Hi,
I’m getting following errors since errata 184 upgrade:
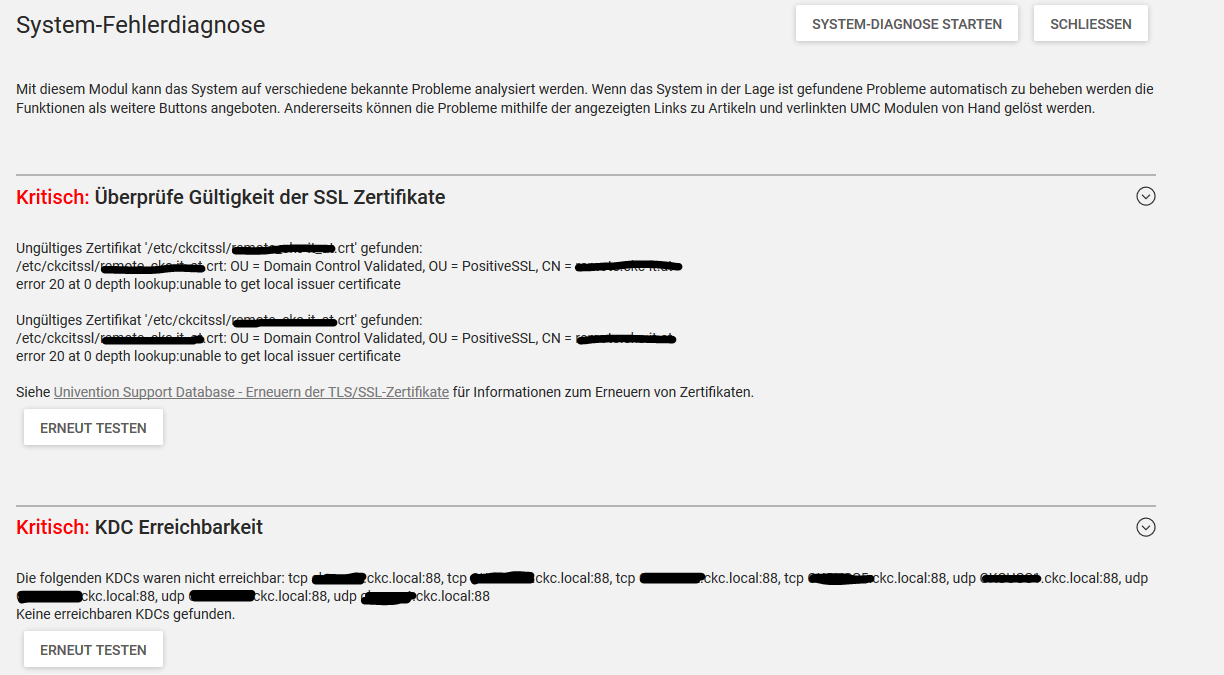
seems to be a problem with external cert (cert is valid till 2019)
any hints on this ?
rg
Christian
Hi,
I’m getting following errors since errata 184 upgrade:

seems to be a problem with external cert (cert is valid till 2019)
any hints on this ?
rg
Christian
Those checks were added via Errata 166, so the problems most probably were present before and are only detected know. The SSL check might be a false positive, though. “error 20 at 0 depth lookup:unable to get local issuer certificate” is an “openssl verify” error message, that basically says “I can’t verify this because I cannot find the matching root/intermediate certificate(s)”.
Regarding the KDC check: I’d check if the mentioned DNS SRV records are still valid. If not, they should be updated / corrected via DNS module. If they are still valid, I’d go and check why they cannot be reached.
Hi,
thanks for your informtaion - so SSL check I’ll have to ignore this error as it seems to rely on the external root CA and I tested on a testinstallation with letsencrypt app from appcenter and getting the same error there !
But the error with KDC is interresting as all DNS records are there and on cmd line i’m able to connetct to port 88 on all DC’s and the error is only given on the Master Server - all Backup Servers run teh chekc without error
rg
Christian
From the source code of the KDC check module:
# This checks for the reachability of KDCs by sending a AS-REQ per TCP and UDP.
# The AS-REQ is send with the fake user `kdc-reachability-check`. The KDCs will
# respond in several ways: either with an KRB-ERROR (PREAUTH_REQUIRED,
# PRINCIPAL_UNKNOWN or RESPONSE_TO_BIG) or a AS-REP with an anonymous ticket.
#
# If we do not receive one of the above, the connection is not accepted, the
# socket is closed or an operation times out, we can assume, that the KDCs is
# not reachable.
#
# This check will test the KDCs as specified in UCR `kerberos/kdc` with TCP and
# UDP on port 88. If `kerberos/defaults/dns_lookup_kdc` is set, KDC discovery as
# specified in section `7.2.3. KDC Discovery on IP Networks` [1] will be used.
# In this case the ports as specified in the SRV records are used.
#
# This implements a minimal number of packages as defined in [1] and does not
# rely on python-kerberos or python-krb5, as those are too high level and
# outdated.
#
# Reachability checks of kpasswd servers are not implemented, as those are a
# separate protocol. See [2].
#
# [1]: https://tools.ietf.org/html/rfc4120
# [2]: https://tools.ietf.org/html/rfc3244
Is the UCR variable kerberos/defaults/dns_lookup_kdc different set on the systems?
no the settings are the same (unset) on all servers
if i run the script on cli manually it responds correctly on the master too 
rg
Christian