vCenter version: VMware-VCSA-all-6.7.0-14070457
UCS version: 4.4-1 errata196 (Blumenthal)
Our vCenter Server is unable to bind to UCS through ldap.
My Process:
Configure SSO through “Active Directory Domain”:
- In vCenter: Administration > SSO > Configuration > Active Directory Domain
- Selected “Join AD”
- Join to the domain, reboot vCenter (Note: I can also replicate this through vCenter CLI commands)
- after reboot, I go to Identity Source > Add Identity source
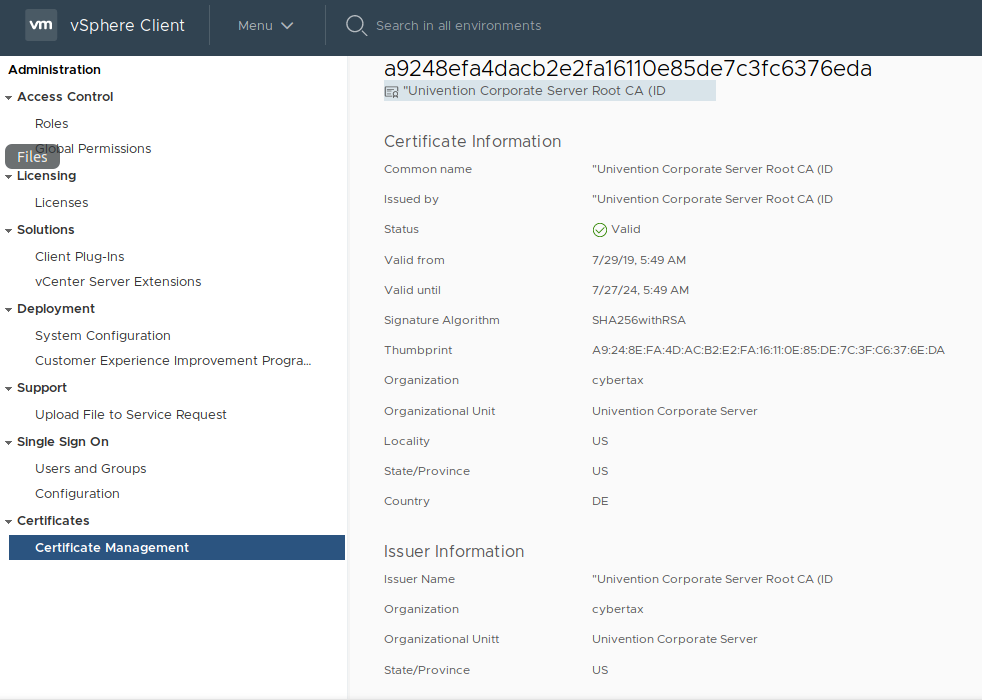
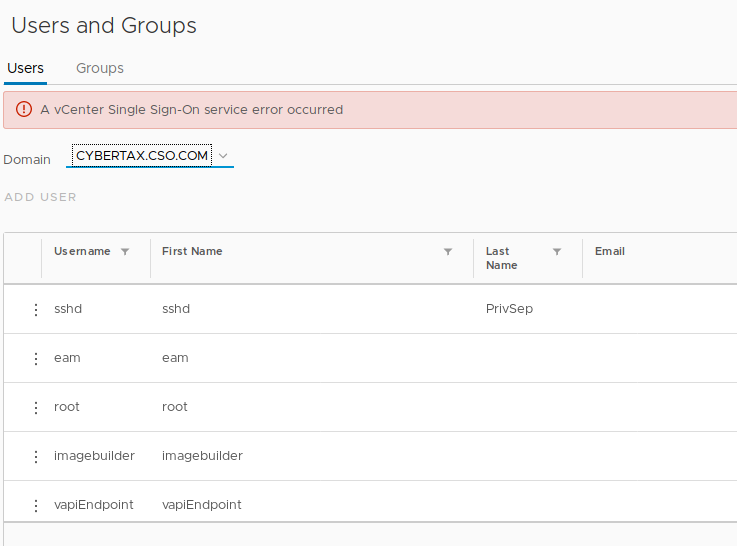
- PROBLEM: When going to Single Sign On > Users and Groups, and select the newly added domain, I receive “A vCenter Single Sign-On service error occured”
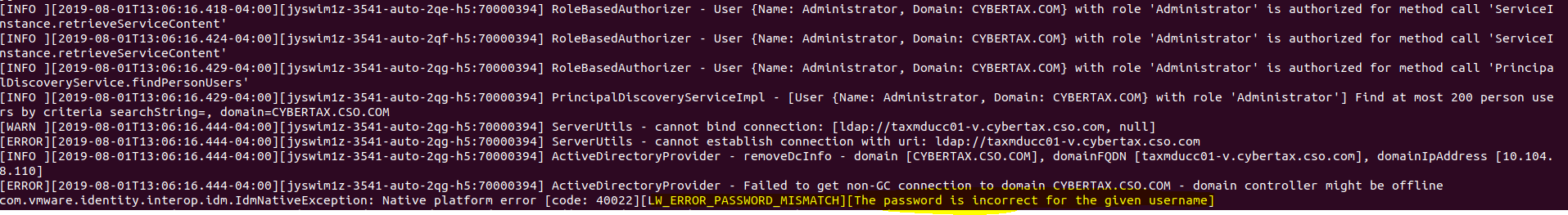
Upon further inspection of the the /var/log/vmware/sso/ssoAdminServer.log. I see the following every time I try to search UCS:
