Hello,
We are facing an issue with a univention mail server and an Active Directory 2003 Integration. The problem starts with the error:
root@ucs:/var/log/univention# univention-adsearch cn=ucs-lda
kdestroy: krb5_cc_destroy: Did not find a plugin for ccache_ops
kinit: Password incorrect
Traceback (most recent call last):
File "/usr/sbin/univention-adsearch", line 163, in <module>
get_kerberos_ticket()
File "/usr/sbin/univention-adsearch", line 156, in get_kerberos_ticket
raise kerberosAuthenticationFailed('The following command failed: "%s"' % string.join(cmd_block))
__main__.kerberosAuthenticationFailed: The following command failed: "kinit --no-addresses --password-file=/etc/machine.secret ucs-ldap$"
--- connect failed, failure was: ---
Traceback (most recent call last):
File "/usr/share/pyshared/univention/connector/ad/main.py", line 303, in main
connect()
File "/usr/share/pyshared/univention/connector/ad/main.py", line 191, in connect
baseConfig['%s/ad/listener/dir' % CONFIGBASENAME]
File "/usr/lib/pymodules/python2.7/univention/connector/ad/__init__.py", line 839, in __init__
self.open_ad()
File "/usr/lib/pymodules/python2.7/univention/connector/ad/__init__.py", line 1038, in open_ad
self.get_kerberos_ticket()
File "/usr/lib/pymodules/python2.7/univention/connector/ad/__init__.py", line 1016, in get_kerberos_ticket
raise kerberosAuthenticationFailed('The following command failed: "%s" (%s): %s' % (string.join(cmd_block), p1.returncode, stdout))
kerberosAuthenticationFailed: The following command failed: "kinit --no-addresses --password-file=/etc/machine.secret ucs-ldap$" (1): kinit: Password incorrect
Jul 4 13:40:01 ucs-ldap CRON[18687]: pam_unix(cron:session): session opened for user root by (uid=0)
Jul 4 13:40:01 ucs-ldap CRON[18689]: pam_unix(cron:session): session opened for user root by (uid=0)
Jul 4 13:40:01 ucs-ldap CRON[18688]: pam_unix(cron:session): session opened for user root by (uid=0)
Jul 4 13:40:01 ucs-ldap ldapsearch: DIGEST-MD5 common mech free
Jul 4 13:40:01 ucs-ldap ldapsearch: DIGEST-MD5 common mech free
Jul 4 13:40:01 ucs-ldap ldapsearch: DIGEST-MD5 common mech free
Jul 4 13:40:01 ucs-ldap CRON[18688]: pam_env(cron:session): Unrecognized Option: XDG_DATA_DIRS=/usr/share:/usr/share/univention-kde-profiles/default/.local/share#012 - ignoring line
Jul 4 13:40:01 ucs-ldap CRON[18688]: pam_env(cron:session): Unrecognized Option: XDG_CONFIG_DIRS=:/usr/share/univention-kde-profiles/default/.config:/etc/xdg/#012 - ignoring line
Jul 4 13:40:01 ucs-ldap CRON[18688]: pam_env(cron:session): Unrecognized Option: KDEDIRS=/usr/share/univention-kde-profiles/default/.kde#012 - ignoring line
Jul 4 13:40:01 ucs-ldap CRON[18687]: pam_env(cron:session): Unrecognized Option: XDG_DATA_DIRS=/usr/share:/usr/share/univention-kde-profiles/default/.local/share#012 - ignoring line
Jul 4 13:40:01 ucs-ldap CRON[18687]: pam_env(cron:session): Unrecognized Option: XDG_CONFIG_DIRS=:/usr/share/univention-kde-profiles/default/.config:/etc/xdg/#012 - ignoring line
Jul 4 13:40:01 ucs-ldap CRON[18687]: pam_env(cron:session): Unrecognized Option: KDEDIRS=/usr/share/univention-kde-profiles/default/.kde#012 - ignoring line
Jul 4 13:40:01 ucs-ldap CRON[18689]: pam_env(cron:session): Unrecognized Option: XDG_DATA_DIRS=/usr/share:/usr/share/univention-kde-profiles/default/.local/share#012 - ignoring line
Jul 4 13:40:01 ucs-ldap CRON[18689]: pam_env(cron:session): Unrecognized Option: XDG_CONFIG_DIRS=:/usr/share/univention-kde-profiles/default/.config:/etc/xdg/#012 - ignoring line
Jul 4 13:40:01 ucs-ldap CRON[18689]: pam_env(cron:session): Unrecognized Option: KDEDIRS=/usr/share/univention-kde-profiles/default/.kde#012 - ignoring line
Jul 4 13:40:01 ucs-ldap CRON[18688]: pam_unix(cron:session): session closed for user root
Jul 4 13:40:01 ucs-ldap CRON[18687]: pam_unix(cron:session): session closed for user root
Jul 4 13:40:01 ucs-ldap CRON[18689]: pam_unix(cron:session): session closed for user root
Jul 4 13:41:26 ucs-ldap nscd: nss_ldap: failed to bind to LDAP server ldap://ucs-ldap.DOMAIN.DOM:7389: Invalid credentials
Jul 4 13:41:26 ucs-ldap nscd: nss_ldap: reconnecting to LDAP server...
Jul 4 13:41:26 ucs-ldap nscd: nss_ldap: failed to bind to LDAP server ldap://ucs-ldap.DOMAIN.DOM:7389: Invalid credentials
Jul 4 13:41:26 ucs-ldap nscd: nss_ldap: reconnecting to LDAP server (sleeping 1 seconds)...
Jul 4 13:41:27 ucs-ldap nscd: nss_ldap: failed to bind to LDAP server ldap://ucs-ldap.DOMAIN.DOM:7389: Invalid credentials
Jul 4 13:41:27 ucs-ldap nscd: nss_ldap: could not search LDAP server - Server is unavailable
Jul 4 13:41:27 ucs-ldap python2.7: pam_unix(univention-management-console:auth): check pass; user unknown
Jul 4 13:41:27 ucs-ldap python2.7: pam_unix(univention-management-console:auth): authentication failure; logname= uid=0 euid=0 tty= ruser= rhost=
Jul 4 13:41:27 ucs-ldap python2.7: pam_krb5(univention-management-console:auth): user administrator authenticated as administrator@DOMAIN.DOM
Jul 4 13:41:27 ucs-ldap python2.7: pam_unix(univention-management-console:account): could not identify user (from getpwnam(administrator))
We have checked the configuration file /etc/machine.secret and the AD user who performs the AD Queries and the password doesn’t match. When we fix the issue the sync starts and the AD Connection works based on the logs but then we have authentication error on Roundcube webmail and email access via outlook with all users to authenticate we get authentication error message.
As a workaround we would like to bypass the AD passwords and change them somehow via the UCS management console. The problem is the UCS doesn’t allow this action because of the AD Integration.
Is there any way to bypass this issue until we replace the mail server? Unfortunately there is no window for tests/interruptions!
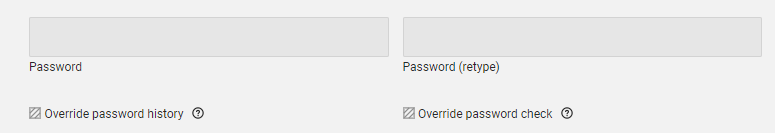
Thanks in advance,
George

 I really don’t know what to do
I really don’t know what to do