Problem
The portal servers are only reachable in the intranet and the customer firewall only permits SSH connections on port 22.
Prerequisites
- We need a so-called “jump host” that we have SSH access to, which also has access to the UMC (default: port 443) of the target system
- TCP forwarding of arbitrary ports has to be allowed in the customer network:
setAllowTcpForwarding yesin /etc/ssh/sshd_config - firefox browser with the FoxyProxy-Addon
Solution
We will set up dynamic port forwarding and access the local SOCKS5 Proxy on Port 9091with FoxyProxy.
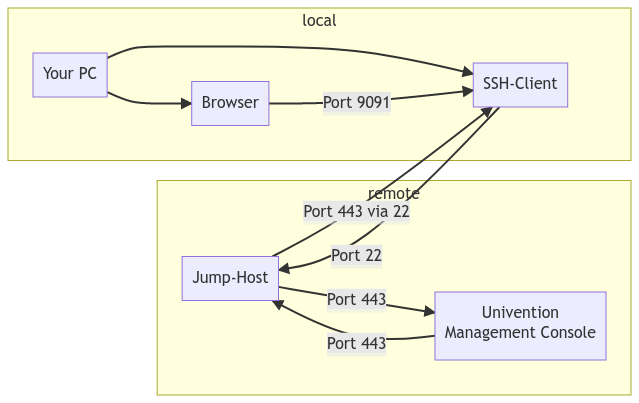
Set up SSH tunnel with dynamic port forwarding
For example, I have the following entry in my ~/.ssh/config
Host blockedumc.example.com
HostName 78.47.199.152
IdentityFile ~/.ssh/id_rsa
User friedrich
Port 22
GatewayPorts yes
DynamicForward 9091
Here I use 9091 as a dynamic port, you may choose another one as long as it is above 1024 (“privileged ports”).
Alternatively, you can do the same on CMDline:
ssh -N -D 9091 -i ~/.ssh/id_rsa friedrich@78.47.199.152
Output from ssh -N -v blockedumc.example.com:
debug1: Local connections to *:9091 forwarded to remote address socks:0