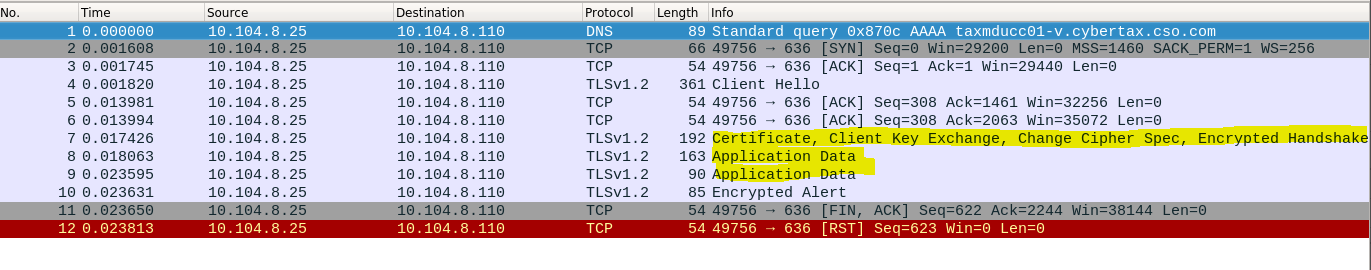
[WARN ][2019-07-30T16:55:40.650-04:00][jyqan3yc-174-auto-4x-h5:70000052] ServerUtils - cannot bind connection: [ldap://taxmducc01-v.cybertax.cso.com, null]
[ERROR][2019-07-30T16:55:40.650-04:00][jyqan3yc-174-auto-4x-h5:70000052] ServerUtils - cannot establish connection with uri: ldap://taxmducc01-v.cybertax.cso.com
[INFO ][2019-07-30T16:55:40.650-04:00][jyqan3yc-174-auto-4x-h5:70000052] ActiveDirectoryProvider - removeDcInfo - domain [CYBERTAX.CSO. COM], domainFQDN [taxmducc01-v.cybertax.cso. com], domainIpAddress [10.104.8.110]
[ERROR][2019-07-30T16:55:40.650-04:00][jyqan3yc-174-auto-4x-h5:70000052] ActiveDirectoryProvider - Failed to get non-GC connection to domain CYBERTAX.CSO. COM - domain controller might be offline
