@Moritz_Bunkus
Is this that you ask?
root@CCMDC01:~# openssl s_client -connect ccmdc01.ccm.local:443 < /dev/null | openssl x509 -in - -noout -text | grep -A 2 Subject
depth=1 C = PT, ST = PT, L = PT, O = PT, OU = Univention Corporate Server, CN = Univention Corporate Server Root CA (ID=QbAo4rsE), emailAddress = ssl@ccm.local
verify return:1
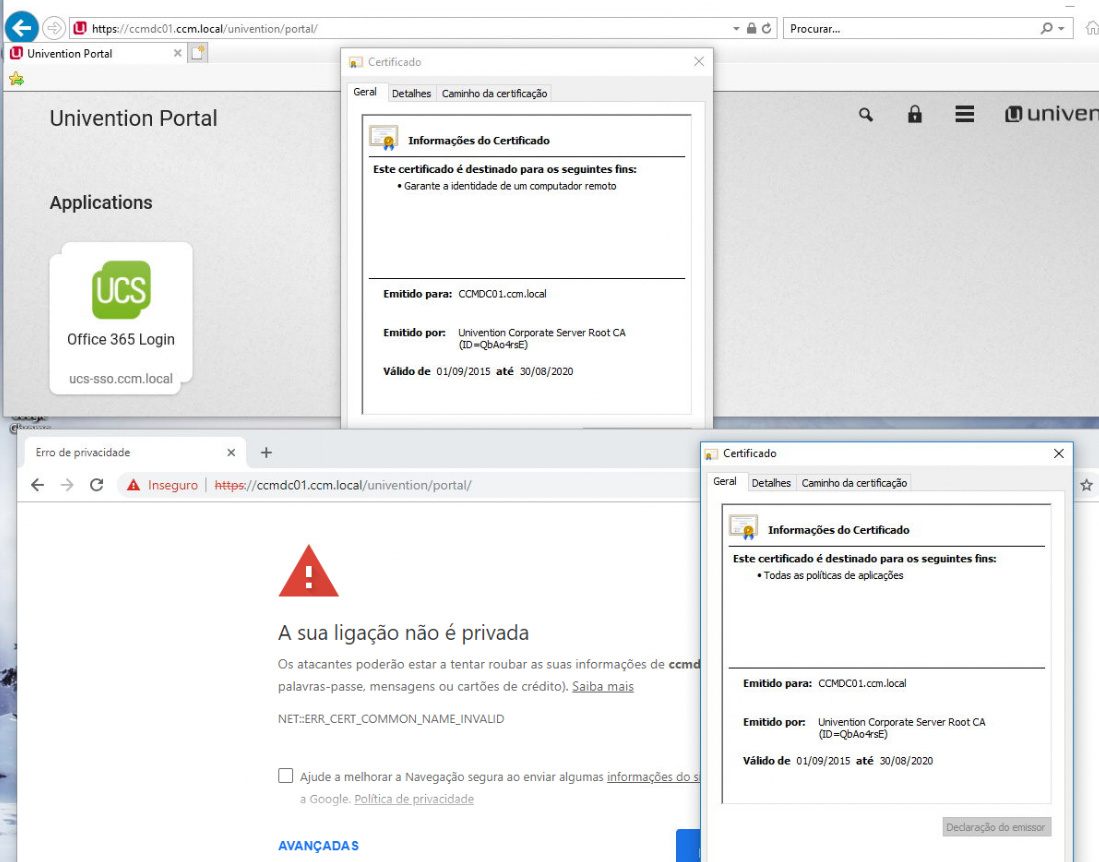
depth=0 C = PT, ST = PT, L = PT, O = PT, OU = Univention Corporate Server, CN = CCMDC01.ccm.local, emailAddress = ssl@ccm.local
verify return:1
DONE
Subject: C = PT, ST = PT, L = PT, O = PT, OU = Univention Corporate Server, CN = CCMDC01.ccm.local, emailAddress = ssl@ccm.local
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
--
X509v3 Subject Key Identifier:
7E:6C:8F:84:D7:2A:98:76:3E:FB:2B:83:A9:35:50:8B:F2:0D:E3:51
X509v3 Authority Key Identifier:
--
X509v3 Subject Alternative Name:
DNS:CCMDC01.ccm.local, DNS:CCMDC01
Signature Algorithm: sha256WithRSAEncryption
root@CCMDC01:~# openssl s_client -connect ccmdcbck.ccm.local:443 < /dev/null | openssl x509 -in - -noout -text | grep -A 2 Subject
depth=1 C = PT, ST = PT, L = PT, O = PT, OU = Univention Corporate Server, CN = Univention Corporate Server Root CA (ID=QbAo4rsE), emailAddress = ssl@ccm.local
verify return:1
depth=0 C = PT, ST = PT, L = PT, O = PT, OU = Univention Corporate Server, CN = CCMDCBCK.ccm.local, emailAddress = ssl@ccm.local
verify return:1
DONE
Subject: C = PT, ST = PT, L = PT, O = PT, OU = Univention Corporate Server, CN = CCMDCBCK.ccm.local, emailAddress = ssl@ccm.local
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
--
X509v3 Subject Key Identifier:
7B:4E:DC:CB:E7:C0:0D:9A:81:FC:AA:DD:A8:A1:2A:76:6E:A3:D4:62
X509v3 Authority Key Identifier:
--
X509v3 Subject Alternative Name:
DNS:CCMDCBCK.ccm.local, DNS:CCMDCBCK, DNS:f087ff41-af05-4fc4-b846-b2ee7c77f9d8._msdcs, DNS:f087ff41-af05-4fc4-b846-b2ee7c77f9d8._msdcs.ccm.local
Signature Algorithm: sha256WithRSAEncryption
root@CCMDC01:~#