successfully joined the domain with the CentOS 7 server, but when I try to login using another account that is in LDAP on the UCS I cannot. I am trying to login vi GUI console or ssh neither work.
I must be onto something. Now when I try to login on the centos server using domainname\domainusername the centos server appears to try to connect. The dial just spins forever. I can cancel it, so it isn’t stuck and it doesn’t quickly fail like it used to. The last few things I remember doing to get to this point was blog.zwiegnet.com/linux-server/c … ap-client/ then I opened port 7389 tcp on the firewall.
I would compare the steps you did with Chapter 2. Integration of Linux/Unix systems into a UCS domain.
Before you replied this morning I ran tail /var/log/messages. I received the following error …nslcd[7102]: [ed1e8c] <group/member=“gdm”> ldap_result() failed: Operations error: 00002020: Operation unavailable without authentication
Hi glassknight,
i did some research and tests.
The log-message you posted
did also appear on my test-system when i tried to authenticate against the DC with nslcd.
Please do not use authconfig-tui anymore.
man authconfig
...
NOTES
The authconfig-tui is deprecated. No new configuration settings will be supported by its text user interface. Use system-config-authentication GUI application or the command line options instead.
...
What i have done was looking for the link ahrnke posted. There is a guide for Ubuntu which can be adapted for CentOS. Here are my steps:
#!/bin/bash
# Set IP of Domain-Controller
export MASTER_IP=xxx.xxx.xxx.xxx
mkdir /etc/univention
ssh -n root@${MASTER_IP} 'ucr shell | grep -v ^hostname=' >/etc/univention/ucr_master
echo "master_ip=${MASTER_IP}" >>/etc/univention/ucr_master
chmod 660 /etc/univention/ucr_master
. /etc/univention/ucr_master
echo "${MASTER_IP} ${ldap_master}" >>/etc/hosts
wget -O /etc/openldap/cacerts/CAcert.pem \
http://${ldap_master}/ucs-root-ca.crt
# Create an account and save the password
yum install -y sssd redhat-lsb-core authconfig-gtk
password="$(tr -dc A-Za-z0-9_ </dev/urandom | head -c20)"
ssh -n root@${ldap_master} udm computers/linux create \
--position "cn=computers,${ldap_base}" \
--set name=$(hostname) --set password="${password}" \
--set operatingSystem="$(lsb_release -is)" \
--set operatingSystemVersion="$(lsb_release -rs)"
printf '%s' "$password" >/etc/ldap.secret
chmod 0400 /etc/ldap.secret
# Create ldap.conf
cat >/etc/openldap/ldap.conf <<__EOF__
TLS_CACERT /etc/openldap/cacerts/CAcert.pem
URI ldap://$ldap_master:7389
BASE $ldap_base
__EOF__
# sssd
cat >/etc/sssd/sssd.conf <<___EOF___
[sssd]
config_file_version = 2
reconnection_retries = 3
sbus_timeout = 30
services = nss, pam, sudo
domains = $kerberos_realm
[nss]
reconnection_retries = 3
[pam]
reconnection_retries = 3
[domain/$kerberos_realm]
auth_provider = krb5
krb5_kdcip = ${master_ip}
krb5_realm = ${kerberos_realm}
krb5_server = ${ldap_master}
krb5_kpasswd = ${ldap_master}
id_provider = ldap
ldap_uri = ldap://${ldap_master}:7389
ldap_search_base = ${ldap_base}
ldap_tls_reqcert = never
ldap_tls_cacert = /etc/openldap/cacerts/CAcert.pem
cache_credentials = true
enumerate = true
ldap_default_bind_dn = cn=$(hostname),cn=computers,${ldap_base}
ldap_default_authtok_type = password
ldap_default_authtok = $(cat /etc/ldap.secret)
___EOF___
chmod 600 /etc/sssd/sssd.conf
systemctl start sssdAt this point you should see your all domain-users with “getent passwd”
Then login via GUI (i did with Gnome) and start: Applications -> Sundry -> Authentication.
Configuration should lock like that:

On the 2nd tab (Advanced Options) i disabled “fingerprint reader support” and enabled “Create home directories on first login”.
Apply your Changes.
Logout and login with a domain-user.
