Dear Community,
after upgrading Nextcloud 21.0.9-0 to Nextcloud 22.2.7-0 Collabora is no longer working.
We cant access collabora anymore using our external URL (orange-dev.beispielurl.de).
If we use the internal FQDN Collabora is working (but only if we enable our VPN because the FQDN cant be access by public)
Hier das passende Ticket noch auf deutsch.
Our Setup
- root server with Proxmox VE 7 (all ports → OPNsense)
2.1 OPNsense Firewall (TCP 80, 443 → reverseProxy)
2.2 Debian 11 reverseProxy with NGINX and certbot (Domain orange-dev.beispielurl.de → webAppBei01.beispiel.ucs [10.220.0.17])
2.3 pdcBei.beispiel.ucs (primary UCS domain controller)
2.4 webAppBei01.beispiel.ucs (UCS Application Server with Nextcloud and Collabora Docker Container)
The following configuration is the last working one
- Nextcloud 21.0.9-0
- Collabora 21.11.2.4
- Collabora Nextcloud App 4.2.7
- UCS 5.0-1 errata 524 (at all UCS systems)
$ univention-app list nextcloud
nextcloud
Name: Nextcloud Hub
Versions:
20.0.9-0
20.0.10-0
21.0.3-0
21.0.4-0
21.0.5-0
21.0.7-0
21.0.9-0
Installed: webAppBei01.beispiel.ucs
22.2.7-0
23.0.4-0
23.0.5-0
$ univention-app list collabora
collabora
Name: Collabora Online Development Edition
Versions:
6.4.10.5
6.4.10.10
21.11.2.4
Installed: webAppBei01.beispiel.ucs
Nextcloud > settings > overview
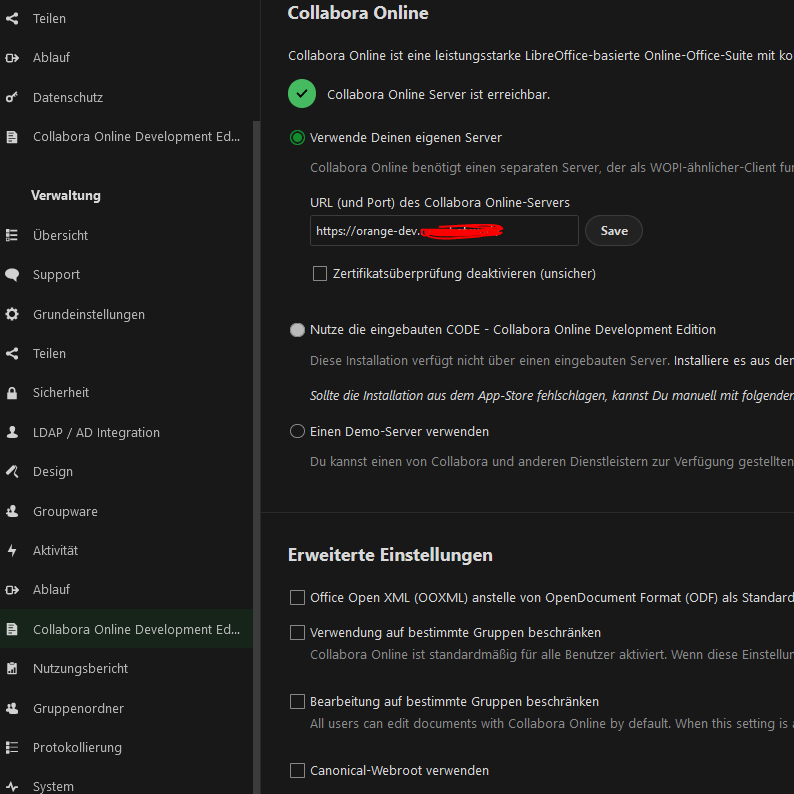
Nextcloud > settings > Collabora Online
Nextcloud > A well working test document
This is our reverseProxy Nginx configuration
server {
if ($host = orange-dev.beispielurl.de) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80;
listen [::]:80;
server_name orange-dev.beispielurl.de;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
listen [::]:443 ssl;
server_name orange-dev.beispielurl.de;
client_max_body_size 999M;
# Server SSL
ssl_certificate /etc/letsencrypt/live/orange-dev.beispielurl.de/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/orange-dev.beispielurl.de/privkey.pem; # managed by Certbot
# Globale Einstellungen
add_header Strict-Transport-Security "max-age=15768000;
includeSubDomains; preload;";
