Hi all,
I’m trying to get the OwnCloud desktop client working with my UCS-based Kopano / OwnCloud server with the OpenID Connect Provider enabled. So far I found out that I had to register the appropriate client id and secret, which are specified here. I added these using the following command:
udm oidc/rpservice create \
--position cn=oidc,cn=univention,$(ucr get ldap/base) \
--set name=owncloud-desktop \
--set clientid=xdXOt13JKxym1B1QcEncf2XDkLAexMBFwiT9j6EfhhHFJhs2KM9jbjTmf8JBXE69 \
--set clientsecret=UBntmLjC2yYCeHwsyj73Uwo9TAaecAetRwMw0xYcvNL9yRdLSUi0hUAHfvCHFeFh \
--set trusted=yes \
--set applicationtype=native \
--set redirectURI=http://127.0.0.1
Note that the applicationtype here is native, which took me a while to figure out. It seems that only web and native are valid options? I had to reverse engineer these from error logging, it would be nice if an example of registering a native application was included in the OpenID Connect Provider readme / documentation.
Anyway, my problem is that I keep getting this error:
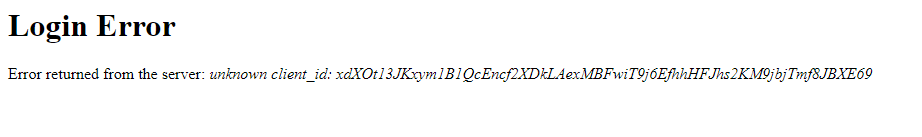
It turns out that the OwnCloud desktop client uses the redirect URI http://127.0.0.1 where Kopano Konnect only allows http://localhost when using the http protocol in combination with a native client. This is reflected in the Konnect logs:
time="2022-01-24T21:48:24Z" level=debug msg="parsing identifier registration conf from /etc/kopano/konnectd-identifier-registration.yaml"
time="2022-01-24T21:48:24Z" level=debug msg="registered client" application_type=web client_id=owncloud insecure=false origins="[https://andromeda.leeuwit.nl]" redirect_uris="[https://andromeda.leeuwit.nl/owncloud/apps/openidconnect/redirect]" trusted=true with_client_secret=true
time="2022-01-24T21:48:24Z" level=debug msg="registered client" application_type=web client_id=kopano-webapp insecure=false origins="[https://andromeda.leeuwit.nl]" redirect_uris="[https://andromeda.leeuwit.nl/kopanoid/signin/v1/identifier/oauth2/cb]" trusted=true with_client_secret=true
time="2022-01-24T21:48:24Z" level=warning msg="skipped registration of invalid client" application_type=native client_id=xdXOt13JKxym1B1QcEncf2XDkLAexMBFwiT9j6EfhhHFJhs2KM9jbjTmf8JBXE69 error="invalid redirect_uri http://127.0.0.1 = http host must be localhost when application_type is native" insecure=false origins="[]" redirect_uris="[http://127.0.0.1]" trusted=true with_client_secret=true
time="2022-01-24T21:48:24Z" level=debug msg="registered client" application_type=native client_id=e4rAsNUSIUs0lF4nbv9FmCeUkTlV9GdgTLDH1b5uie7syb90SzEVrbN7HIpmWJeD insecure=false origins="[]" redirect_uris="[oc://android.owncloud.com]" trusted=true with_client_secret=true
This is already fixed in Kopano Konnect, but that change is available since v0.34.0. I noticed that UCS uses version 0.33.8 of Konnect and simply repackages the upstream Konnect Docker image without any additions.
Is there an easy way to update the Docker image that UCS uses for the OpenID Connect Provider?
I already tried updating the AppCenter cache files by editing the DockerImage line to kopano/konnectd:0.34.0 in /var/cache/univention-appcenter/appcenter.software-univention.de/4.4/openid-connect-provider_20210616104237.ini. Running a univention-app upgrade openid-connect-provider afterwards does pull the new image, but that image is not used when creating the Docker container.
I also tried ucr set appcenter/apps/openid-connect-provider/image=kopano/konnectd:0.34.0, but that didn’t work either.
Any other suggestions to try?