Output of “authconfig --test”
caching is disabled
nss_files is always enabled
nss_compat is disabled
nss_db is disabled
nss_hesiod is disabled
hesiod LHS = ""
hesiod RHS = ""
nss_ldap is enabled
LDAP+TLS is enabled
LDAP server = "ldap://ucs-6450.example.com:7389"
LDAP base DN = "dc=example,dc=com"
nss_nis is disabled
NIS server = ""
NIS domain = ""
nss_nisplus is disabled
nss_winbind is disabled
SMB workgroup = "MYGROUP"
SMB servers = ""
SMB security = "user"
SMB realm = ""
Winbind template shell = "/bin/false"
SMB idmap range = "16777216-33554431"
nss_sss is enabled by default
nss_wins is disabled
nss_mdns4_minimal is disabled
DNS preference over NSS or WINS is disabled
pam_unix is always enabled
shadow passwords are enabled
password hashing algorithm is sha512
pam_krb5 is enabled
krb5 realm = "EXAMPLE.COM"
krb5 realm via dns is disabled
krb5 kdc = ""
krb5 kdc via dns is enabled
krb5 admin server = ""
pam_ldap is disabled
LDAP+TLS is enabled
LDAP server = "ldap://ucs-6450.example.com:7389"
LDAP base DN = "dc=example,dc=com"
LDAP schema = "rfc2307"
pam_pkcs11 is disabled
use only smartcard for login is disabled
smartcard module = ""
smartcard removal action = ""
pam_fprintd is disabled
pam_ecryptfs is disabled
pam_winbind is disabled
SMB workgroup = "MYGROUP"
SMB servers = ""
SMB security = "user"
SMB realm = ""
pam_sss is disabled by default
credential caching in SSSD is enabled
SSSD use instead of legacy services if possible is enabled
IPAv2 is disabled
IPAv2 domain was not joined
IPAv2 server = ""
IPAv2 realm = ""
IPAv2 domain = ""
pam_pwquality is enabled (try_first_pass local_users_only retry=3 authtok_type=)
pam_passwdqc is disabled ()
pam_access is disabled ()
pam_mkhomedir or pam_oddjob_mkhomedir is enabled (umask=0077)
Always authorize local users is enabled ()
Authenticate system accounts against network services is disabledbefore I get to the …“getent passwd”… As the script runs everything looks good until I get E: Invalid Syntax: Hostname: This is not a valid hostname.
Why do I get E: Invalid Syntax: Hostname: This is not a valid hostname.?
Here is a copy of the output log I generated:
Loaded plugins: fastestmirror, langpacks
Loading mirror speeds from cached hostfile
- base: mirror.umd.edu
- extras: mirror.umd.edu
- updates: mirrors.mit.edu
Package sssd-1.13.0-40.el7_2.12.x86_64 already installed and latest version
Package redhat-lsb-core-4.1-27.el7.centos.1.x86_64 already installed and latest version
Package authconfig-gtk-6.2.8-10.el7.x86_64 already installed and latest version
Nothing to do
E: Invalid Syntax: Hostname: This is not a valid hostname.
Am I supposed to change where it says host name in the script or do I need to install an app on UCS or Configure DNS on the client?
Hi glassknight,
i had the same error.
In my case i set the hostname of the client-system “wrong”, during the installation.
root@centos:~$ cat /etc/hostname
centos.example.com
Remove “.example.com” from the hostname.
After that, delete the directory “/etc/univention”, and run the script again.
Also look at “/etc/hosts” and delete multipe entrys of your DC, after running the script.
It appears to have connected, but I do not see all of the domain usernames and password using getent passwd.
Also under authentication, I see you need to select TLS. Do I have to download a CA Certificate from the UCS?
