Hello guys.
Could anyone help me with GLPI configuration? I am trying to authenticate in UCS ldap base with no succes.
Hello guys.
Could anyone help me with GLPI configuration? I am trying to authenticate in UCS ldap base with no succes.
Can you show us a screenshot of the settings that can be made in GLPI and what you’ve entered there so far?
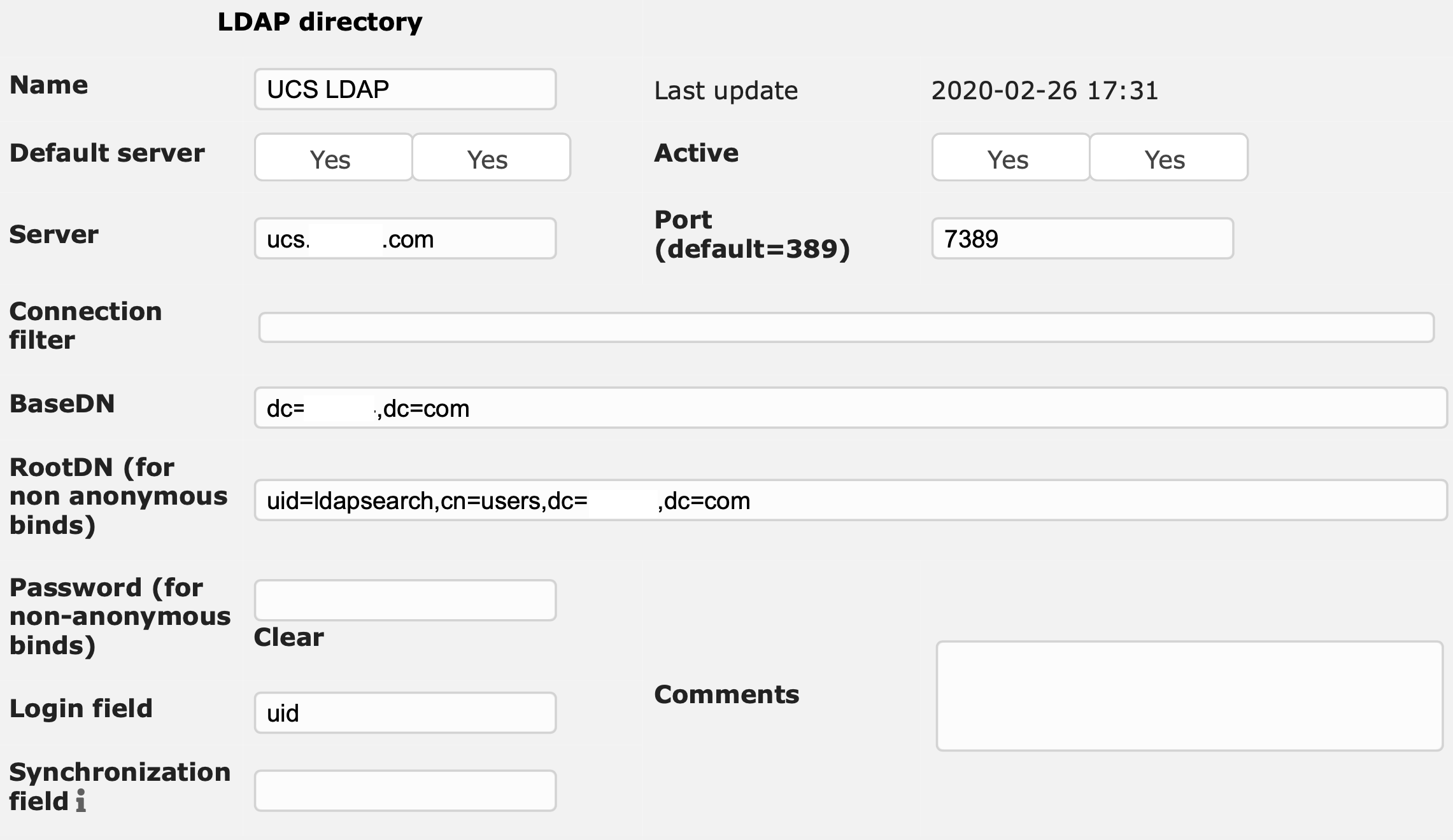
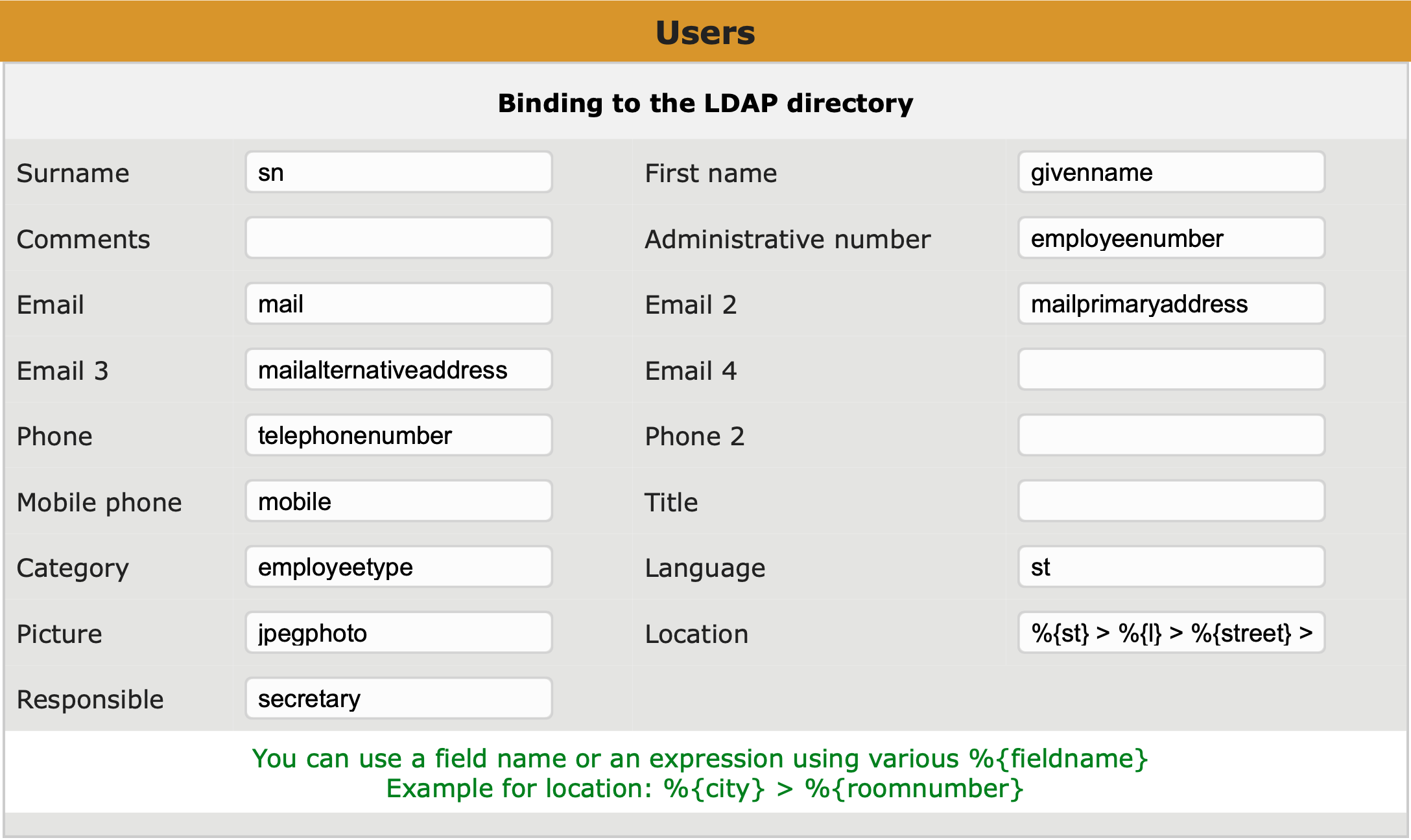