com.vmware.identity.interop.idm.IdmNativeException: Native platform error [code: 40022][LW_ERROR_PASSWORD_MISMATCH][The password is incorrect for the given username]
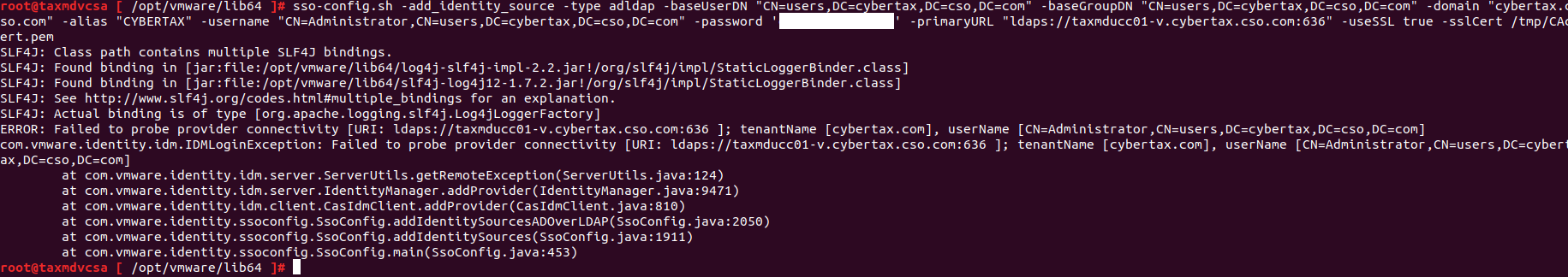
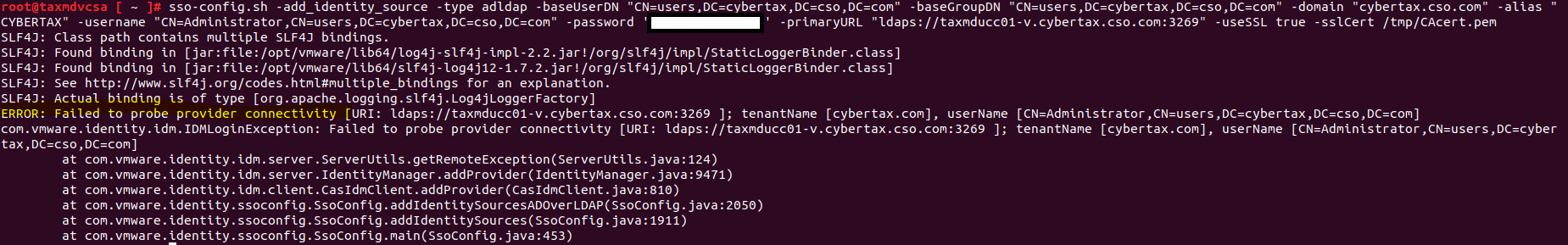
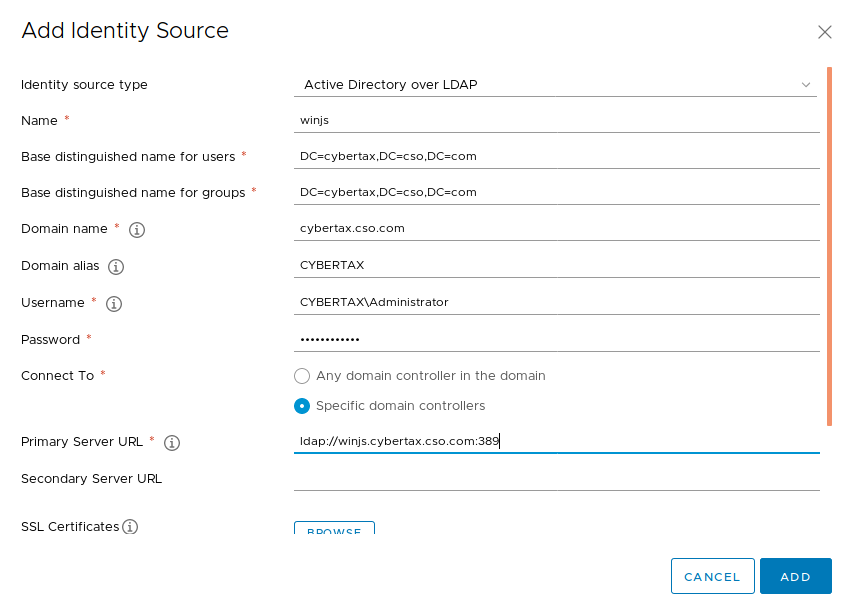
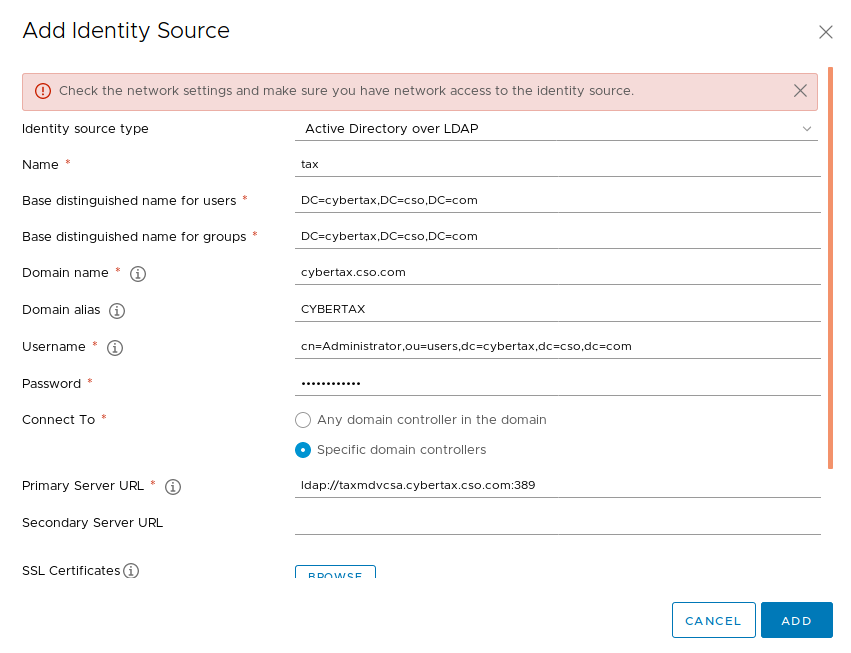
I also tried to integrate directly with the “Active Directory over LDAP” function. However every time I try to connect to UCS I keep getting “Check the network settings and make sure you have network access to the identity source”, not sure why as the administrator username and password worked through AD join through the web and cli,
-
Note: I tried changing the user: to cn=Administrator,cn=users,dc=cybertax,dc=cso,dc=com. As well as using the NETBIOS name CYBERTAX\Administrator. Nothing worked.