fastcgi_hide_header X-Powered-By;
proxy_read_timeout 180;
proxy_http_version 1.1;
proxy_pass_request_headers on;
proxy_pass_header Date;
proxy_pass_header Server;
proxy_pass_header Authorization;
proxy_buffering off;
proxy_set_header Connection "Keep-Alive";
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Accept-Encoding "";
more_set_input_headers 'Authorization: $http_authorization';
more_set_headers -s 401 'WWW-Authenticate: Basic realm="orange-dev.beispielurl.de"';
location / {
proxy_pass https://10.220.0.17/;
proxy_redirect https://10.220.0.17 https://orange-dev.beispielurl.de;
}
rewrite ^/$ /nextcloud/ last;
location = /.well-known/carddav {
return 301 $scheme://$host/nextcloud/remote.php/dav;
}
location = /.well-known/caldav {
return 301 $scheme://$host/nextcloud/remote.php/dav;
}
location /.well-known/acme-challenge {
}
location = /.well-known/webfinger {
return 301 $scheme://$host/nextcloud/index.php/.well-known/webfinger;
}
location = /.well-known/nodeinfo {
return 301 $scheme://$host/nextcloud/index.php/.well-known/nodeinfo;
}
# static files
location ^~ /browser {
proxy_pass https://10.220.0.17:9980;
proxy_set_header Host $http_host;
}
# WOPI discovery URL
location ^~ /hosting/discovery {
proxy_pass https://10.220.0.17:9980;
proxy_set_header Host $http_host;
}
# Capabilities
location ^~ /hosting/capabilities {
proxy_pass https://10.220.0.17:9980;
proxy_set_header Host $http_host;
}
# main websocket
location ~ ^/cool/(.*)/ws$ {
proxy_pass https://10.220.0.17:9980;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
proxy_set_header Host $http_host;
proxy_read_timeout 36000s;
}
# download, presentation and image upload
location ~ ^/(c|l)ool {
proxy_pass https://10.220.0.17:9980;
proxy_set_header Host $http_host;
}
# Admin Console websocket
location ^~ /cool/adminws {
proxy_pass https://10.220.0.17:9980;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
proxy_set_header Host $http_host;
proxy_read_timeout 36000s;
}
# redirect server error pages to the static page
error_page 403 /error403.html;
location = /error403.html {