This is my authconfig --test
caching is disabled
nss_files is always enabled
nss_compat is disabled
nss_db is disabled
nss_hesiod is disabled
hesiod LHS = “”
hesiod RHS = “”
nss_ldap is enabled
LDAP+TLS is enabled
LDAP server = “ldap://mydcs.mydomain.myextension:7389”
LDAP base DN = “dc=mydomain,dc=myextension”
nss_nis is disabled
NIS server = “”
NIS domain = “”
nss_nisplus is disabled
nss_winbind is disabled
SMB workgroup = “MYDOMAIN”
SMB servers = “”
SMB security = “USER”
SMB realm = “MYDOMAIN.MYEXTENSION”
Winbind template shell = “/bin/false”
SMB idmap range = “16777216-33554431”
nss_sss is enabled by default
nss_wins is disabled
nss_mdns4_minimal is disabled
DNS preference over NSS or WINS is disabled
pam_unix is always enabled
shadow passwords are enabled
password hashing algorithm is sha512
pam_krb5 is enabled
krb5 realm = “MYDOMAIN.MYEXTENSION”
krb5 realm via dns is disabled
krb5 kdc = “”
krb5 kdc via dns is enabled
krb5 admin server = “”
pam_ldap is disabled
LDAP+TLS is enabled
LDAP server = “ldap://mydcs.mydomain.myextension:7389”
LDAP base DN = “dc=mydomain,dc=myextension”
LDAP schema = “rfc2307”
pam_pkcs11 is disabled
use only smartcard for login is disabled
smartcard module = “”
smartcard removal action = “”
pam_fprintd is disabled
pam_ecryptfs is disabled
pam_winbind is disabled
SMB workgroup = “MYDOMAIN”
SMB servers = “”
SMB security = “USER”
SMB realm = “MYDOMAIN.MYEXTENSION”
pam_sss is disabled by default
credential caching in SSSD is enabled
SSSD use instead of legacy services if possible is enabled
IPAv2 is disabled
IPAv2 domain was not joined
IPAv2 server = “”
IPAv2 realm = “”
IPAv2 domain = “”
pam_pwquality is enabled (try_first_pass local_users_only retry=3 authtok_type=)
pam_passwdqc is disabled ()
pam_access is disabled ()
pam_mkhomedir or pam_oddjob_mkhomedir is enabled (umask=0077)
Always authorize local users is enabled ()
Authenticate system accounts against network services is disabled
tail messages
Oct 11 13:40:01 myserver systemd: Started Session 116 of user root.
Oct 11 13:40:01 myserver systemd: Starting Session 116 of user root.
Oct 11 13:40:01 myserver systemd: Removed slice user-0.slice.
Oct 11 13:40:01 myserver systemd: Stopping user-0.slice.
Oct 11 13:50:01 myserver systemd: Created slice user-0.slice.
Oct 11 13:50:01 myserver systemd: Starting user-0.slice.
Oct 11 13:50:01 myserver systemd: Started Session 117 of user root.
Oct 11 13:50:01 myserver systemd: Starting Session 117 of user root.
Oct 11 13:50:01 myserver systemd: Removed slice user-0.slice.
Oct 11 13:50:01 myserver systemd: Stopping user-0.slice.
Are there any logs that would better help me trouble shoot what is not happening? Something to provide you with more info to help us get a faster resolution…
I am not sure if I found something or not…
On the member server “lwcfaps” in /etc/sssd I noticed these lines:
ldap_tls_reqcert = never
ldap_tls_cacert = /etc/openldap/cacerts/CAcert.pem
On the UCS server “lwcdcs” I ran this command to find where the CAcert.pem file resides:
# find / -name CAcert*
/etc/univention/ssl/ucsCA/CAcert.pem
/etc/univention/ssl.orig/ucsCA/CAcert.pem
1)On the lwcfaps server should ldap_tls_reqcert = never ?
a) Or should it be one of the following?
- When using security certificates in sssd.conf to authenticate ldap users, the ldap_tls_reqcert option can use one of several values to control how the ldap client uses these certs. The following definitions from the man page for ldap.conf explains the possible values. This value specifies what checks to perform on server certificates in a TLS session, if any.
The can be specified as one of the following keywords:
never - The client will not request or check any server certificate.
allow - The server certificate is requested. If no certificate is provided, the session proceeds normally. If a bad certificate is provided, it will be ignored and the session proceeds normally.
try - The server certificate is requested. If no certificate is provided, the session proceeds normally. If a bad certificate is provided, the session is immediately terminated.
demand | hard - These keywords are equivalent. The server certificate is requested. If no certificate is provided, or a bad certificate is provided, the session is immediately terminated. This is the default setting
-------------- So if testing the use of new certificates, try not to use the “allow” value. In this case, the client will ignore any problem found with the certificates, thus negating the use of this security feature.
2)I have listed the files in the directory /etc/openldap/cacerts/ on lwcfaps, and it is empty. Should there be something in that directory? Should the server copy the CAcert.pem from the lwcdcs (UCS Server)?
Please let me know if I have lost you or am losing you: I will continue to dig until I hear back from you  as I need to desperately get this working.
as I need to desperately get this working.
