Yes, the vhost config exists, this is the /etc/apache2/sites-enabled/univention-saml.conf
# Warning: This file is auto-generated and might be overwritten by
# univention-config-registry.
# Please edit the following file(s) instead:
# Warnung: Diese Datei wurde automatisch generiert und kann durch
# univention-config-registry ueberschrieben werden.
# Bitte bearbeiten Sie an Stelle dessen die folgende(n) Datei(en):
#
# /etc/univention/templates/files/etc/apache2/sites-available/univention-saml.conf
#
Alias /simplesamlphp/saml2/idp/certificate /etc/simplesamlphp/ucs-sso.my-domain-idp-certificate.crt
<Directory "/etc/simplesamlphp">
<Files "ucs-sso.my-domain-idp-certificate.crt">
Require all granted
</Files>
</Directory>
Alias /simplesamlphp /usr/share/simplesamlphp/www
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteRule ^/?simplesamlphp/(.*) https://%{SERVER_NAME}/simplesamlphp/$1 [R,L]
<Directory /usr/share/simplesamlphp/www/>
<FilesMatch ".+\.ph(p[345]?|t|tml)$">
SetHandler php-cgi
</FilesMatch>
Action php-cgi /saml-bin/php-cgi
Order allow,deny
Allow from all
</Directory>
<Directory /var/www/saml/>
Options -Indexes
</Directory>
<IfModule mod_ssl.c>
<VirtualHost *:443>
IncludeOptional /etc/apache2/sso-vhost.conf.d/*.conf
SSLEngine on
SSLProxyEngine on
ServerName ucs-sso.my-domain
SSLCertificateFile /etc/univention/letsencrypt/signed_chain.crt
SSLCertificateKeyFile /etc/univention/letsencrypt/domain.key
SSLCACertificateFile /etc/univention/ssl/ucsCA/CAcert.pem
SSLCertificateChainFile /etc/univention/letsencrypt/intermediate.pem
DocumentRoot /var/www/
RedirectMatch ^/$ /simplesamlphp/
ScriptAlias /saml-bin /var/www/saml
SuexecUserGroup samlcgi samlcgi
RewriteEngine on
RewriteCond %{HTTP:Authorization} !^$
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization},L]
Include /etc/apache2/sites-available/univention-proxy.conf
</VirtualHost>
<VirtualHost *:80>
IncludeOptional /etc/apache2/sso-vhost.conf.d/*.conf
ServerName ucs-sso.my-domain
DocumentRoot /var/www/
RedirectMatch ^/$ /simplesamlphp/
ScriptAlias /saml-bin /var/www/saml
SuexecUserGroup samlcgi samlcgi
RewriteEngine on
RewriteCond %{HTTP:Authorization} !^$