root /var/www/error;
}
}
Up to this point everything is working well.
The following configuration is not working
- Nextcloud 22.2.7-0 (same Problem using version 23.0.4-0 and 23.0.5-0)
- Collabora 21.11.2.4
- Collabora Nextcloud App 4.2.7 (if it is NC 23.0.4-0 and 23.0.5-0 it is App Version 5.0.5 , we also tested App Version 5.0.4)
- UCS 5.0-1 errata 524 (at all UCS systems)
Content of /var/www/html/config/config.php inside Nextcloud docker container
<?php
$CONFIG = array (
'passwordsalt' => '..%passwordsalt%..',
'secret' => '..%secret%..',
'trusted_domains' =>
array (
0 => 'webAppBei01.beispiel.ucs',
1 => '10.220.0.17',
2 => 'orange-dev.beispielurl.de',
),
'datadirectory' => '/var/lib/univention-appcenter/apps/nextcloud/data/nextcloud-data',
'dbtype' => 'pgsql',
'version' => '22.2.7.1',
'overwrite.cli.url' => 'https://orange-dev.beispielurl.de/nextcloud',
'dbname' => 'nextcloud',
'dbhost' => '172.17.42.1:5432',
'dbport' => '',
'dbtableprefix' => 'oc_',
'dbuser' => 'nextcloud',
'dbpassword' => '..%dbpassword%..',
'installed' => true,
'instanceid' => 'ocx6tslabhwg',
'updatechecker' => false,
'upgrade.disable-web' => true,
'memcache.local' => '\\OC\\Memcache\\APCu',
'memcache.distributed' => '\\OC\\Memcache\\APCu',
'overwriteprotocol' => 'https',
'overwritewbroot' => '/nextcloud',
'htaccess.RewriteBase' => '/nextcloud',
'ldapProviderFactory' => 'OCA\\User_LDAP\\LDAPProviderFactory',
'default_phone_region' => 'DE',
'skeletondirectory' => '',
'trusted_proxies' =>
array (
0 => '172.17.42.1',
),
'maintenance' => false,
'loglevel' => 2,
);
Nextcloud > Settings > Overview
Nextcloud > Settings > Collabora Online
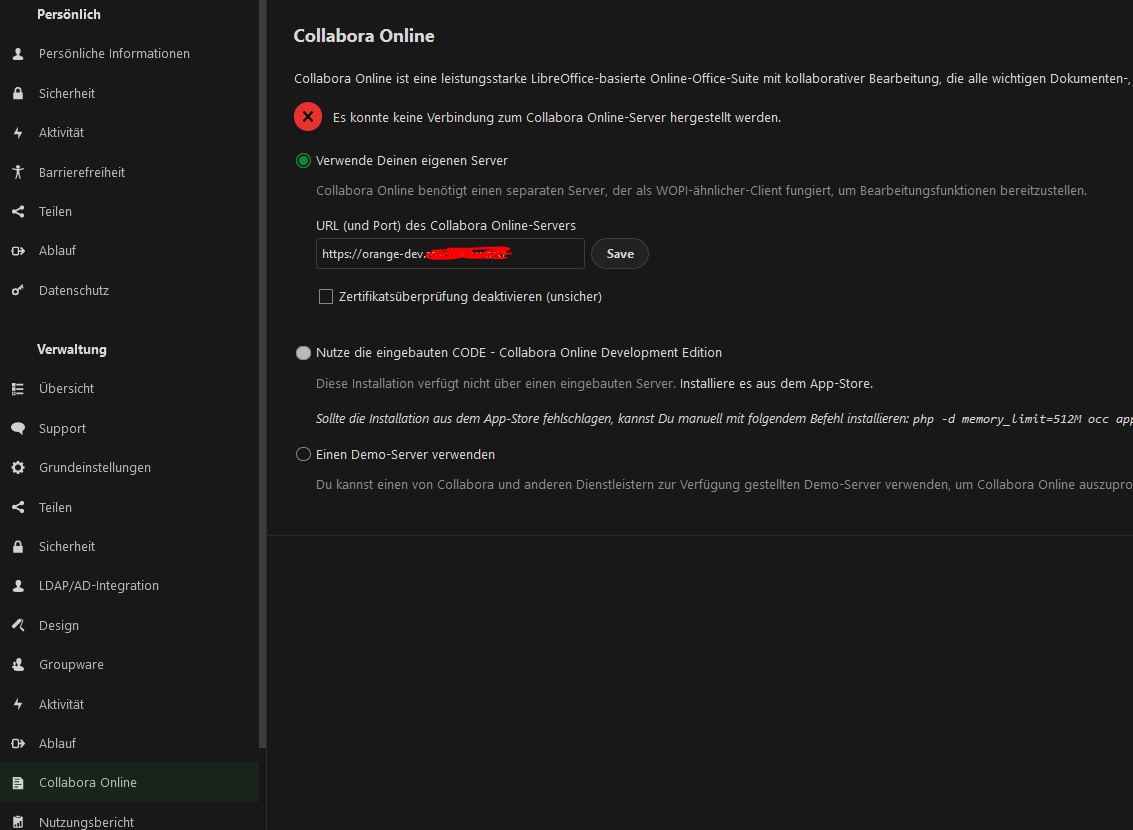
Nextcloud > A not working document (our main problem)
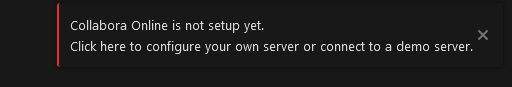
It feels like there is a new setting or a new value inside config.php file that we are missing. Something like “let external Host access me”.
Perhaps someone of you run into the same problem, or even better, got a solution for this?
We thank you for any idea or input you can give us.
Greetings
Migo