This morning I thought I would reread what the script you created for me was trying to do and where it might be going wrong… Please keep in mind I am very GREEN at linux, but I will learn it…
What I noticed in the script this morning was the following:
The first thing I saw was the last line…
systemctl start sssd
This means that the sssd service should be started and running…
so I decided to check the status of that service using
# service sssd status -l
Redirecting to /bin/systemctl status -l sssd.service
● sssd.service - System Security Services Daemon
Loaded: loaded (/usr/lib/systemd/system/sssd.service; enabled; vendor preset: disa
Drop-In: /etc/systemd/system/sssd.service.d
└─journal.conf
Active: active (running) since Thu 2016-10-13 17:41:18 EDT; 2 days ago
Process: 651 ExecStart=/usr/sbin/sssd -D -f (code=exited, status=0/SUCCESS)
Main PID: 699 (sssd)
CGroup: /system.slice/sssd.service
├─699 /usr/sbin/sssd -D -f
├─709 /usr/libexec/sssd/sssd_be --domain LWCOOPER.COM --uid 0 --gid 0 --de
├─710 /usr/libexec/sssd/sssd_be --domain default --uid 0 --gid 0 --debug-t
├─717 /usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --debug-to-files
├─718 /usr/libexec/sssd/sssd_sudo --uid 0 --gid 0 --debug-to-files
├─719 /usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --debug-to-files
└─720 /usr/libexec/sssd/sssd_autofs --uid 0 --gid 0 --debug-to-files
Oct 16 02:41:04 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unkno
Oct 16 03:13:13 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unkno
Oct 16 03:45:27 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unkno
Oct 16 04:17:32 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unkno
Oct 16 04:49:51 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unkno
Oct 16 05:22:19 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unkno
Oct 16 05:54:47 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unkno
Oct 16 06:26:58 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unkno
Oct 16 06:59:15 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unkno
Oct 16 07:31:23 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unkno
I saw that the service does not apear to be running, so I dug a little deeper…
The first few lines I notice are 11-14
[i]echo “${MASTER_IP} ${ldap_master}” >>/etc/hosts
wget -O /etc/openldap/cacerts/CAcert.pem
${ldap_master}/ucs-root-ca.crt[/i]
From what I know so far it looks like the script is desiegned to get the “CAcert.pem” which I noticed last night is not on my member server “lwcfaps”.
So I decided to manually run the wget command
wget -O /etc/openldap/cacerts/CAcert.pem 192.168.2.129/ucs-root-ca.crt
…the response I recieved…
[i]–2016-10-16 07:55:54-- 192.168.2.129/ucs-root-ca.crt
Connecting to 192.168.2.129:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 2053 (2.0K) [application/x-x509-ca-cert]
Saving to: ‘/etc/openldap/cacerts/CAcert.pem’
100%[===========================================>] 2,053 --.-K/s in 0s
2016-10-16 07:55:54 (302 MB/s) - ‘/etc/openldap/cacerts/CAcert.pem’ saved [2053/2053][/i]
It looks like it retrieved the cert!!!
I verified the directory /etc/openldap/cacerts/ by running # ls /etc/openldap/cacerts/
CAcert.pem is in the directory  !!!
!!!
I ran # service sssd status -l again and recieved the following response:
Redirecting to /bin/systemctl status -l sssd.service
● sssd.service - System Security Services Daemon
Loaded: loaded (/usr/lib/systemd/system/sssd.service; enabled; vendor preset: disabled)
Drop-In: /etc/systemd/system/sssd.service.d
└─journal.conf
Active: active (running) since Thu 2016-10-13 17:41:18 EDT; 2 days ago
Process: 651 ExecStart=/usr/sbin/sssd -D -f (code=exited, status=0/SUCCESS)
Main PID: 699 (sssd)
CGroup: /system.slice/sssd.service
├─699 /usr/sbin/sssd -D -f
├─709 /usr/libexec/sssd/sssd_be --domain LWCOOPER.COM --uid 0 --gid 0 --debug-to-files
├─710 /usr/libexec/sssd/sssd_be --domain default --uid 0 --gid 0 --debug-to-files
├─717 /usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --debug-to-files
├─718 /usr/libexec/sssd/sssd_sudo --uid 0 --gid 0 --debug-to-files
├─719 /usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --debug-to-files
└─720 /usr/libexec/sssd/sssd_autofs --uid 0 --gid 0 --debug-to-files
Oct 16 02:41:04 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unknown error
Oct 16 03:13:13 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unknown error
Oct 16 03:45:27 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unknown error