debug1: Local forwarding listening on 0.0.0.0 port 9091.
debug1: channel 0: new [port listener]
debug1: Local forwarding listening on :: port 9091.
With this, we already have an open SSH tunnel which locally listens for Proxy connections on port 9091!
Configure FoxyProxy
Right now, you could configure your browser to connect via the SOCKS-Proxy we just created. But this will send all your data through the SSH tunnel and you can’t access any other page .
Therefore, we configure FoxyProxy to dynamically switch the proxy connection on and off.
First, we add a new connection and set the Proxy IP to localhost and the Port to 9091 (the one we chose above):
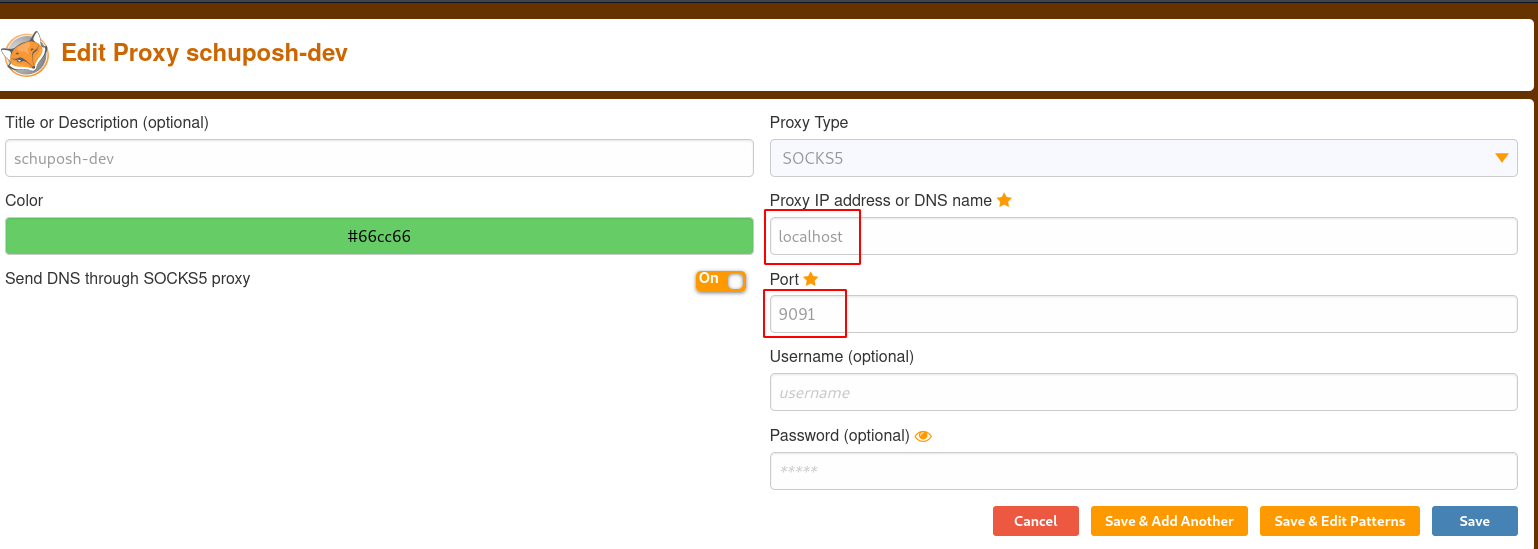
Then, we click on “Save and edit patterns” and configure some wildcard patterns:
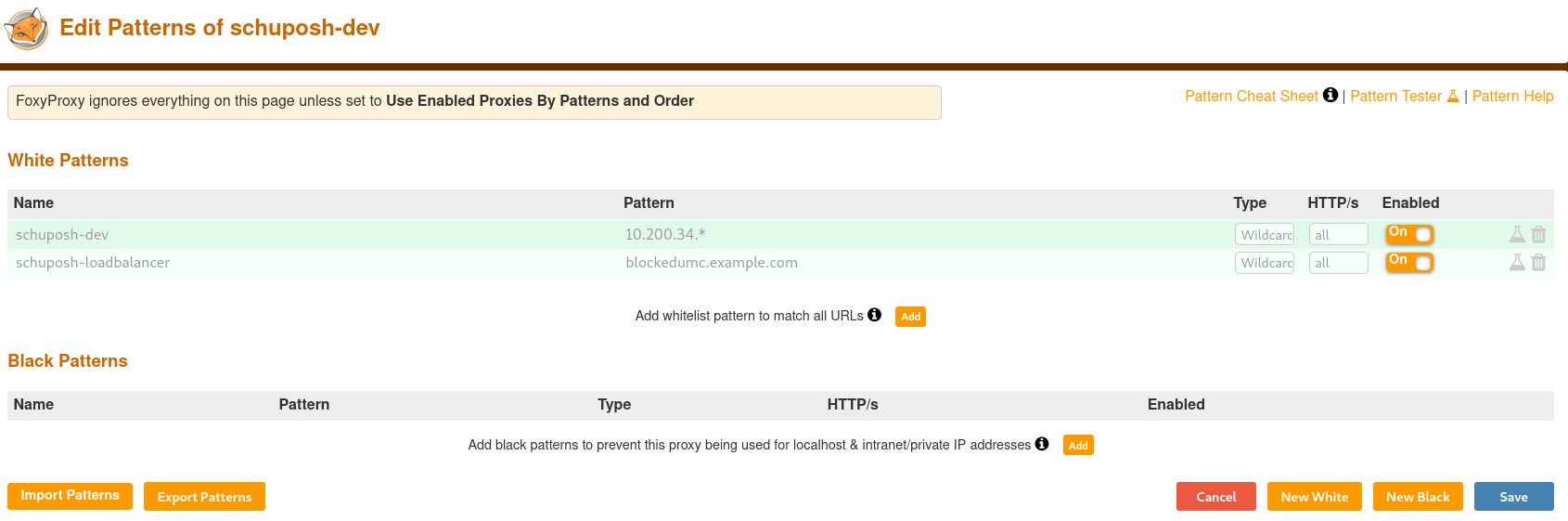
With a click on the small bottle on the right side of the pattern you can check it using the pattern tester.
Now activate the option Use enabled proxies by Patterns and Order in the FoxyProxy-Dropdown menu and you’re DONE!
If you visit, for example, the internal IP address 10.61.63.11, FoxyProxy detects the pattern and activates the connection via the SOCKS-Proxy for this IP.