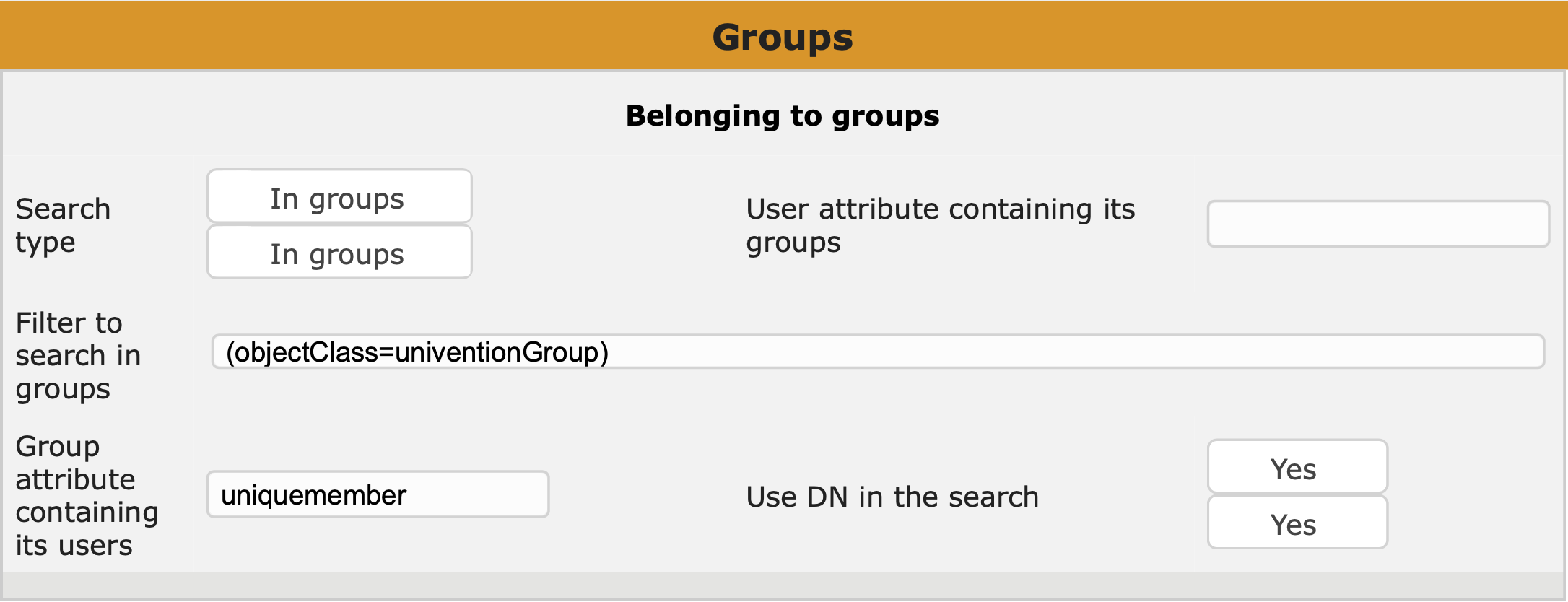
Always keep the following three points in mind when configuring a third-party application for access to the UCS LDAP:
ldapsearch just for this purpose. The format of the user name used to bind depends on the LDAP server you’re contacting: domain\username or username@f.q.dn should work with Samba 4 whereas you need the user name’s LDAP DN for the OpenLDAP server (e.g. uid=username,cn=users,dc=your,dc=domain).scp from the DC Master where it’s can be found in /etc/univention/ssl/ucsCA/CAcert.pem.memberOf which can be used in LDAP filters. OpenLDAP on the other hand stores group membership in the group object, not in the user object, and that you cannot filter for; the application has to handle OpenLDAP group membership on its own.…ok there are four important things to remember 
I could. This is AD pre-configuration.