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization},L]
Include /etc/apache2/sites-available/univention-proxy.conf
</VirtualHost>
</IfModule>
And /etc/apache2/sso-vhost.conf.d/openid-connect-provider.conf is
#####################################################################
# generated by openid-connect-provider app join script, do not edit manually #
#####################################################################
# Kopano Konnect OIDC
ProxyPass /.well-known/openid-configuration http://localhost:8777/.well-known/openid-configuration retry=0
ProxyPass /konnect/v1/jwks.json http://localhost:8777/konnect/v1/jwks.json retry=0
ProxyPassReverse /konnect/v1/jwks.json http://localhost:8777/konnect/v1/jwks.json
ProxyPass /konnect/v1/token http://localhost:8777/konnect/v1/token retry=0
ProxyPassReverse /konnect/v1/token http://localhost:8777/konnect/v1/token
ProxyPass /konnect/v1/userinfo http://localhost:8777/konnect/v1/userinfo retry=0
ProxyPassReverse /konnect/v1/userinfo http://localhost:8777/konnect/v1/userinfo
ProxyPass /konnect/v1/static http://localhost:8777/konnect/v1/static retry=0
ProxyPassReverse /konnect/v1/static http://localhost:8777/konnect/v1/static
ProxyPass /konnect/v1/session http://localhost:8777/konnect/v1/session retry=0
ProxyPassReverse /konnect/v1/session http://localhost:8777/konnect/v1/session
ProxyPass /konnect/v1/register http://localhost:8777/konnect/v1/register retry=0
ProxyPassReverse /konnect/v1/register http://localhost:8777/konnect/v1/register
# Kopano Konnect login area
ProxyPass /signin/ http://localhost:8777/signin/ retry=0
ProxyPassReverse /signin/ http://localhost:8777/signin/
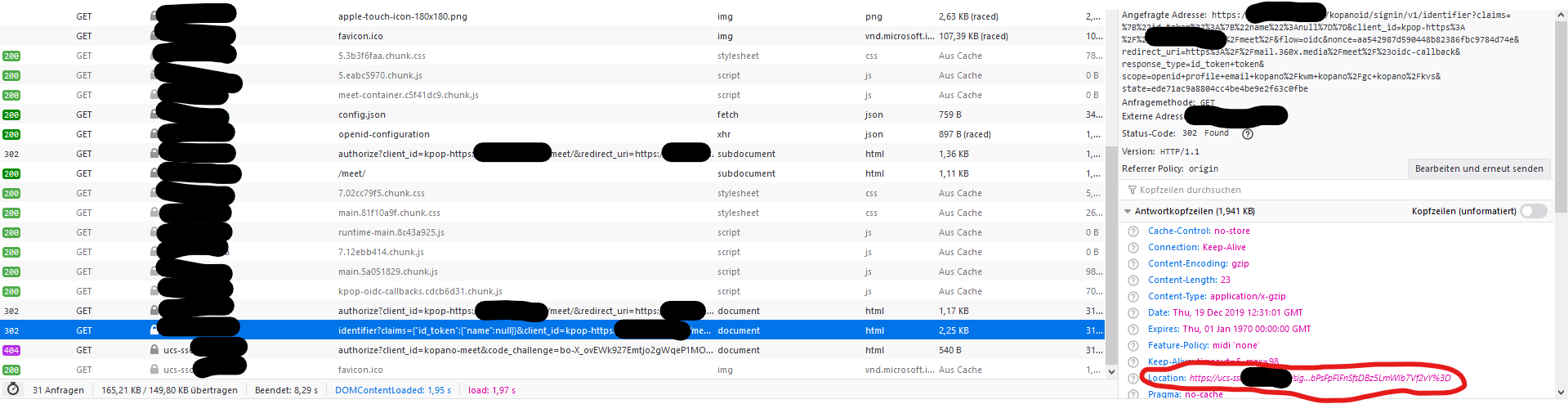
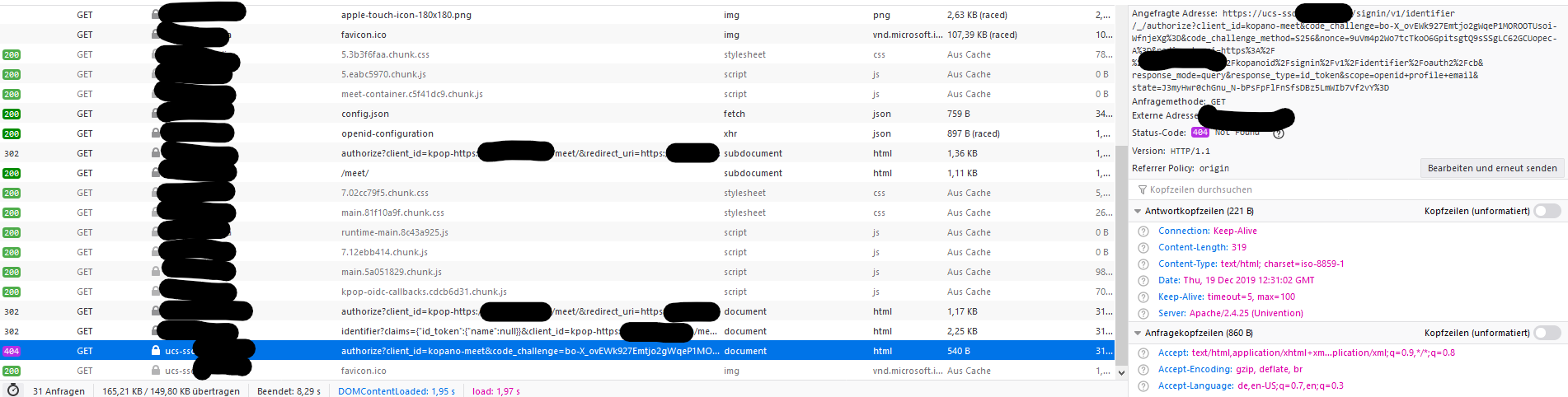
if I try to curl http://localhost:8777/signin/v1/identifier/_/authorize in the command line I get an error 400. So in general it works. I can also access https://ucs-sso.my-domain/kopanoid/signin/v1/identifier/_/authorize from the browser. But due to some reason kopano meet tries to get https://ucs-sso.my-domain/signin/v1/identifier/_/authorize which is not working after the change of the cert and adding ucs-sso sub domain to LE.