Starting with UCS 4.3, it’s possible to use Kerberos as authentication for SSO enabled services.
This means that users log in to a Windows machine with their domain account and are automatically signed in to the UMC and other configured service providers.
However, there are two settings in Windows that need to be changed for this to work. This can be achieved with a group policy object in Samba. Windows clients must be joined to the domain for this to work.
Note: Single sign-on won’t work if a HTTPS connection to ucs-sso.your-domain.tld is not possible, e.g. if the certificate is not trusted. How to import UCS root CA on Windows clients
Note: We will add the UCS identity provider to Windows’ trusted sites. These trusted sites are used by Chrome and Internet Explorer. The following has no effect on other browsers at the time of this writing, because they don’t utilize Windows trusted sites in the same way. Currently, it’s not possible to configure SSO for Edge.
Note: Make sure that SSO works in your environment before configuring this to avoid debugging in the wrong place.
Configure univention-negotiate
For the following to work, the UCR variable saml/idp/authsource has to be set to “univention-negotiate”:
ucr set saml/idp/authsource=univention-negotiate
Chrome, Internet Explorer
Create a group policy
Creating Windows group policies works the same in Samba as in a Windows AD domain.
Install the Remote Server Administration Tools (RSAT) on a Windows client in the domain and run the “Microsoft Group Policy Management Tool”.
The RSAT Tools are available for Windows 10 and Windows 7.
After the RSAT tools are installed, you need to activate the Group Policy Management Tools. Click the Start button and run Turn Windows features on or off. Browse to
Remote Server Administration Tools -> Feature Administration Tools -> Group Policy Management Tools
and activate the checkbox. Click OK.
Now, you can run Group Policy Management from the Start button.
In the Group Policy Management Tool, expand Forest:YourForestName, expand Domains, expand YourDomainName, and then click Group Policy Objects.
Click Action, and then click New.
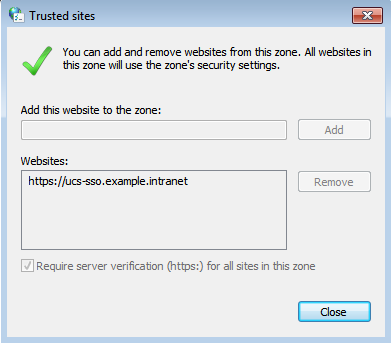
Add identity provider to trusted sites
Firstly, the UCS identity provider has to be added to Windows’ trusted sites.
Right click and choose “Edit” on your group policy. A hierachical structure of settings opens.
Browse to:
User Settings -> Policies -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page
Double-click on Site to Zone Assignment List, select Enable and click Show to edit the list.
Add the following to your list and click OK. example.intranet is our domain in this example.
| Value name | Value |
|---|---|
| https://ucs-sso.example.intranet | 2 |
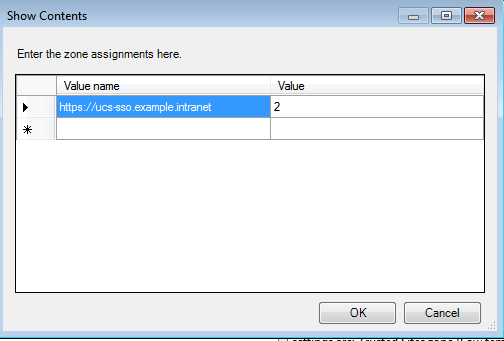
This method will grey out the assignment list on the Windows clients, so users can’t remove or add anything themselves.
Allow authentication with trusted sites
Now that we’ve added the UCS identity provider to trusted sites, we need to enable authentication for them.
Edit your group policy and browse to:
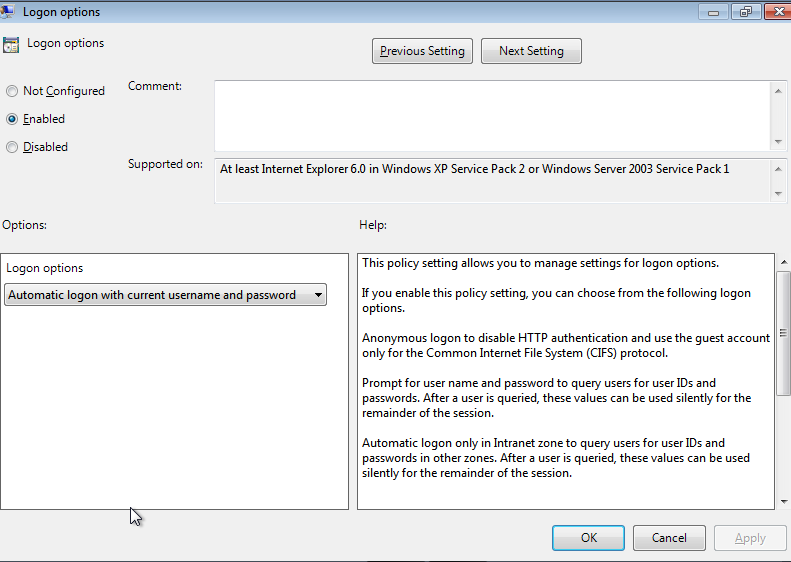
User Settings -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page -> Trusted sites zone
Double-click on Logon options, select Enable and choose Automatic Logon with current username and password in the drop-down menu in the Options area.
Click OK.
Link the GPO to your domain
To make sure that the GPO is applied, you have to link it to your desired domain or OU. Right-click on the domain or OU and select Link an Existing GPO. Choose your newly created GPO and click OK.
Firefox
As mentioned above, Firefox doesn’t utilize Windows trusted sites as Chrome and IE do. The configuration has to be applied in Firefox’ own configuration.
Open about:config in Firefox. You will be presented with a list of settings parameters and a search mask. Again, dc=example,dc=intranet is our LDAP base in this example. Use the mask to search for the following parameters and apply the accompanying value:
| Config parameter | Value |
|---|---|
| network.auth.use-sspi | true |
| network.negotiate-auth.trusted-uris | .example.intranet |
Logout
Once the user logs out on a web page configured for SSO (for example the UMC), single sign-on will not be automatically performed using the Kerberos login until the next time the user logs in using Kerberos. Users will simply be prompted for their credentials on e.g. the UMC, if they decide to login again without having logged out and in to Windows before.