Oct 16 04:17:32 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unknown error
Oct 16 04:49:51 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unknown error
Oct 16 05:22:19 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unknown error
Oct 16 05:54:47 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unknown error
Oct 16 06:26:58 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unknown error
Oct 16 06:59:15 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unknown error
Oct 16 07:31:23 lwcfaps sssd[be[default]][710]: Could not start TLS encryption. unknown error

So I restarted the service running # service sssd restart and then # service sssd status -l to check status and I recieved:
"…● sssd.service - System Security Services Daemon
Loaded: loaded (/usr/lib/systemd/system/sssd.service; enabled; vendor preset: disabled)
Drop-In: /etc/systemd/system/sssd.service.d
└─journal.conf
Active: active (running) since Sun 2016-10-16 07:58:12 EDT; 12s ago
Process: 16216 ExecStart=/usr/sbin/sssd -D -f (code=exited, status=0/SUCCESS)
Main PID: 16218 (sssd)
CGroup: /system.slice/sssd.service
├─16218 /usr/sbin/sssd -D -f
├─16219 /usr/libexec/sssd/sssd_be --domain LWCOOPER.COM --uid 0 --gid 0 --debug-to-files
├─16220 /usr/libexec/sssd/sssd_be --domain default --uid 0 --gid 0 --debug-to-files
├─16223 /usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --debug-to-files
├─16224 /usr/libexec/sssd/sssd_sudo --uid 0 --gid 0 --debug-to-files
├─16225 /usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --debug-to-files
└─16226 /usr/libexec/sssd/sssd_autofs --uid 0 --gid 0 --debug-to-files
Oct 16 07:58:12 lwcfaps systemd[1]: Starting System Security Services Daemon…
Oct 16 07:58:12 lwcfaps sssd[16218]: Starting up
Oct 16 07:58:12 lwcfaps sssd[be[LWCOOPER.COM]][16219]: Starting up
Oct 16 07:58:12 lwcfaps sssd[be[default]][16220]: Starting up
Oct 16 07:58:12 lwcfaps sssd[autofs][16226]: Starting up
Oct 16 07:58:12 lwcfaps sssd[nss][16223]: Starting up
Oct 16 07:58:12 lwcfaps sssd[sudo][16224]: Starting up
Oct 16 07:58:12 lwcfaps sssd[pam][16225]: Starting up
Oct 16 07:58:12 lwcfaps systemd[1]: Started System Security Services Daemon.
"

I thought I would run # getent passwd to see if anything changed nope 
I also did return to the GUI and ran the Authentication Configuration I did what you told me but this time I also edited the path after clicking the Download CA Certificate I tried using "http://192.168.2.129/ucs-root-ca.crt" the same one I used above. It seemed like it worked… at least it was a good path… but # getent passwd did not show any different results after running it again…
I tried to rerun the entire script again as you stated previously, it looks like it runs, but I still cannot log in with a domain user and # getent passwd does not show an updated list 
Hi glassknight,
you haven’t lost me, but i had to do some other works and there was no time to respond to you.
Can you please tell me something more?
- Is “lwcfaps” a Virtual Machine?
- You are talking about “lwcfaps” as a member server, but my setup does not cover this cenario. Do you realy need a member-server?
- Is it possible for you to setup a fresh CentOS 7 installation and execute the “script”?
I will try to reproduce your error with “Could not start TLS encryption. unknown error”, over the weekend and answer you next week.
I understand, as long as I haven’t lost you, I can relax a bit lol :).
-
lwcfaps (file and print share) is a Virtual Machine and so is lwcdcs (UCS Domain Controller & LDAP)
-
Yes I would like to join lwcfaps to the domain. That would make it a member-server correct? The plan behind this is for me to manage users and permissions from one location for access and file sharing and more. I would also like to eventually add a mail server, a web server, and a backup server.
-
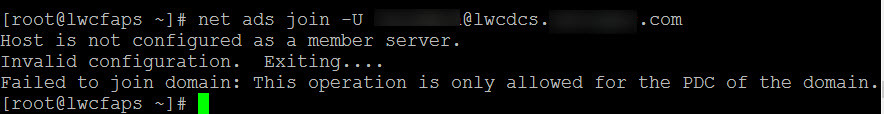
Coincidentally, before you responded with the script the first time I just reinstalled CentOS 7 with minimal installation. If you feel that something might be wrong I can bring it back to a fresh install. Would you like me to bring it back to a fresh install? If so, how do you recommend removing the server from the UCS, can I just go delete it from the OU?
For the record, I do not think I have this configured as a member server. My understanding of a member server is just a server that is connected to the domain? I might be wrong about this.