-
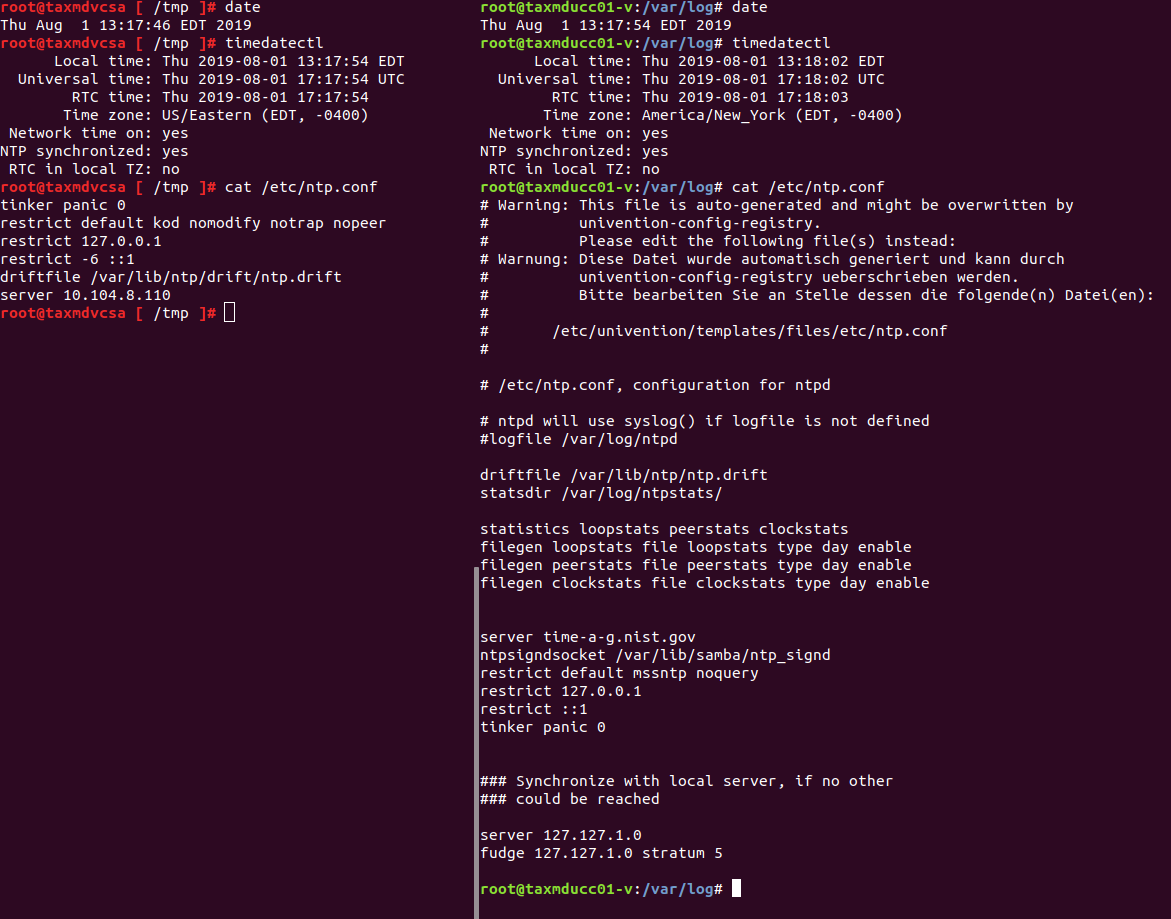
Trouble shooting: I tried deploying a new vCenter (for testing purposes) and integrating to a Windows Domain. it worked with no problems.
Not sure what I am missing here. Any ideas?