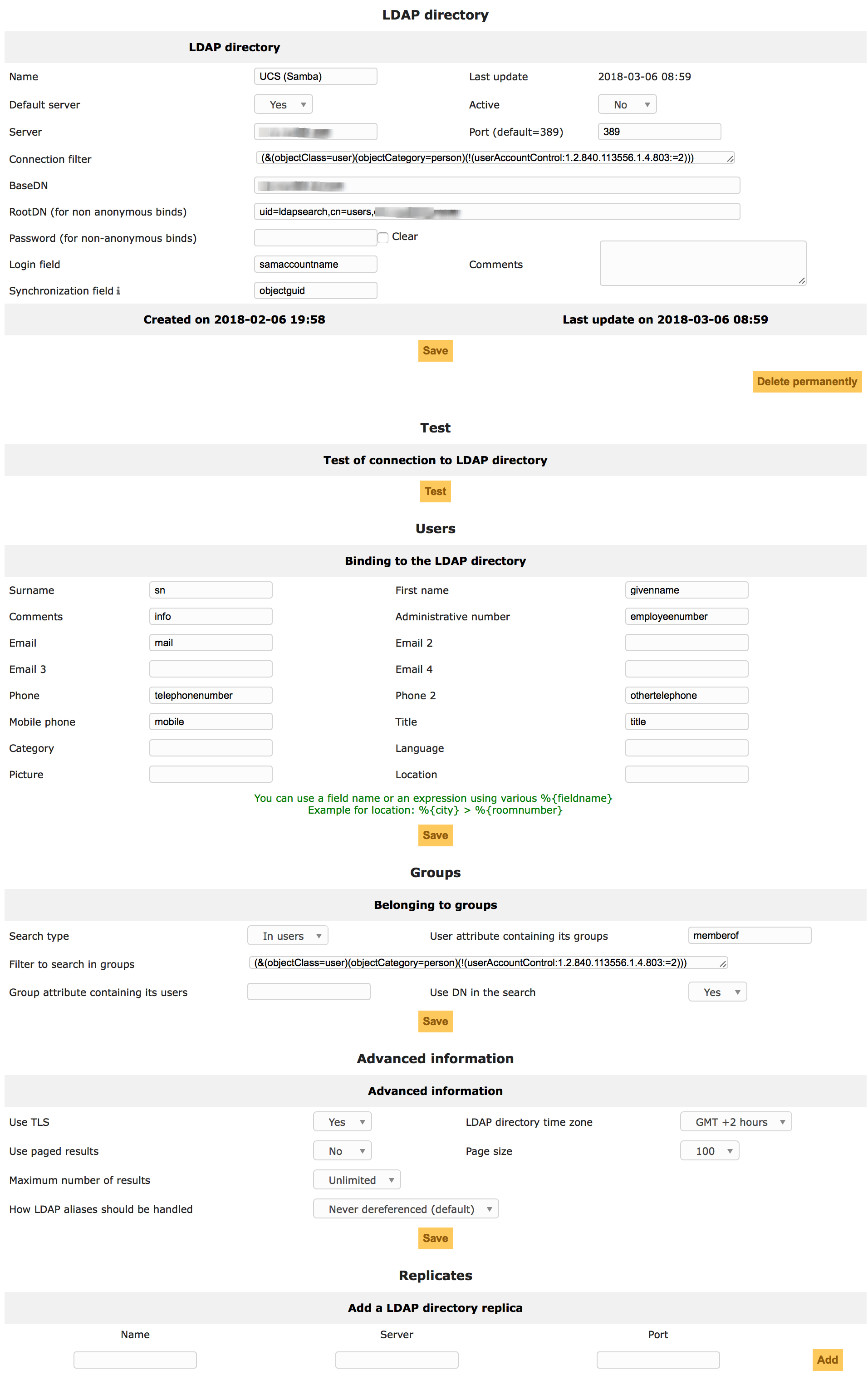
My test failed on encryption, but not yet checked the certs.
OpenLDAP works without encryption.
Hey,
your bind user’s DN uid=ldapsearch,cn=users,… is wrong for Samba. In OpenLDAP the user objects are indeed named uid=…, but in Samba’s LDAP they’re named cn=…. See univention-s4search samaccountname=ldapsearch dn for its actual DN.
Kind regards,
mosu
Got it almost working. Except on every 2nd or 3rd connection I’ve got an “Unable to start TLS” (retrying works).
OpenLDAP Settings for GLPI: